Active Directory Tiering
Peter Löfgren Principal Technical Architect

What’s an AD Tiering Implementation?
Active Directory Tiering, or AD Tiering, is not just a technical concept; it’s about safeguarding your most valuable assets in the most secure layers. This approach, involving partitioning administrative privileges – often referred to as Privileged Access Management (PAM) – has been recommended for over a decade.
The concept of putting our most valuable things in the most protected place isn’t new. It’s been around pretty much since we’ve had….well, things.
Peter Löfgren – Principal Technical Architect
Despite its critical importance, especially considering that about 90% of Global Fortune 1000 companies rely on Active Directory (AD) for authentication, AD Tiering is surprisingly underutilized. Historically, the lack of deployment has been sparse simply because the implementation of AD tiering is perceived as a large, complex project often associated with significant risks to the availability of a company’s systems and resources.
What’s Different About Truesec’s AD Tiering Implementation?
At Truesec, our approach to implementing AD Tiering stands out. We’ve successfully integrated AD Tiering into numerous systems without disrupting business operations. Contrary to common belief, our process is swift and efficient – typically completed in days, not weeks or months, as others might suggest. For a detailed breakdown, Peter Löfgren’s video tutorial offers an insightful step-by-step guide.
Leveraging Experience in Cyber Incident Response
As a renowned leader in cyber incident response, Truesec not only resolves incidents but also actively engages with global cybersecurity experts. This collaboration enables us to both learn and share crucial insights. One significant tactic we’ve noticed among cybercriminals involves lateral movement within networks. They typically navigate from one computer to another, seeking credentials that elevate their privileges, often aiming for domain admin access.
How Active Directory Tiering (AD Tiering) Counters These Threats
To counter such sophisticated attacks, implementing an Active Directory Tiering model is essential. AD Tiering effectively segregates the network into multiple security zones or “tiers.” This structure prevents attackers from accessing anything beyond their initial breach point.
By creating these distinct tiers, we isolate high-risk devices like regular workstations from the more critical ones, such as domain controllers, backup systems, Public Key Infrastructure (PKI), and other vital business applications. This tiered approach in AD management not only adds a robust layer of security but also significantly hinders an attacker’s ability to compromise the entire network.
The Advantages of Implementing Active Directory Tiering
- Doesn’t require new tools, only the correct use of existing tools.
- Allows for a secure and efficient usage of your existing infrastructure. It aligns with your current systems, ensuring that your investments are maximized for better security outcomes.
- AD Tiering is making it significantly more challenging for attackers to compromise sensitive systems. By segregating access and privileges, it adds a robust layer of defense against various cyber threats.
- AD Tiering enables the safeguarding of your organization’s most valuable assets and systems. This is achieved without introducing unnecessary complexity into your business processes, ensuring that security enhancements don’t hinder operational efficiency.
- Beyond the initial implementation, AD Tiering opens up the way for ongoing improvements in your cybersecurity posture. It sets a foundation for continuously evolving and strengthening your defenses against emerging cyber threats.
Active Directory Tiering: A Practical Illustration
As previously noted, when the AD is tiered, you limit the exposure of sensitive credentials. This explanation highlights how Active Directory Tiering (AD Tiering) works in a real-world scenario using two hypothetical employees, Linda and Patricia.
