Powered by the Truesec Cyber Security Platform

See the Threats. Prioritize the Risks. Act Before It’s Too Late.
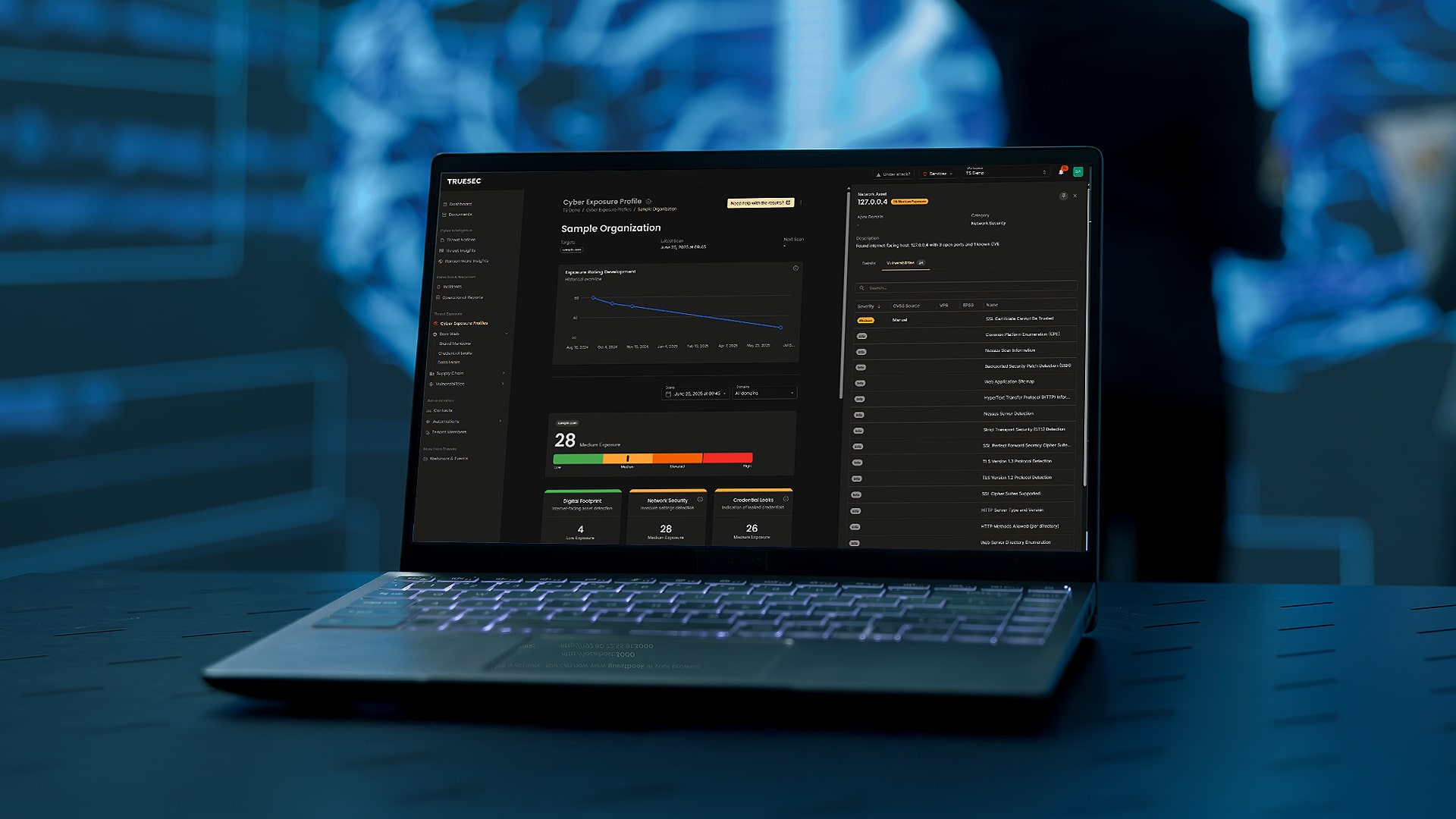
Managed Threat Exposure (MTE) gives you continuous visibility into your attack surface, so you can identify, assess, and prioritize vulnerabilities before they’re exploited. With MTE, you gain the insights needed to make strategic, risk-based security decisions, not just technical fixes. It’s the foundation for building true cyber resilience.
Get free access and see your vulnerabilities – before they are exploited.

