A Victim of the Akira Ransomware
Recently we helped a victim recover from a full ransomware attack from the threat actor Akira. The attack is one of many that is targeting vulnerable VPN solutions to gain initial access.
Initial Access
The threat actor used valid credentials to access the Customers Cisco VPN solution. Likely obtained via a password spray attack. On august 22nd Bleeping computer posted an article about how Akira targets Cisco VPN solutions, linking this attack to more ransomware incidents from the same threat actor.
Persistence
Persistence was established via installation of AnyDesk. The logs generated by this software reveals that the threat actor used the backdoor several times throughout the attack.
Command and Control
Two very similar binaries were found that appeared to be used to command and control the affected servers. Both binaries made connections to the domain samabasa[.]us via HTTPS and were placed inside the ProgramData directory on the C-Drive.
- 00633de9f5.exe (SHA256=739705079BE36C8125D0E5B136E9220944A8EA5D563C345FBC8E1D7FDE9A256F)
- e6b671d04d.exe (SHA256=2A81947F32BA46DBCBE9D867C97C6654F325EB61B5F87B33B31E89E6B15574DE)
Network Enumeration
Advanced IP scanner was used for network enumeration.
Akira Ransomware
The Akira ransomware utilizes a combination of asymmetric and symmetric encryption with a hardcoded asymmetric public key. Before any files are encrypted, the Windows Shadow Volume Copies are removed. Shadow copies would otherwise be a method for the victim to recover deleted files. The ransomware targets all files except a few whitelisted extensions (.exe, .dll, .sys, .msi and .lnk). In this incident the ransomware was executed both by targeting specific systems and using a list of target systems placed in a file called “file.txt”, using the “-remote” parameter. The ransomware also had a “-local” parameter to encrypt the system that it’s executed on, this was not used during the attack.
win_locker.exe -p \FQDNC$ win_locker.exe -remote -s=file.txt
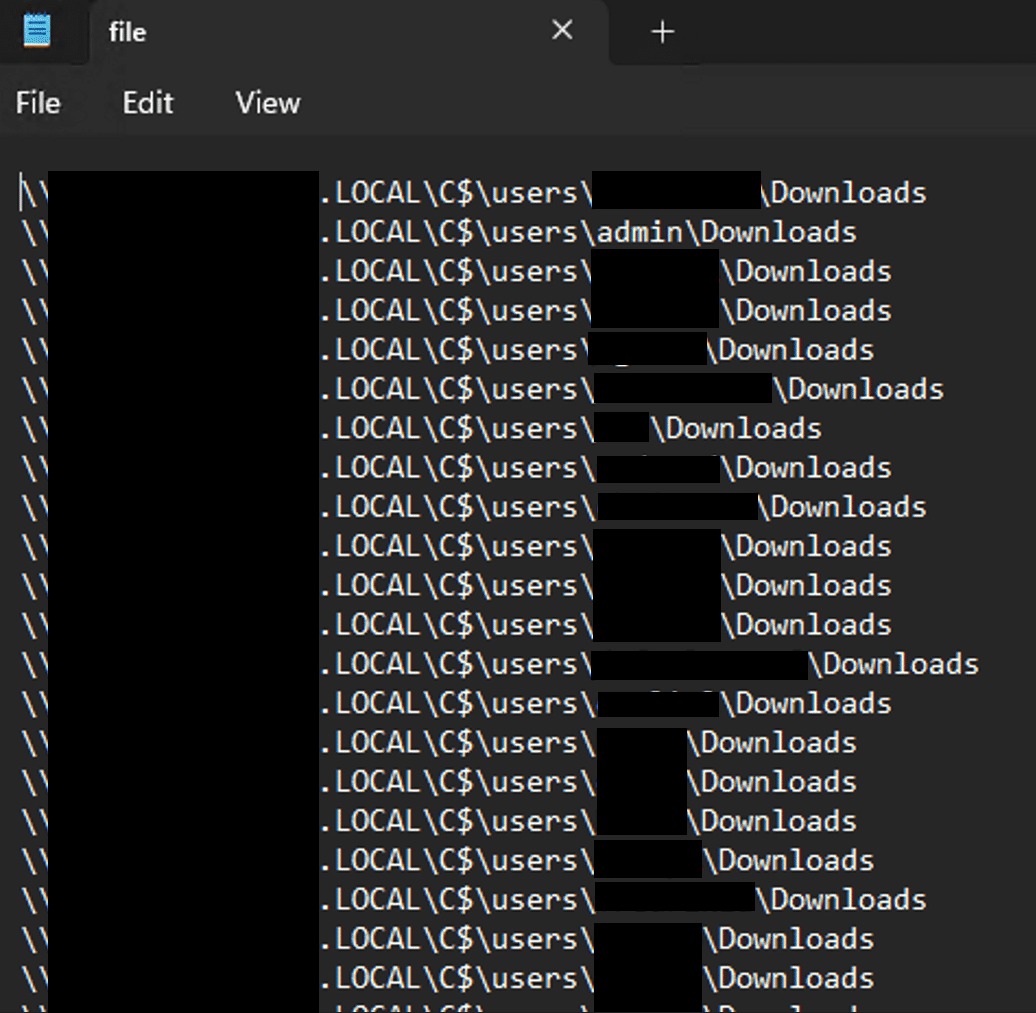
The threat actor left “file.txt” on the system, which allowed us to investigate its contents. Figure 1 shows a screenshot of the first entries. The file had in total >1500 entries targeting directories across the victim network.
Extortion
On the Akira darknet website a news article is posted a few days after the ransomware attack, naming the victim company. At the same time, an email to ~15 recipients is sent of from a gmail address. It’s worth noting that the recipient list does not only include mailboxes at the victim, it also included several email addresses of business partners. A screenshot of the full email is presented in Figure 2.

Lessons Learned
There are no shortcuts to have a secure environment. But the victim likely would have had a much lesser impact from the ransomware attack if the following activities had been made:
- Make sure the VPN solution is fully patched and enable MFA.
- Evaluate detection and response capabilities – Does the existing solution block and detect modern threats? Are the alerts monitored?
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.
