A case of the FAUST Ransomware
In October 2023, Truesec CSIRT was engaged to respond to an incident related to the FAUST ransomware and that affected an organization active in the selling of luxury goods. Several configuration and design mistakes made the intrusion possible and participated in the unhindered movements within the network.

Lessons learnt (Bottomline upfront)
- The Threat Actor (“TA”) gained initial access via a Remote Desktop Protocol (“RDP”) port directly exposed to the Internet.
- The TA signed in using valid credentials to an unused and unattended account.
- Lateral movement was possible due to a flat network with no access-control and due to very little defense mechanisms on endpoints. The movements included a mix of RDP and PsExec.
- The TA exfiltrated data to filesharing platform Mega.io.
- Defense mechanisms present on hosts were impaired and users were expelled.
- The TA spent less than 72 hours in the network between initial access and encryption.
Initial Access
The client operates several websites related to its commerce of luxury goods. Due to a design mistake, the server had two interfaces: one connected to the internal network and one connected to the outside network, bypassing the firewall. The local windows firewall was not enabled and, as a result, all the ports open on the machine were accessible from the whole internet, including WinRM, Netbios and RDP. The open ports visible from Shodan are shown in Figure 1.
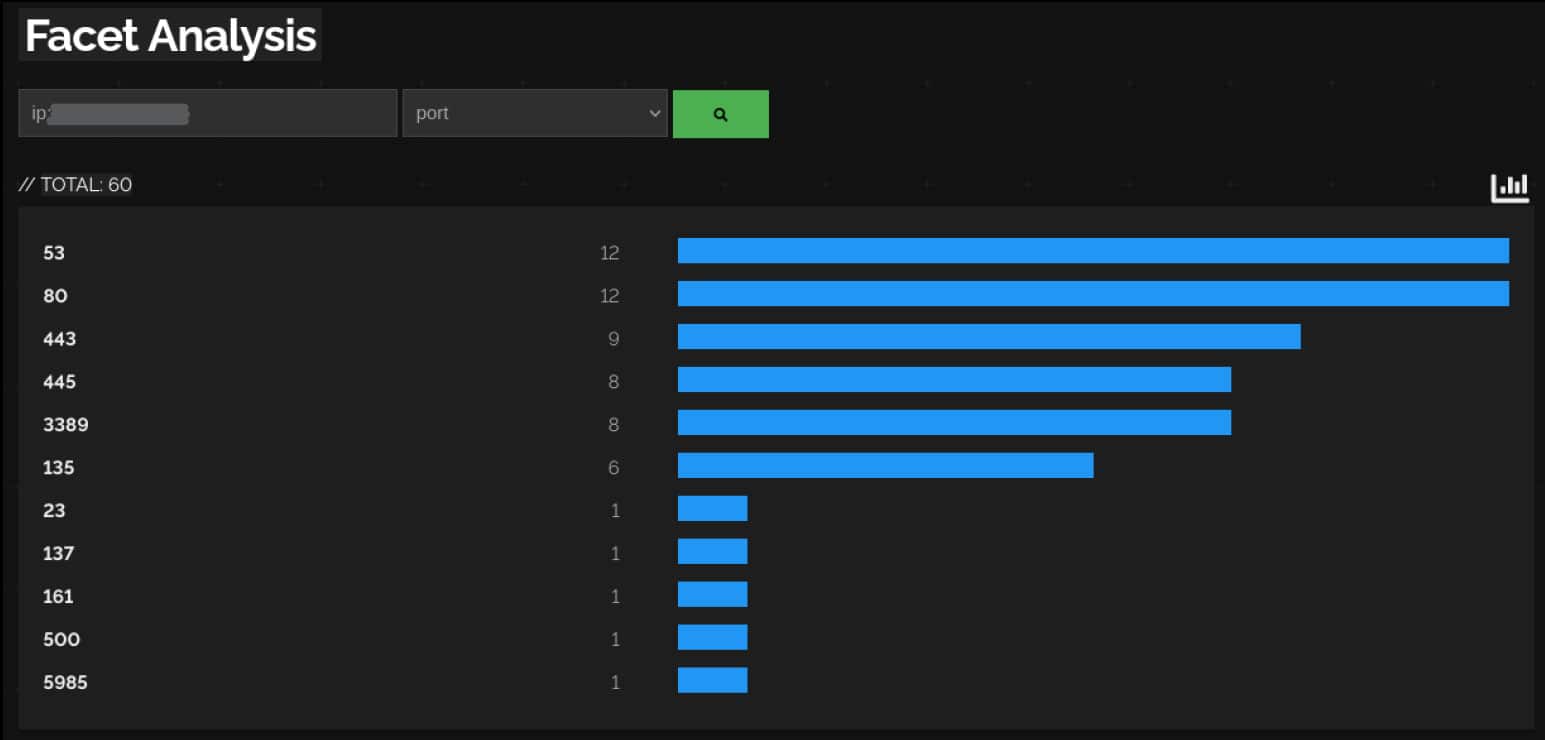
The Threat Actor used the usual domain administrator DOMAIN\Administrator for this connection. This account was left unattended and unused, with a last password change more than 5 years before the incident happened
Credential Retrieval
On one of the domain controllers, the Threat Actor enumerated the members of the “Domain Admins” domain group. Additionally, the Threat Actor ran two opensource hacking tools, Mimikatz and LaZagne, to dump and retrieve credentials from memory, registries, and applications.
Network Enumeration