Powered by the Truesec Cyber Security Platform
Proactive Cybersecurity
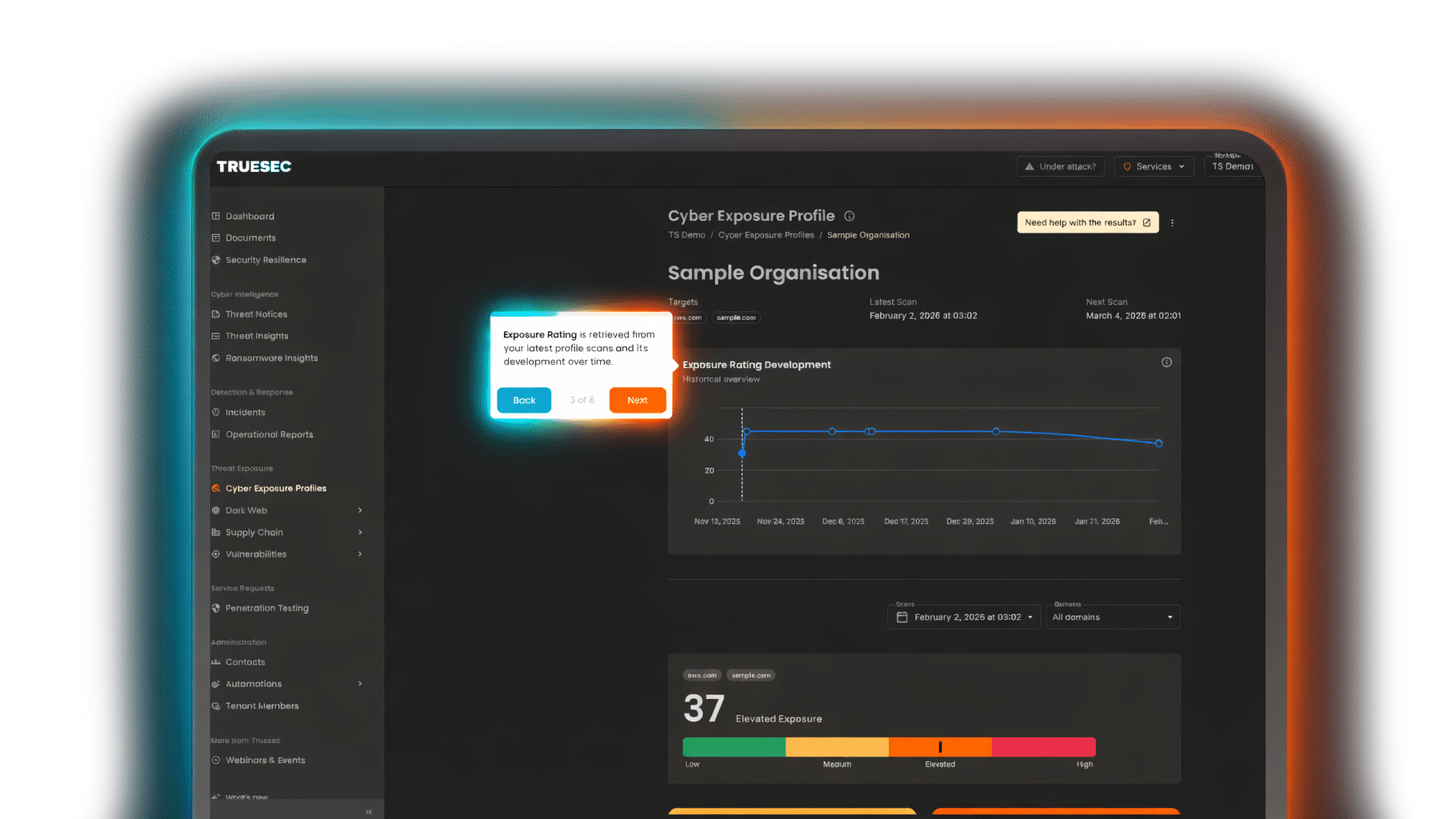
See MTE in Action
For teams starting their exposure management journey. Provides curated threat updates, monthly external scans, and visibility into exposed credentials, vulnerabilities, and vendor breaches.
For organizations with existing security operations. Adds daily threat and vulnerability alerts, deeper context from multiple data sources, and support for third-party tools and agents.
For mature teams who need transparency, integration, and control. Adds access to Truesec’s scoring methodology, customizable reporting, and planned validation via attack simulation.
We offer flexible tiers designed to meet different needs and budgets. Explore the options below to find the one that’s right for you.
Please note: while many features are available across all tiers, the depth of functionality or service may vary.

Free trial

Whether you’re looking for foundational visibility or advanced integration with your internal processes, Managed Threat Exposure (MTE) has a tier that meets your needs.
Talk to us to find the right fit.