Exploitable Critical RCE Vulnerability Allows Regular Users to Fully Compromise Active Directory – PrintNightmare CVE-2021-1675 and CVE-2021-34527

PrintNightmare (CVE-2021-1675) is a vulnerability that allows an attacker with a regular user account to take over a server running the Windows Print Spooler service. This is by default running on all Windows servers and clients, including domain controllers, in an Active Directory environment. EDIT: Microsoft has assigned a different CVE to PrintNightmare: CVE-2021-34527.
In practice, this means that an attacker with a regular domain account can take over the entire Active Directory in a simple step. For example, if a user is compromised with a phishing attack, a threat actor can use the compromised computer to easily take over Active Directory in a matter of seconds (this can also be fully automated).
A proof-of-concept (PoC) exploit was recently published (and quickly removed). Although deleted, the GitHub repository had already been cloned.
The main issue is that although CVE-2021-1675 was supposed to be patched on June 8th according to Microsoft, and therefore the recommendation has been to simply update your systems, the PrintNightmare exploit still works on a fully patched domain controller.
We have verified this by running the exploit against a fully patched domain controller running Windows Server 2019 (we have not tested other versions yet), over the network, using a regular domain account.
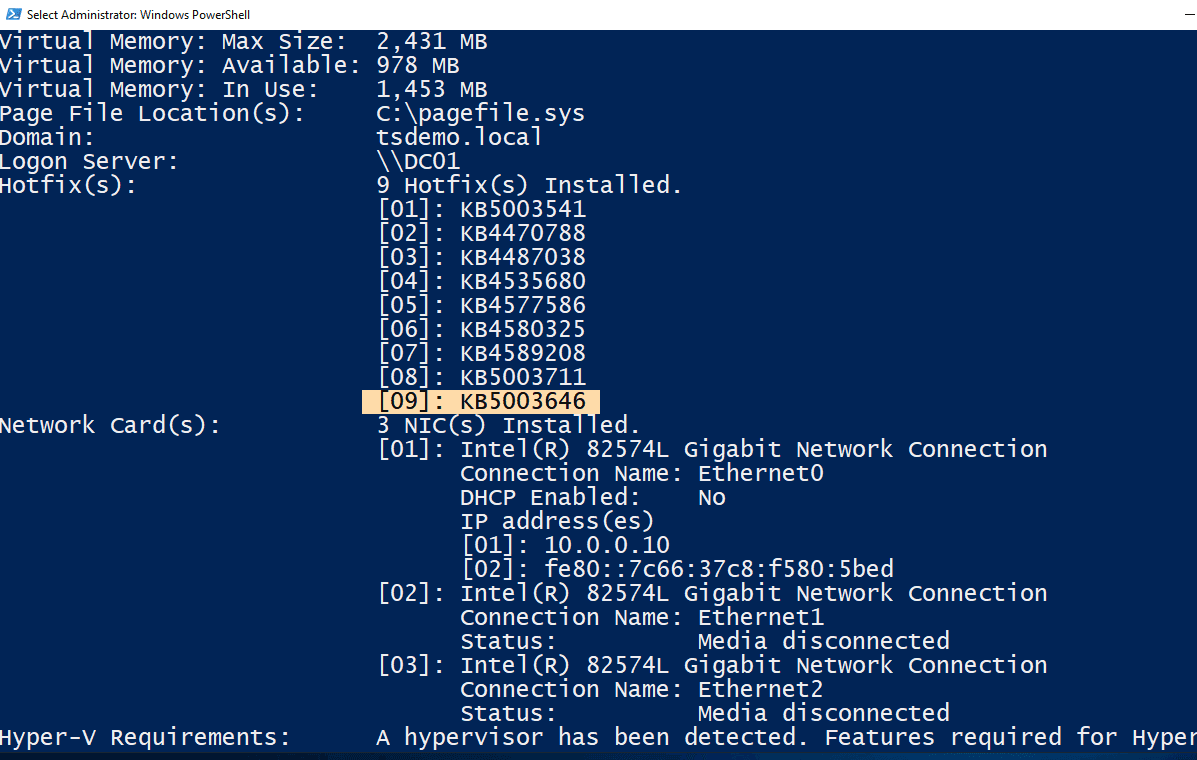
Target Domain Controller, fully patched including KB5003646
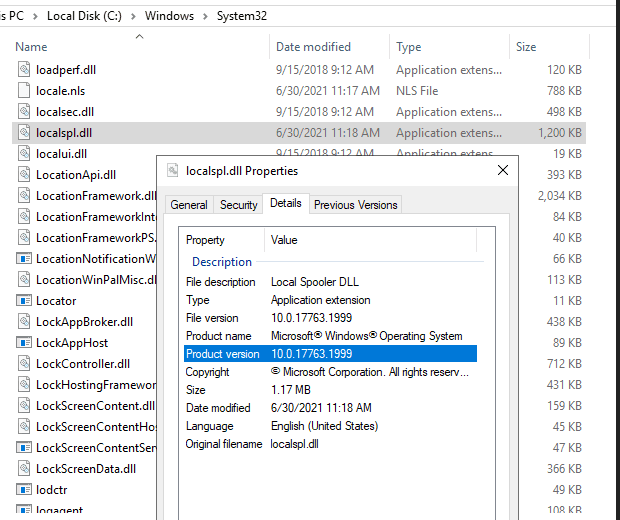
Version of the patched Print Spooler DLL
We have tested one of the exploits available on GitHub using a regular domain account, to deliver a PoC DLL that would simply output the current username to a file in C:poc.txt
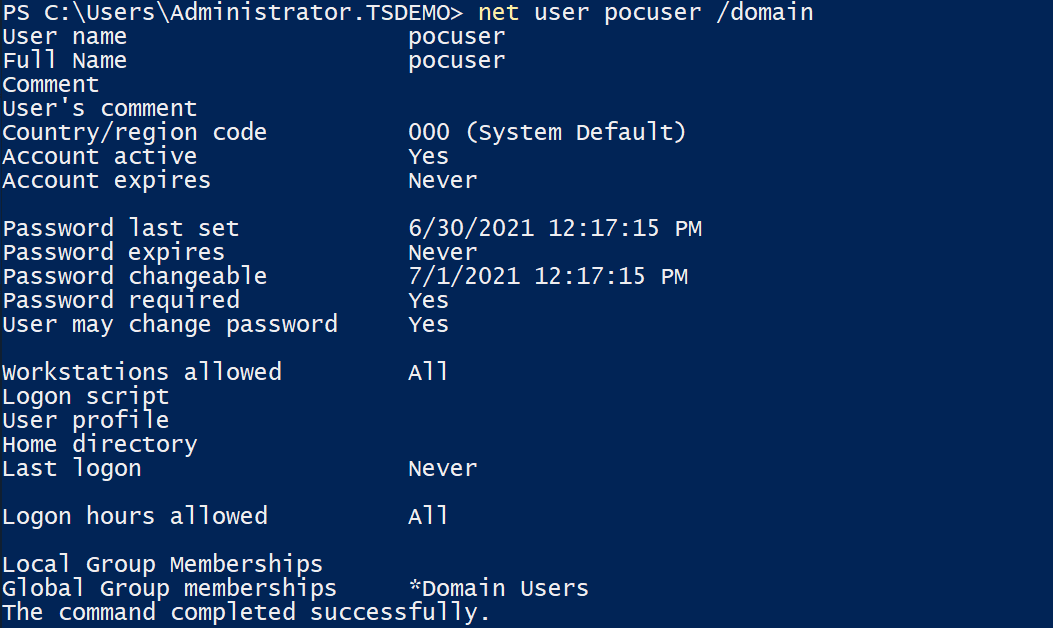
Regular domain account used for the PoC
Exploiting PrintNightmare CVE-2021-1675
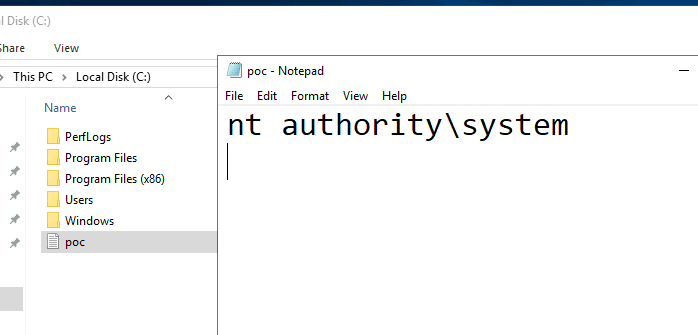
Successful exploitation of PrintNightmare CVE-2021-1675 confirming SYSTEM privileges on a fully patched Windows Server 2019 domain controller
Recommendations
NOTE: scroll down for updated recommendations.
