Threat Hunting
Cracking the Chaos Ransomware Family

Truesec has implemented a simple to use application that can be used to restore encrypted files for free. We are publishing the solution via the No More Ransom project, an initiative by Europol et. al. with the goal to help victims of ransomware retrieve their encrypted data without having to pay the criminals. Truesec’s decryption software is distributed as a free (GPLv3) open source software hosted on Github (https://github.com/Truesec/TSD…).
This article aims to give some context by describing the Chaos ransomware family, its strains, and the modus operandi of the threat actors behind them.
Early Days of the Chaos Ransomware
This story begins in June 2021, when the threat actor that develops the Bagli ransomware (also known as Bagli wiper), posted an inquiry for new ransomware partners on a darknet forum.
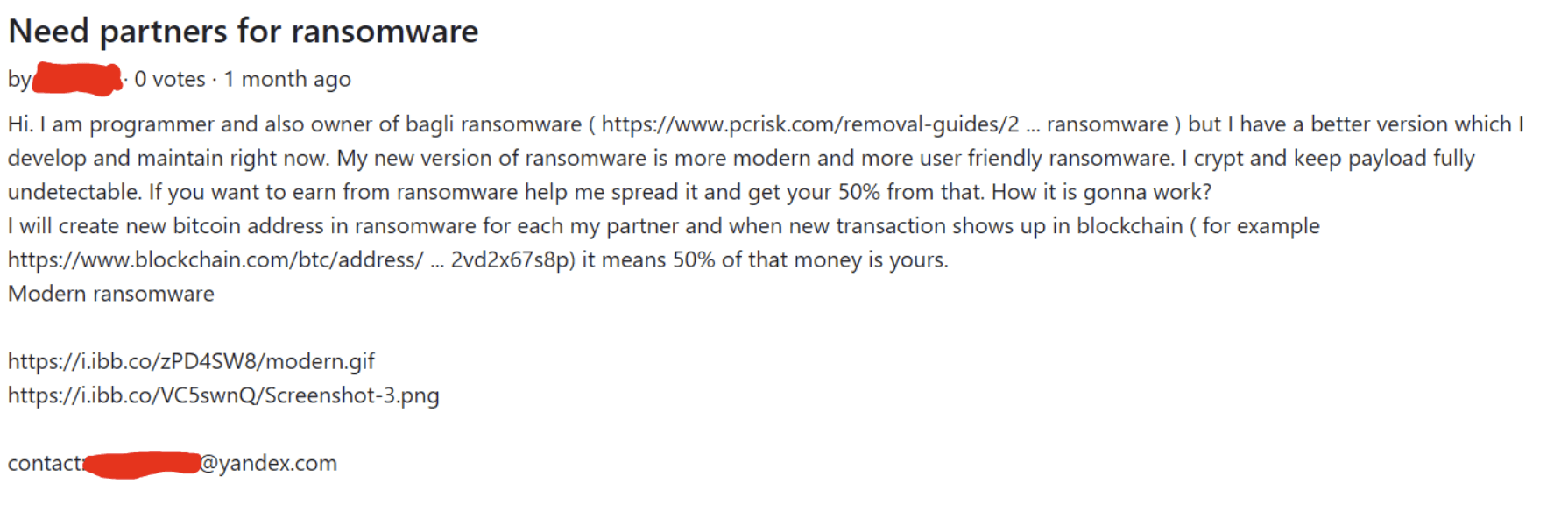
Figure 1 Confirmed via multiple sources. Screenshot is from https://mobile.twitter.com/ash…
On June 9th, the threat actor published the original Chaos ransomware builder, under the name Ryuk .Net Ransomware Builder. The motive for publishing the ransomware builder publicly is unknown. Sometimes public sharing is used to make it more difficult to attribute attacks to a specific actor. However, it might also be that it was posted publicly for attention and “street cred” in the criminal hacker community.

The ransomware has no connection to the actual Ryuk ransomware, and threat actor later rebranded the builder to Chaos Ransomware Builder.
