Detect and Respond
The Importance of Detecting Cyber Threats Before Operations are Impacted
Time is the most critical factor when reducing the damage of a cyber security breach. Therefore, detecting a breach as quickly as possible, and having the capability to disarm and isolate the intruder, is key.
A cyber breach happens either through a vulnerability in your IT infrastructure or your organization. You can mitigate some of the vulnerabilities, but you can never build a 100 percent safe environment. Therefore, you need to be prepared to be breached and to take immediate action when it happens.
Threat Detection Is Key
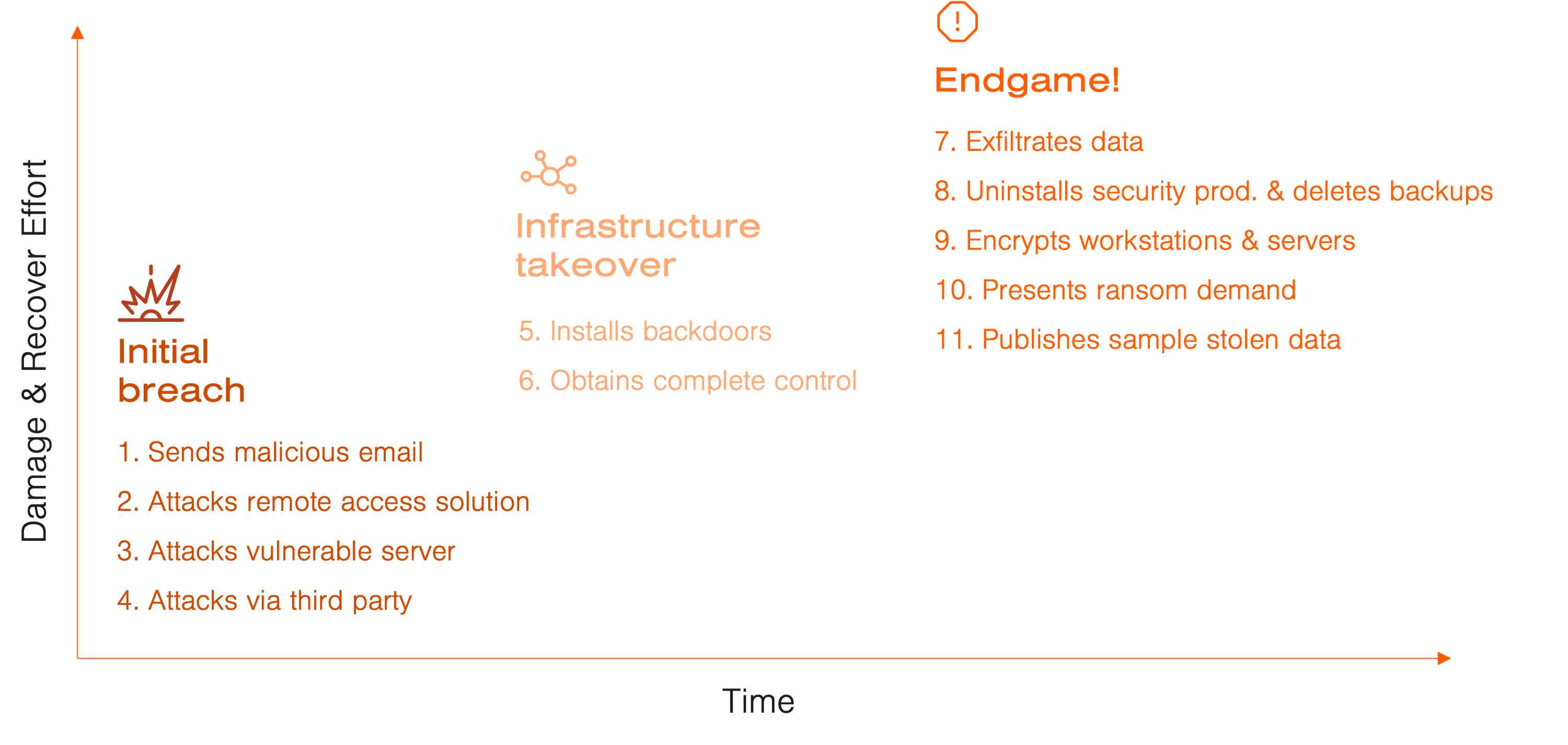
The first step is being aware that you are being attacked. It may come as a surprise, but a vast number of security breaches take months or even years to detect. An IBM study found that, on average, it took companies close to seven months to detect a breach, and another two months to contain it. Costs to organizations per cyber breach have reached high levels and in 2021 a cost of a cyber breach was 4,24 million USD according to another study by the same company*. We know that time to discovery and appropriate actions are strongly correlated to the damaging impact of a cyber breach and efforts required to recover from it.
Detecting malicious activity in your IT environment is fundamental, not to mention critical, to minimize the damage done and stop the intruder in their tracks. Therefore, you must constantly monitor your network activity and learn how to detect anomalies. On top of that, you need to be able to mitigate attacks and isolate the intruders.
Typical Breach Process
Monitor Your Environment 24/7 With a SOC Service
Enter the Security Operations Center (SOC). The focus of a SOC is protecting your business by detecting and responding to threats in real-time. A SOC monitors the activity of all your computers, phones, tablets, servers, cloud services, and the identity of your users. When suspicious activity is detected, alarms alert the SOC operators. They will determine if a cyber breach is taking place, based on, among other things, the information gathered from your environment and their knowledge of the current threat landscape.
Add Real-World Cybersecurity Experience
What sets different SOC services apart is how well they detect and mitigate cyber breaches. The SOC operators need to have an updated, real-world understanding of the current threat landscape, not just theoretical knowledge. This can be achieved by working with threat hunting, cyber forensics, and knowledge sharing between SOC operators. When a new vulnerability is discovered in one client’s network, the whole team should scan for the same vulnerability in all clients’ environments. This way, the SOC service will help you be proactive and continuously develop your IT security strategy.
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.