Detection Engineering – A Strategic Imperative

Why Have Detection Engineering?
Detection Engineering is a practice within a Security Operation Center (SOC) that ensures the SOC stays ahead of the threat actors.
This is accomplished by evaluating which security technologies are capable of detecting out of the box, enhancing the product’s capabilities with custom rulesets, and tuning these to precise detections.
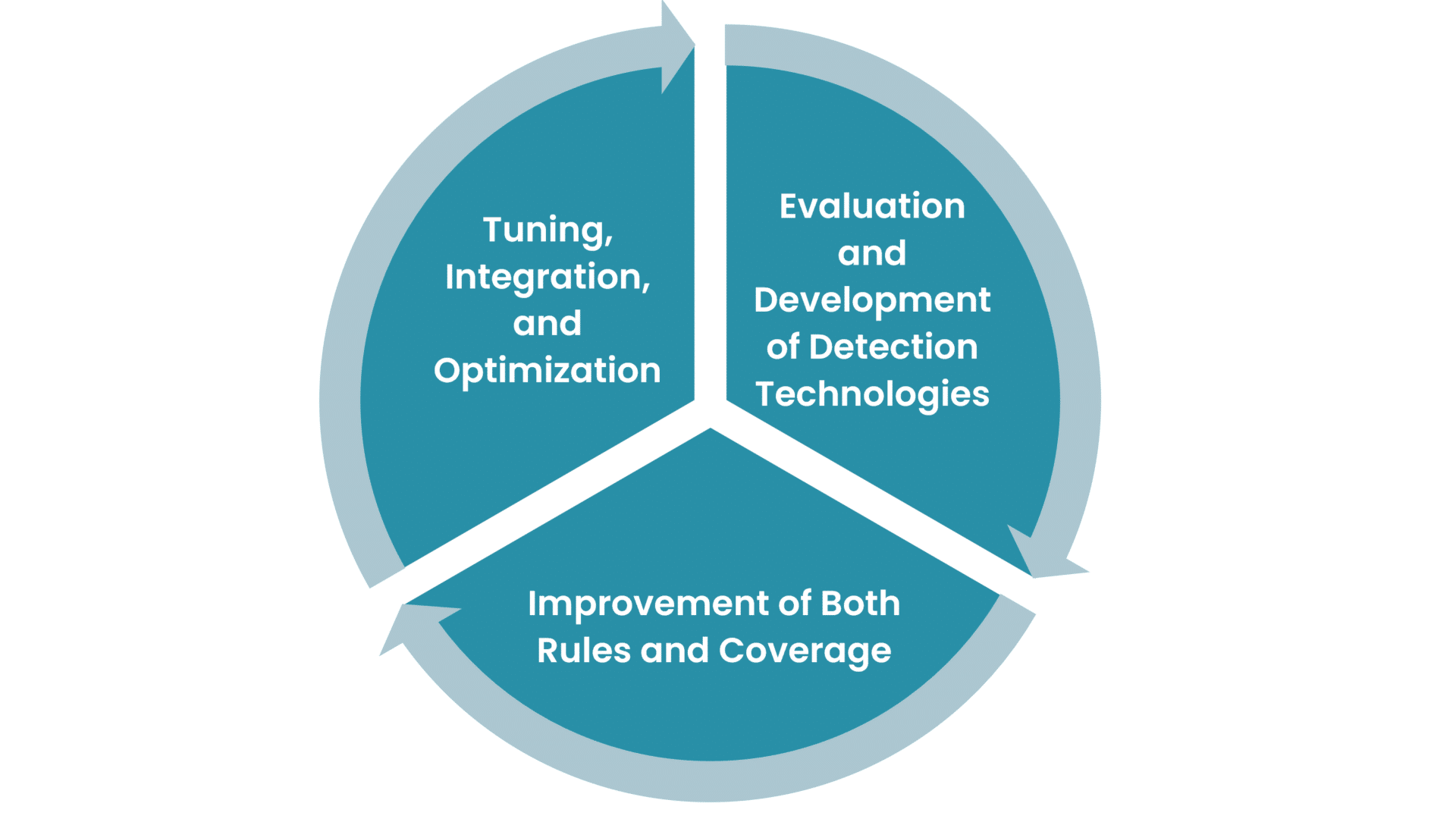
What Is Detection Engineering?
In cybersecurity’s dynamic realm, detection engineering is a cornerstone discipline for a functional SOC or MDR service. This guide explores detection engineering’s complexities and uncovers its key principles, advanced tactics, and real-world applications. It emphasizes ongoing progress and adjustment to ever-changing cyber threats. We’ll show how committed, detection engineering teamwork leads to developing, fine-tuning, and creating critical detection rules to protect digital ecosystems.