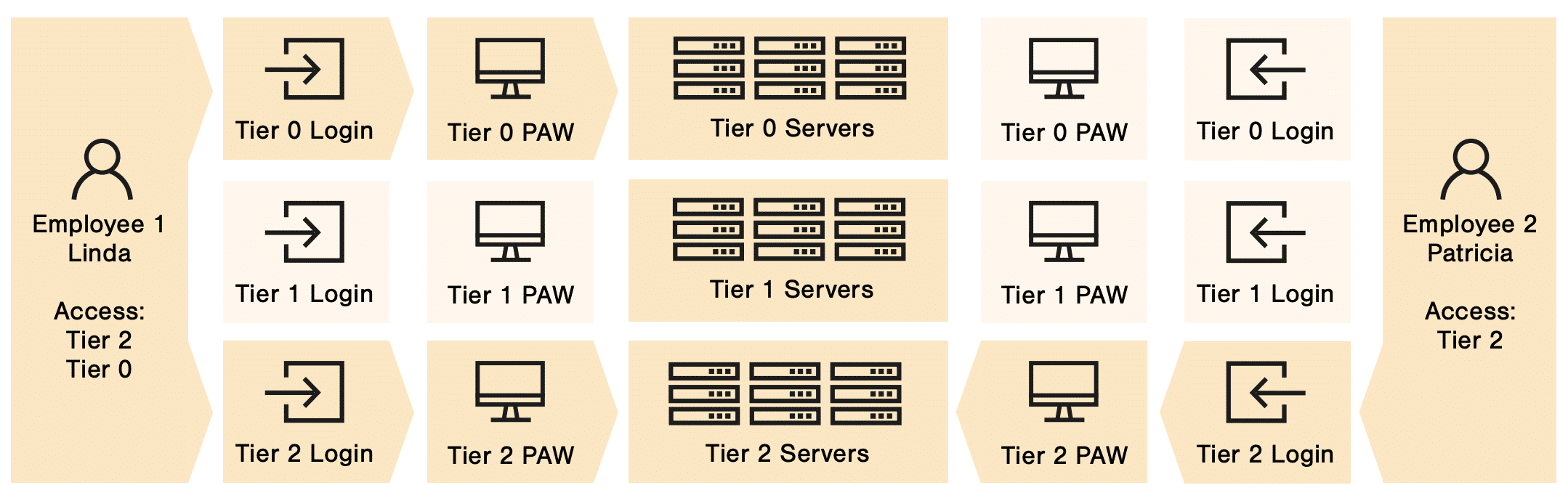
Linda’s Access in Tier 0 and Tier 2
Linda, designated as Employee 1, is granted administrative privileges in both Tier 0 and Tier 2 of the company’s network. When working in Tier 0, Linda uses her specific Tier 0 admin account, along with a dedicated Tier 0 Privileged Access Workstation (PAW). This setup restricts her movement to within Tier 0 only, in line with the stringent logon and control restrictions set by Group Policy Objects (GPOs) in Active Directory. The GPOs’ enhancing security settings ensure that neither her admin account nor the Tier 0 PAW can access other tiers.
Linda’s Role in Tier 2
Similarly, when Linda needs to perform administrative tasks in Tier 2, she switches to her Tier 2 admin account and uses the corresponding Tier 2 PAW. This segregation is crucial for maintaining strict security protocols and preventing unauthorized access across different network tiers.
Patricia’s Limited Access in Tier 2
Patricia, referred to as Employee 2, has a more restricted role. Her administrative capabilities are confined to Tier 2. She accesses this tier using her Tier 2 admin account and a designated Tier 2 PAW. This ensures she can administer the necessary servers or systems within Tier 2 without the risk of cross-tier interference.
An example of the GPOs and the organizational unit (OU) structure is shown in the tiering model below.