The Chaos Ransomware builder has been constantly updated since then, and multiple forks have been observed. Truesec discovered over 50 publicly indexed samples of the ransomware that are tracked by their extension names. The relations between the samples, aside from the code being identical, are illustrated in the below figure.
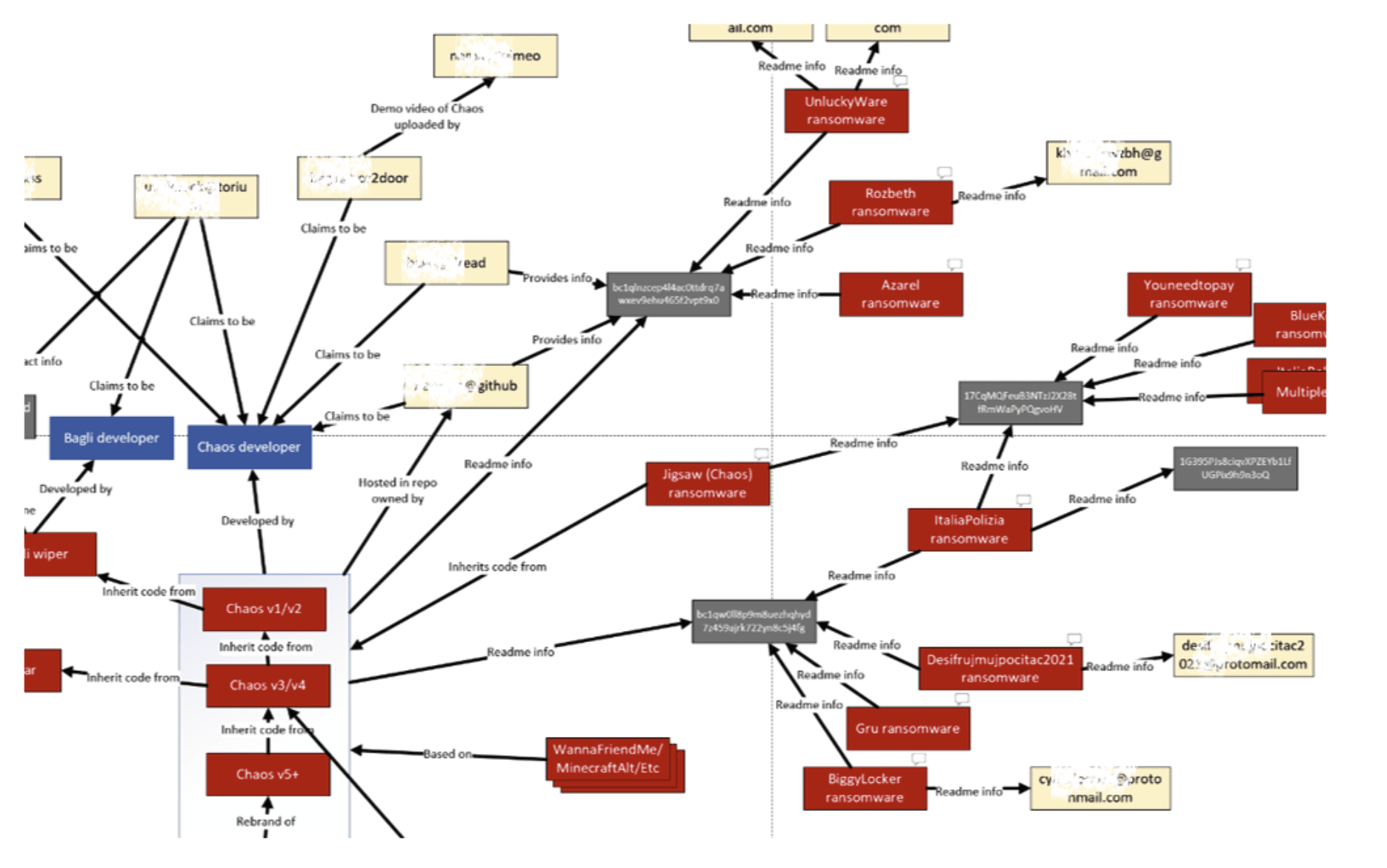
Figure 2 Chaos ransomware overview (cropped)
The ransomware has been used against both organizations and home users. The victims and delivery mechanisms are as varied as you would expect for a public ransomware builder. One notable case was the use against Azovstal in the war against Ukraine, according to researchers from Fortinet.