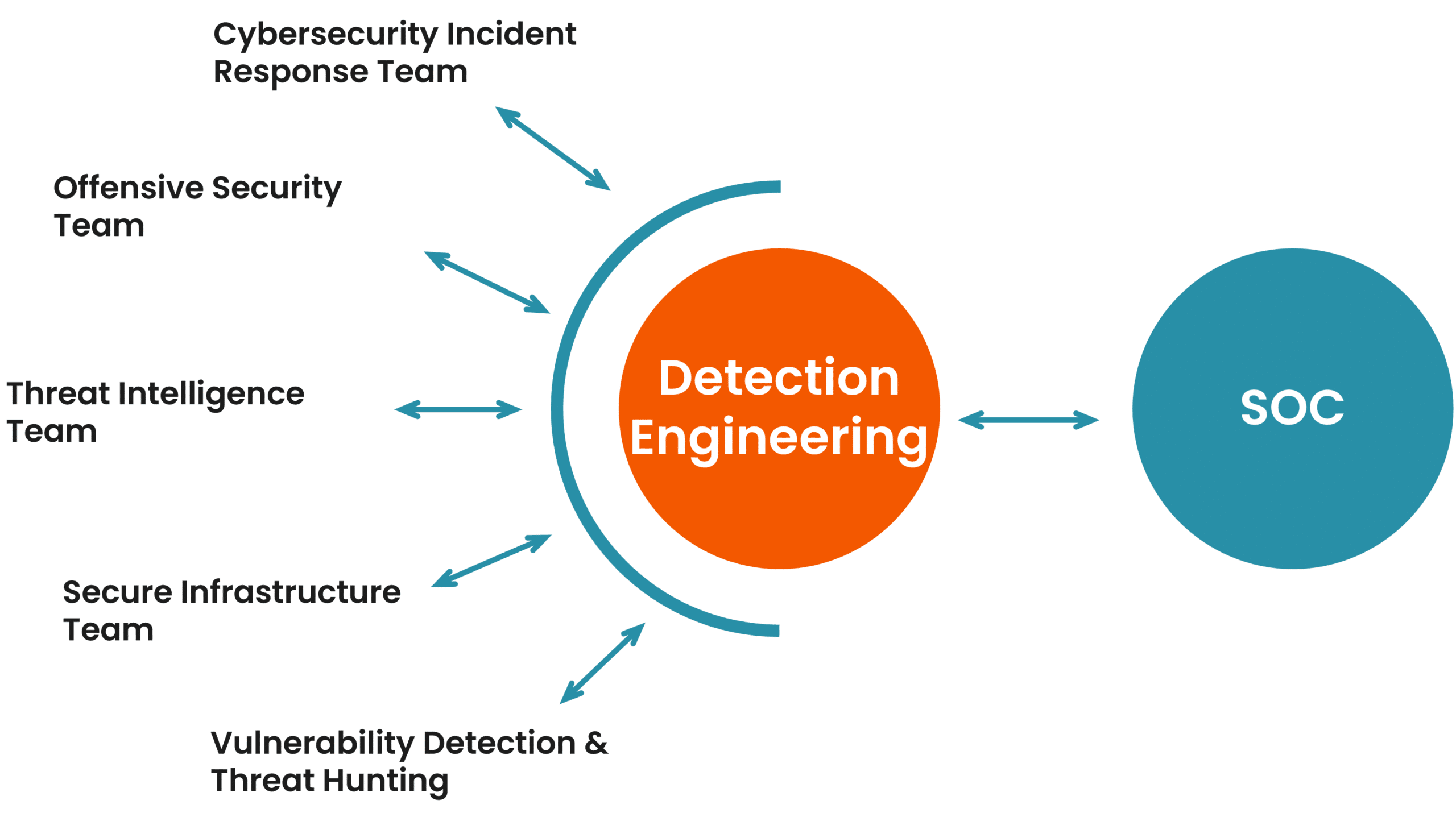
How Does Detection Engineering Find Threat Actors?
Threat actors use the same tools as the rest of us.
Often, they also use detection tools and practice bypassing detection with those tools.
Rulesets relevant to the customer environment, as defined by the toolset providers form the base of the security monitoring platform. Additionally, Truesec establishes its layer of rulesets and tuning as the service is deployed. Truesec’s ever-evolving experience in threat hunting, threat intelligence, and incident response across the client landscape and the customer’s specific situation informs these proprietary and more granular rulesets. These comprehensive sets of triggers provide sensitive and up-to-date protection against even the latest identified threats.
Custom rules matter because they’re something threat actors can’t prepare to avoid. They lack access to Truesec’s global detection rules. This prevents them from developing special tools or practicing ways to evade detection.
“Custom rules matter because they’re something threat actors can’t prepare to avoid.”