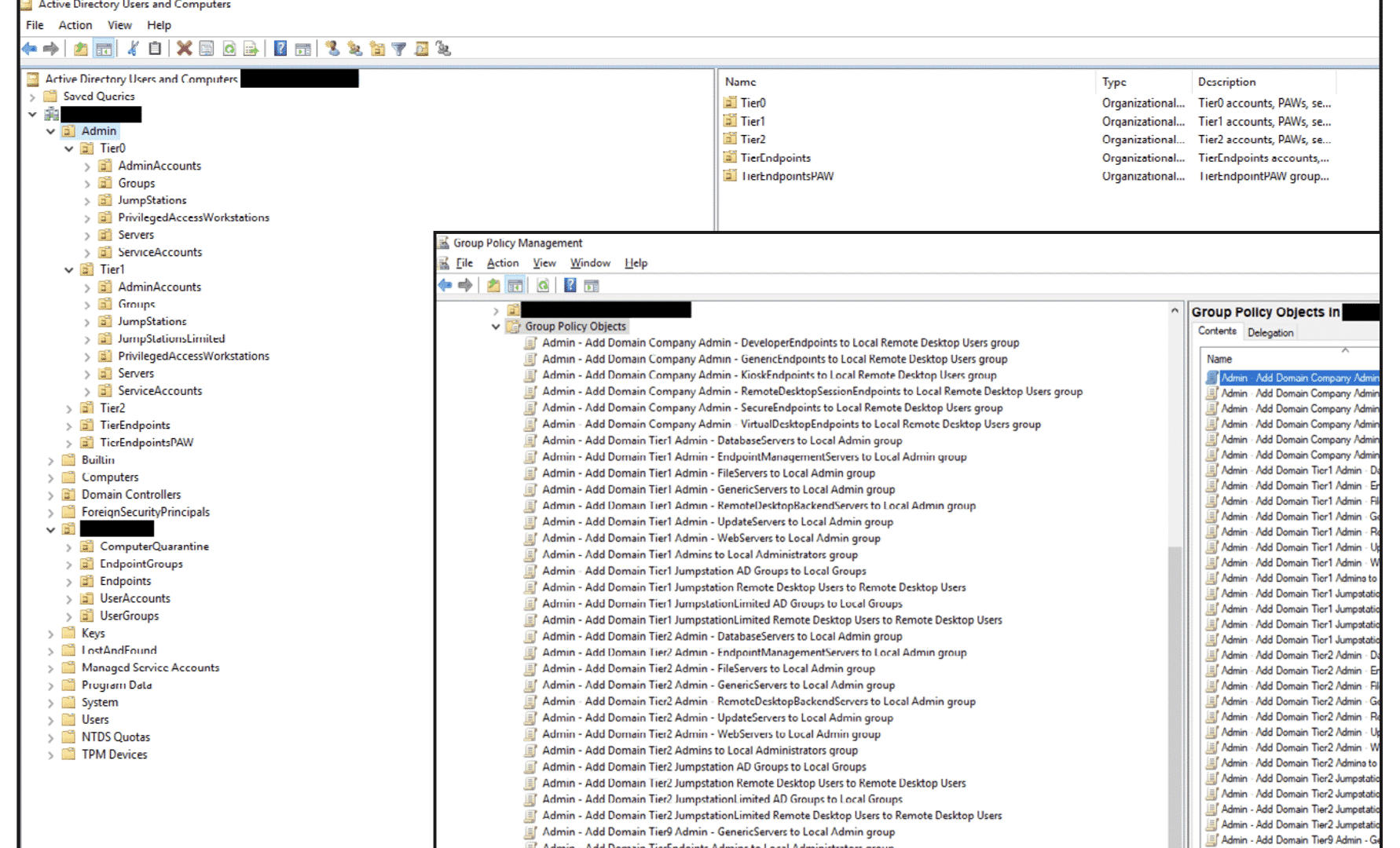
The Truesec AD Tiering Methodology
Implementing an Active Directory Tiering model can be a huge step for your organization’s cybersecurity posture. While this process can be self-managed, Truesec’s team of cybersecurity experts has developed a battle-proven methodology and is available to assist if needed. The methodology is divided into three phases, each designed to ensure a comprehensive and secure implementation.