The early versions of Chaos (version 1 and 2) were wiperware based on the Bagli wiper. These versions overwrote all files on the system and did not perform any type of encryption. In other words, it was not possible to recover files even if payment was made to the threat actor. Version 3 added encryption functionality but opted to only encrypt files under 1 MB, other files were still overwritten. The crypto implementation appears to be based on another open source ransomware, named Hidden Tear. However, Truesec has no indications that these are developed by the same developer. Version 4 increased the limit and started encrypting all files under 2117152 bytes (2MB).
Evolution of the Chaos Family
We define the Chaos ransomware family as a set of malicious software, which are derived from this one original software that was published on Github by the threat actor.
In April 2022, a ransomware group known as Onyx (later rebranded to VSOP) started using a fork of the Chaos ransomware. The first version of the Onyx ransomware was essentially identical to Chaos ransomware version 4. The second version of Onyx made significant changes to the crypto implementation, but the overall program is still the same. The key difference is that the ransomware supports encryption of larger files, compared to the original Chaos ransomware.
The Onyx/VSOP ransomware group appears to be operated by a limited number of people and only targets enterprises and organizations. There are indications that the group is based in Russia. The group operates a ransomware site named “VSOP news”, that use Tor Onion Services to conceal the actual IP of the site. The website has a file browser where data stolen from victim organizations are presented. Generally, the VSOP group use similar modus to most ransomware groups. In other words, they perform broad initial access attacks to identify “low hanging fruit”, specifically they perform bruteforce attacks on internet-exposed RDP services. After gaining a foothold, they manually escalate their privileges in the victim environment and deploy Cobalt Strike. Finally, they destroy backups and deploy the ransomware on as many systems as possible using legitimate techniques such as Group Policy Objects (GPOs) and Sysinternals PSExec. The group has also been seen creating local user accounts on internet-exposed RDP servers for persistent access.
In August 2022, a new ransomware-as-a-service named Solidbit was launched, which is also based on a Chaos fork. The Solidbit ransomware have their own crypto implementation and uses heavier obfuscation than other forks. However, the Solidbit ransomware is still very similar to the original Chaos ransomware.
Another strain known as Yashma/AstraLocker based on the main branch of the Chaos ransomware was also active during this period, but officially shutdown in July 2022 and published their master keys for free decryption.
Internals of the Chaos Ransomware
The Chaos ransomware is a malicious wiper and cryptolocker software, developed in C#. In this section we will describe the features of this software.
Preparation phase
The AlreadyRunning function checks if the ransomware is already running by querying all running processes. If the ransomware is already running, the current process will stop.
If the checkSleep option is true, the sleepOutOfTempFolder function will pause execution, the number of seconds specified in the sleepTextbox option.
If checkAdminPrivilage option is enabled, the copyResistForAdmin function will attempt to copy itself to the appdata folder, renamed as the processName option. Then it will start a new process as admin and exit the original process.
If checkCopyRoaming is enabled and checkAdminPrivilage is disabled, the copyRoaming function will do the same as copyResistForAdmin but without running as admin explicitly.
If checkStartupFolder is enabled, the addLinkToStartup function will create a file named <ProcessName>.url, in the current user’s startup folder with the following content:
[InternetShortcut]
URL=file://<Executing Assembly Location>
IconIndex=0
IconFile=<Executing Assembly Location>
Note that this file is created prior to the encryption and will thus be encrypted by the ransomware itself.
Encryption phase
At this point, the ransomware will start encrypting the system by invoking the lookForDirectories function. The function enumerates all logical drives on the system and encrypts all folders on every volume, aside from the C volume. On the C volume, the ransomware encrypts folders in an explicit list, meaning that many folders will remain untouched.