The Threat Actor ran several network scans, using SoftPerfect’s Network Scanner.
Lateral Movement
The threat actor used Sysinternals’ PsExec and Microsoft RDP to move from one system to another.
Defense Impairment
Two methods were used: forcefully logging off users and disabling Windows Defender.
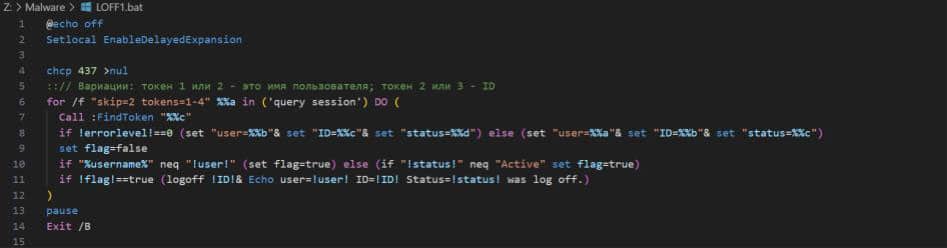
To logoff users, the threat actor ran a script called LOFF.BAT or LOFF1.BAT, shown in Figure 1. It iterates over the logged-in sessions and issues the corresponding “logoff” command. Interestingly, there is a comment in Russian and a code page change (“chcp”) to CP437 (US).
The second tool is called DefenderControl.exe and does just that: it disables Windows Defender.
Data Exfiltration
Prior to exfiltration, the threat actor used a tool called WizTree64.exe. While the exact activities the TA performed with this tool are not known, it is presented as a “disk space optimizer” and can generate, among other, detailed lists of files.
The TA used the MegaSync tool to exfiltrate data to the Mega Cloud Storage. As the TA did not claim to have a blog on which breaches and leaked data is published, how the TA plans to leverage the data to pressure the victim into paying is unknown.
Faust Ransomware
This ransomware is part of the Phobos ransomware family. It has a few built-in features to prevent recovery, such as disabling the startup recovery and deleting the shadow copies. It also creates an entry for itself to be started when Windows starts.
It is a “Ransomware-as-a-Service” (“RaaS”): any cybercriminal may, for a fee, generate an encryptor based on a minimal configuration. As such, it is almost impossible to attribute this attack to a specific or established TA.
During the encryption process, it drops two files, info.hta and info.txt, containing the same ransom note. This ransom note contains an email address to contact to negotiate the terms as opposed to a link to an onion site, further reinforcing the belief that the TA behind this attack is not one of the usual, more organized group.
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.