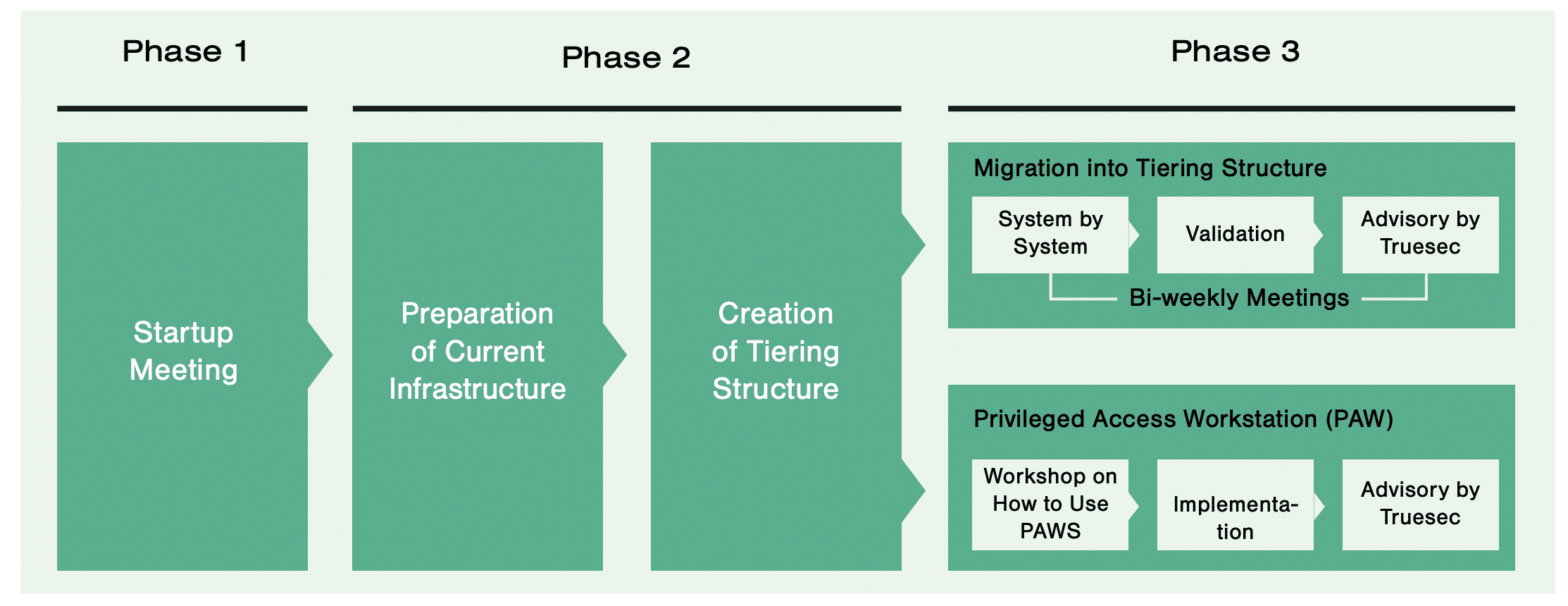
Phase 1 – Gain Knowledge and Define Expectations
We conduct a startup meeting that includes the concepts and benefits of working with a tiering model. Examples of areas covered:
Initiate a startup meeting with the team to make sure they understand the concepts and benefits of the tiering model. Key topics should include the rationale behind using a tiering model, the structure of the tiered system, and the role/implementation of privileged access workstations (PAW).
- Why a tiering model should be used.
- Define the tiering model.
- Why and when to use a privileged access workstation (PAW).
- Ways of working for admins.
Phase 2 – Implementation and Structure Development
In Phase 2, the environment is prepared, and information regarding current and future privileged users is collected. Then the new tiering structure is created with all the policies and settings required. “Break glass” accounts are also created.
- Prepare the environment for the new tiering system, including data gathering on current and future privileged users.
- Construct the tiering structure with the necessary policies and settings. This includes creating “break glass” accounts for emergency access.
- Use guidelines and resources to execute these steps effectively.
Phase 3 – Guidance
In Phase 3, the systems are protected one by one in the new tiering model implemented by your team. Also, at this stage, the implementation of privileged access workstations (PAW) is completed. As this establishes a “new way” of accessing the environment for some administrators, it’s important to train your staff and be there to guide and assist during this phase.
- Progressively secure systems under the new tiering model, guided by a structured plan.
- Complete the implementation of PAWs, adapting to the new access protocols for administrators.
- Regular review meetings (e.g., bi-weekly) within your team to monitor progress and address challenges.
Conclusion
In summary, implementing an Active Directory Tiering model is a pivotal step toward enhancing your organization’s cybersecurity posture. The process, structured into three distinct phases – knowledge, implementation, and operationalization – offers a clear roadmap for this change. While organizations can undertake this journey independently, leveraging the expertise of Truesec’s cybersecurity professionals can provide invaluable guidance and support. Whether you choose a self-managed approach or seek expert assistance, the goal remains the same: to establish a robust, efficient, and secure IT environment through effective Active Directory Tiering.