Stay ahead of the intruders
Why Safeguarding Your Digital Assets Is a Must
In the connected world, information and digital assets can be shared and distributed in an unprecedented way. This not only presents us with great business opportunities and innovations, but also new challenges in protecting valuable information.
As cyber threats continue to evolve where both sophisticated attacks and seemingly innocent mistakes create unwanted sharing or even theft of business-critical knowledge, the need for modern and continuous information security is higher than ever before.
Since last year, organized cybercrime gangs have expanded their ransom attacks and now increasingly steal sensitive business data as well. One more change is that the speed from initial breach to large-scale encryption continues to increase. We have basically gone from a situation where days was still relevant to the current relevant measurement of only hours and even minutes.
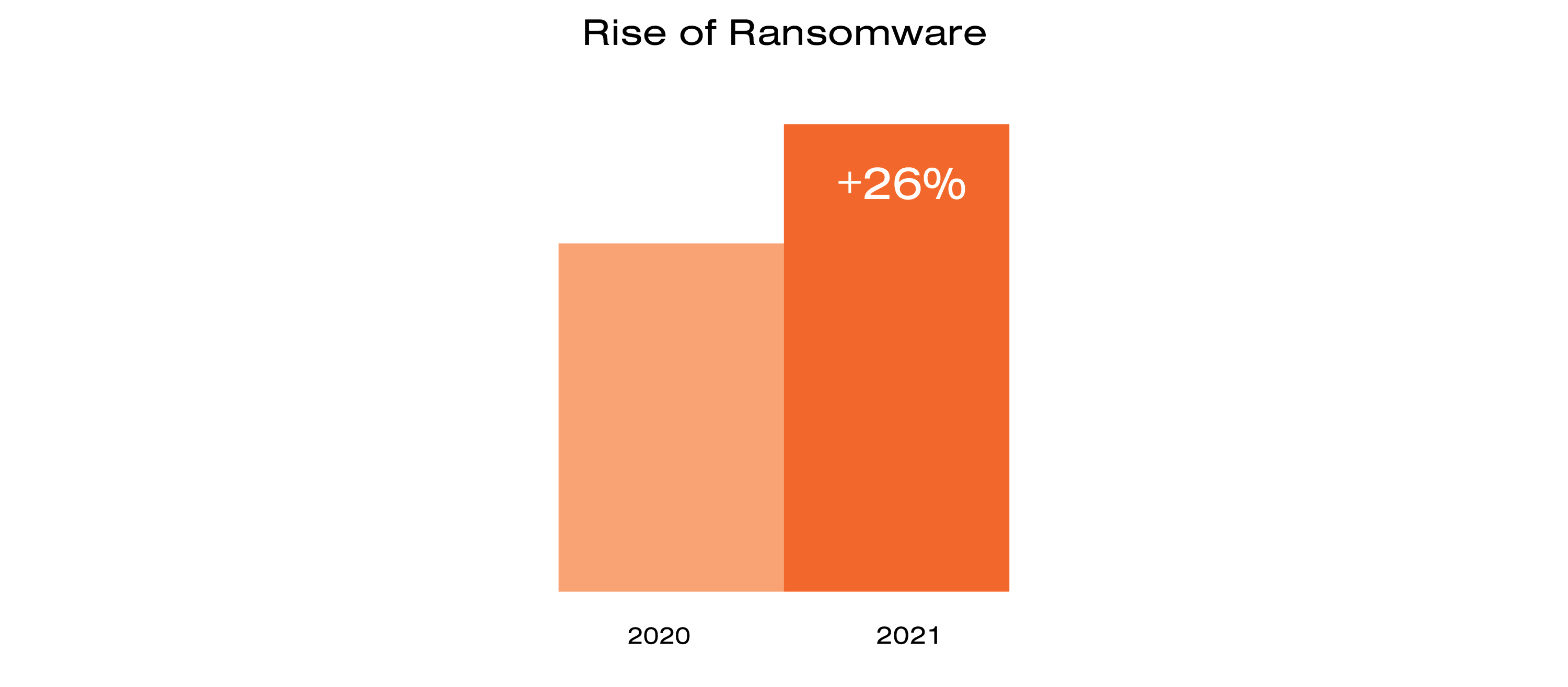
Because no cyber defense is perfect, the assumption that cyber threats and attacks eventually could breach and compromise any system should be acknowledged. This is often also called the “assume breach” mentality in cybersecurity. In line with this approach, an organization will not consider prevention measures as complete intrusion mitigation.
When a breach eventually happens, the damage will very much depend on if and how fast the breach is detected and acted upon. The longer an intruder is allowed to act the higher the risk of losing control and critical assets. Therefore, a natural consequence of the “assume breach” approach is to introduce strong intrusion detection combined with an ability to disarm and mitigate as fast as possible.
Monitor Your IT To Keep Your Assets Safe
Having a solid monitoring capability in place not only illustrates the threat situation for companies and organizations but also makes it possible to detect and disarm potential intrusions much more efficiently.
This is primarily accomplished by monitoring all relevant endpoints in your organization, from servers and cloud capacity to laptops and mobile units. If a more serious incident occurs, it provides critical information to understand what has happened, how to manage the situation, and, in particular, what improvements need to be made to avoid similar incidents in the future.
Finally, it makes it possible to trace and document what has happened, which can be crucial for reporting issues, regulatory requirements, market expectations, and customer relationships.
Protecting Your Data Requires 24/7 Control
In many ways, this is like protecting assets in the physical world. To be able to protect what is most valuable for your organization, you need to understand and monitor your environment. If something unwanted or unexpected happens, rules and routines should be in place in order to take the right actions and use the right resources to meet potential threats in the right way. This readiness is necessary to have at all times.
Therefore, a managed monitoring service, Detect and Disarm, sits at the very core of a good cybersecurity approach.
So, if you feel strongly that your organization needs to increase the protection of business-critical digital assets, the time might be right to implement a professional monitoring service that makes it possible to detect and disarm potential security threats.
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.