The Essence of Detection Engineering
At its core, detection engineering is about crafting a robust framework that can identify and mitigate cyber threats effectively. It’s not about the mere selection of tools. Instead, the focus is on creating a value-driven detection model built on a deep understanding of the threat landscape. Additionally, you should continuously refine it based on knowledge from incident response operations, threat intelligence units, SOC teams, and beyond.
Truesec’s approach, which emphasizes developing and managing detection rules independent of the tools used, is a prime example of this philosophy in action.
Important in detection engineering:
- A process to evaluate the tools on the market. The market changes quickly, and to be relevant, organizations must use the best tools because threat actors use their best tools.
- Enhance the detection capabilities with custom detections.
- Ensure detection coverage across the entire organization’s infrastructure.
- Continuous fine tuning to both increase the sensitivity and minimize unnecessary false positives.
Operationalizing Detection With Precision and Agility
Integrating detection engineering into the daily operations of a SOC involves more than just technical implementation. Rather, it’s about embedding a culture of vigilance and adaptability. Truesec incorporates rules maintenance into daily workflows. Our MISP platform and curated intelligence automate this process. This approach emphasizes blending technology with human expertise seamlessly and also involves behavior-based detection rules. Although these rules may trigger many alerts, they highlight the need for careful tuning. Truesec tailors the rules to fit a customer’s unique environment through tuning. This customization boosts both efficiency and relevance.
Working with detection engineering isn’t something you do once a year to tune your rules. It must be an integrated part of the day-to-day work in the entire SOC.
You must:
- Have guidelines for seamlessly integrating detection systems into existing infrastructures.
- Leverage automation to enhance detection capabilities, including MISP platforms.
- Nurture a culture of skill development and teamwork. This ensures continuous learning and collaboration, drawing on knowledge from incident response, threat intelligence, SOC teams, and more for rule refinement and innovation.
Challenges and Strategies for Effective Detection
Navigating the challenges in detection engineering requires a balanced approach. High alert volumes and the need for precise rule tuning are common hurdles. However, these can be effectively managed through a process of continuous refinement and leveraging insights from a broad spectrum of cybersecurity activities. This dynamic approach enables the creation of highly effective, behavior-based detection rules that, once fine tuned, are uniquely tailored to each customer’s environment. The commitment to ongoing service delivery and adjustment in response to the changing threat landscape is crucial for maintaining a strong defense mechanism.
It should be noted that fine tuning should make the detection more sensitive to malicious behavior (and this usually means that it creates more alerts) and at the same time minimizes noise. The challenge is to generate useful data while keeping true positive alerts.
How is this Done in Practice at Truesec?
Let’s try to explain what can feel like an quite abstract subject by exemplifying it with how we do this at Truesec.
To ensure our security measures are always ahead, Truesec actively evaluates the various Tools, Tactics, and Procedures (TTPs) used by cyber attackers. This evaluation is not just theoretical; it takes place in a simulated environment. Think of this simulated environment as a highly realistic digital theater where we recreate the IT settings common to many organizations, complete with roles for defenders and attackers. In this controlled scenario, we rigorously test a wide range of attackers’ methods to see what we can detect and what slips through the cracks.
The purpose of these tests is twofold. First, we want to see if the security setups out of the box can identify these threats. If there are gaps in detection, we then decide whether we can craft specialized detection mechanisms (we call these “Custom Detections“) or if the data on a specific attack doesn’t give us enough to work with. When the latter happens, it’s time to reach out to the product’s vendor for improvements to make sure future threats don’t go unnoticed.
The outcome of this rigorous testing benefits us in two major ways. By developing custom detection solutions, we directly strengthen the security defenses of the organization implementing them. On the other hand, when we work with vendors to enhance their products, these improvements have a global impact, bolstering security for all users of the product.
Looking Ahead in Detection Engineering
As we peer into the future of detection engineering, it’s clear that the discipline will continue to evolve, shaped by technological innovations and shifts in the cyber threat landscape. Also, the integration of AI and other emerging technologies offers new avenues for enhancing detection capabilities. Amidst these advancements, the fundamental principles of detection engineering remain unchanged. Lastly, the focus on continuous improvement, the value-driven approach to detection, and the importance of customizing defenses to meet the unique challenges faced by organizations today.
Conclusion
Detection engineering is not merely a technical requirement but a strategic imperative for organizations navigating the complexities of today’s cybersecurity threats. Through dedicated efforts, such as those by Truesec’s detection engineering team, organizations can foster a resilient and proactive security posture. Adopting a comprehensive strategy for detection engineering positions organizations to effectively tackle current and future cybersecurity threats.
Learn More
Blogpost: Empowering Threat Detection With Custom Detection in EDR