Remote attackers with access to a user capable of authenticating to the spooler service can gain full control of any system running the print spooler service by exploiting CVE-2021-1675 / CVE-2021-34527.
Due to the nature of the exposure, all systems (especially domain controllers) need to have the Print Spooler service disabled until a working patch is available and installed. NOTE: the service should be disabled, not stopped. If it is only stopped, it may be triggered to start again.
Even without this vulnerability, the recommendation has been to avoid running the print spooler service on any domain controller, as it can be used to elevate privileges to a domain controller computer account when a threat actor has access to a user with unconstrained delegation.
Disallow client connections
Disabling the Print Spooler service on clients will impact the clients’ general ability to print to any printer. An alternative workaround to disabling the service is to configure it to not accept client connections. This will effectively limit the access to the local machine preventing the remote exploitation of PrintNightmare.
Configure the “Allow Print Spooler to accept client connections” setting locally or using a GPO. The policy is part of the Administrative Templates in the Computer Configuration.
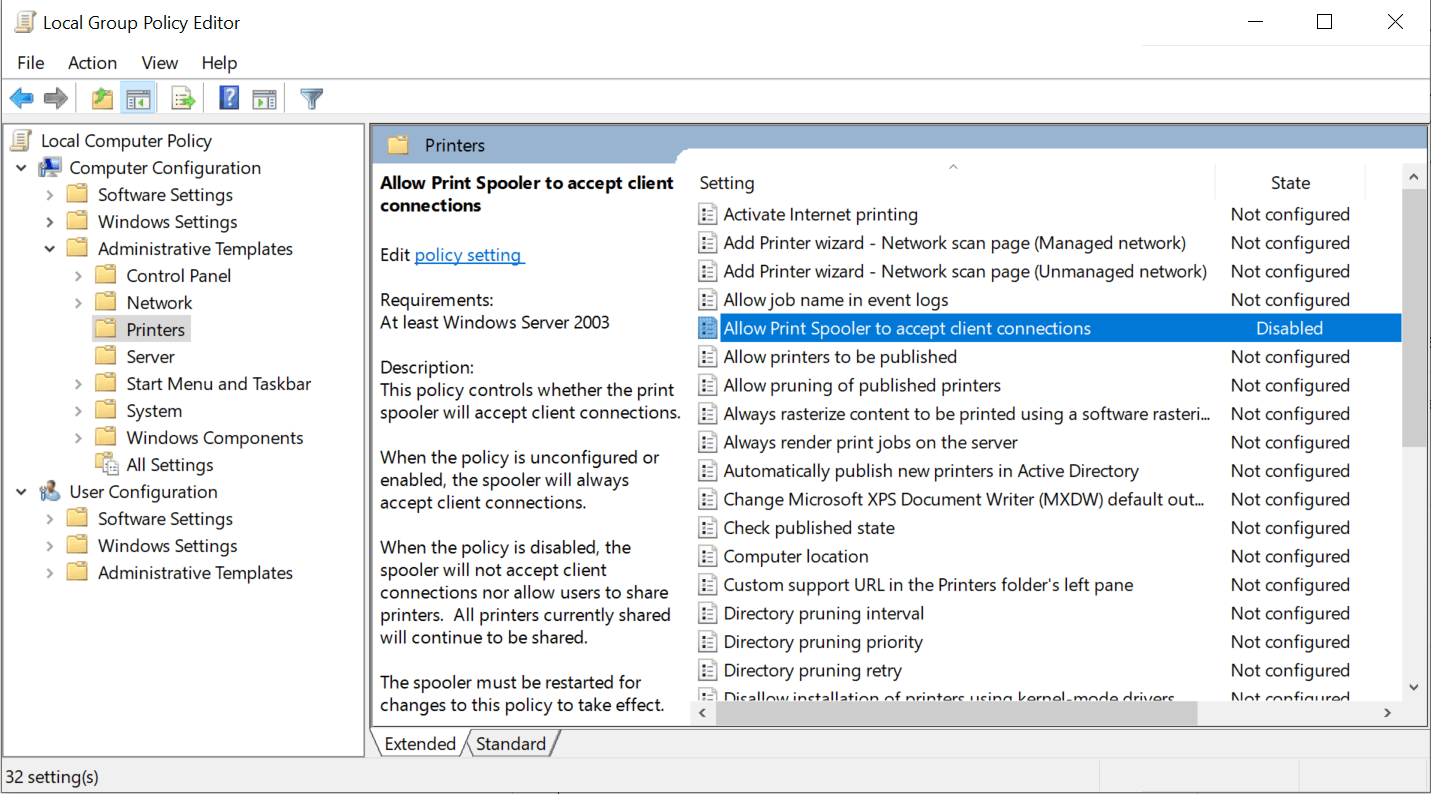
Policy to disallow client connections
Workaround
For systems where the print service is absolutely needed, here we describe a possible workaround to prevent exploitation and keep the servers running until a patch is available.
UPDATE JULY 6th, 2021
Microsoft released an Out-of-Band (OOB) Security Update available for CVE-2021-34527.