The encryptDirectory function will be called on every folder in lookForDirectories. The function will enumerate all files in the directory and get the file size of every file. Depending on the file size, it will then perform different actions. If the file is under a certain size, it will encrypt the file, otherwise it will overwrite the file with random data. This file size limit varies between strains, and we will discuss this later on. The encryption function EncryptFile also varies between strains.
The common components of the encryption are that AES is used to encrypt file data, and the secret parameters, which are derived using System.Random, are saved in the encrypted file after being encrypted with a public RSA key.
Post-encryption phase
If CheckAdminPrivilege is enabled, the ransomware will remove shadow copies, disable recovery mode, and delete the backup catalogue (all of these having their own config option).
If the option CheckSpread is enabled, the function SpreadIt will copy the executable to the root folder of all volumes. In other words, it will not “spread” in the sense that a worm-like malware spreads, but rather only copy itself to other locations.
After this, the ransomware will write the ransomware note, open it with the default handler (typically notepad) and then set the wallpaper if the option base64Image is set.
Final phase – Crypto hijacking
After completing, the ransomware starts a new thread that monitors for clipboard activities. The WndProc function, which receives clipboard change notifications, will look for WM_CLIPBOARDUPDATE messages. If the clipboard contains a bitcoin wallet address (based on a regex) it will replace the address in the clipboard with the threat actor’s bitcoin wallet.
Comparison of the Chaos Family Strains
The encryption implementation differs between forks and versions. Chaos ransomware after version 5 can encrypt arbitrary file sizes. In addition, the Onyx strain has also, as of Onyx version 2, changed the encryption to handle encryption of larger files. This is also true for the Solidbit ransomware. The below table provides an overview of the various encryption schemes.
below table provides an overview of the various encryption schemes.
|
Strain |
Encrypts/Wipe |
Key generation |
Data crypto |
Secret crypto |
File format |
|
Chaos 1 |
Overwrites every file. |
N/A |
N/A |
N/A |
N/A |
|
Chaos 2 |
Overwrites every file. |
N/A |
N/A |
N/A |
N/A |
|
Chaos 3 |
Encrypts files under 1 MB. Overwrites larger. |
20-char password (System.Random). Key and IV generated from password with Rfc2898DeriveBytes (1000 iteration and static salt) |
AES-256-CBC |
RSA-1024 |
AES key encrypted with RSA and prepended to the file within the ASCII “<EncryptedKey>”. Encrypted data is base64 encoded. |
|
Chaos 4 |
Encrypts files under 2 MB. Overwrites larger. |
20-char password (System.Random). Key and IV generated from password with Rfc2898DeriveBytes (1000 iteration and static salt) |
AES-256-CBC |
RSA-1024 |
AES key encrypted with RSA and prepended to the file within the ASCII “<EncryptedKey>”. Encrypted data is base64 encoded. |
|
Chaos 5+ |
Can encrypt arbitrary size |
20-char password (System.Random). Key and IV generated from password with Rfc2898DeriveBytes (1000 iteration and static salt) |
AES-256-CBC |
RSA-1024 |
AES key encrypted with public RSA key and prepended to the file within the ASCII “<EncryptedKey>”. File data encrypted and base64 encoded. |
|
Onyx 1 |
Encrypts files under 2 MB. Overwrites larger. |
20-char password (System.Random). Key and IV generated from password with Rfc2898DeriveBytes (1 iteration and static salt) |
AES-256-CBC |
RSA-1024 |
AES key encrypted with RSA and prepended to the file within the ASCII “<EncryptedKey>”. Encrypted data is base64 encoded. |
|
Onyx 2/VSOP |
Can encrypt arbitrary size |
40-char password (System.Random). Key and IV generated from password with Rfc2898DeriveBytes (1 iteration and static salt) |
AES-256-CFB |
RSA-1024 |
AES key encrypted with public RSA key and appended to the file. File data encrypted and stored as raw bytes. Static salt prepended to file. |
|
Solidbit |
Can encrypt arbitrary size |
Key and IV bytes generated with System.Random. |
AES-128-CBC |
RSA-1024 |
AES key encrypted with public RSA key and appended to the file. File data encrypted and stored as raw bytes. |
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.