The fix includes new features that allow customers to implement stronger protections. See KB5005010 Restricting installation of new printer drivers after applying the July 6, 2021 updates.
Optionally configure the RestrictDriverInstallationToAdministrators registry value to prevent non-administrators from installing printer drivers on a print server.
| Registry location | HKEY_LOCAL_MACHINE SoftwarePoliciesMicrosoftWindows NTPrintersPointAndPrint Note: The RestrictDriverInstallationToAdministrators registry setting resides under the PointAndPrint registry location but is specific to protections for CVE-2021-34527 but is not related to point and print behavior. |
| DWord name | RestrictDriverInstallationToAdministrators |
| Value data | Setting the value to 0, or leaving the value undefined allows non-administrators to install signed drivers and allows administrators to install signed and unsigned printer drivers to a print server. This is the default value. Setting this value to 1 or any non-zero value prevents a non-administrator from installing any signed or unsigned printer driver on a printer server. Administrators can install both a signed or unsigned printer driver on a print server. Note: If this value is set to 0, the registry value is disabled (default or not present). |
| Restart requirements | No restart is required when creating or modifying this registry value. |
UPDATE JULY 7th, 2021
Benjamin Delpy @gentilkiwi released and updated a version of Mimikatz that demonstrates how to bypass the filtering in the released fix by simply avoiding the \ characters and denoting a UNC path using ??UNC instead.
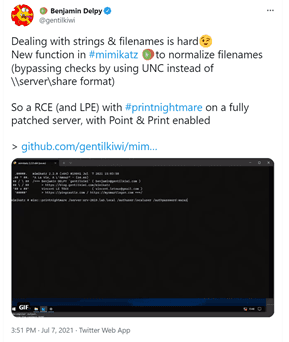
It is important to note that (according to @gentilkiwi) the bypass is related to the Point and Print feature!
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.
