Track down patient zero
Giving Forensics a Log Trail to Follow
Three steps that will help you track down and recover from ransomware or other malicious attacks.

The Challenge
The challenge with this is the lack of logfiles. The fact that they often also don’t contain enough information, don’t stretch far enough back or have been wiped. The difficulty here is how enabling logging for domain controllers, for example may cause the files to spiral out of control in size.
The Solutions
Unfortunately, there is no single solution to magically solve all of this. Using relatively simple tools we can increase the odds of success and give the forensics team a much better chance.
Let’s start with the high level steps and then drill down into what they actually mean.
- Increase the logging capabilities
- Turn on logging for PowerShell
- Enable off-site log shipping
Increase Logging Capabilities
This means turning on all the advanced audit logs for your on-premises domain. This can be done in several different ways, but the most common way is using Group Policy. If you are using the Microsoft Security Baselines for domain controllers (which you should) most your work is done! Even if you are using the security baselines they only affect what you log, and not how long they will be kept for. Since time is also a critical factor, increasing the file size will allow you to store the logs for a longer time period.
Turn On Logging for PowerShell
With the evolution of PowerShell and the increase of all the amazing capabilities of it so has the use of it for malicious intent. Fortunate we can track what our users are doing by enabling PowerShell logging. Again using Group Policy we can turn this on at scale quickly. Below is a good starting point.
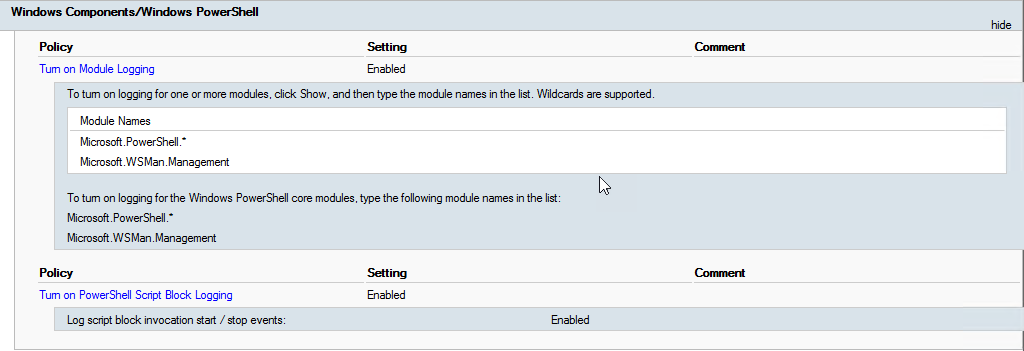
Enable Off-site Log Shipping
Even when extended logging is enabled, the logs are stored locally on each device. This creates a challenge when trying to quickly search and identify issues or breaches. To solve this a centralized log solution is needed. When implementing a central log solution select a tool that can be managed and stored off-site. This is important because of the same reasons off-site backups are. In the event of attack, a threat actor will often go after backups and log files to make recovery harder and hide their presence.
When you have a Microsoft focused environment a very good option is to use the Azure service Log Analytics. This service allows you to store logs for a very long time period as well as have a quick and easy way of searching all of combined log files. I’m not going to dive into the what and how Log Analytics works here but if you want to read more you can check out the official docs here https://docs.microsoft.com/en-us/azure/azure-monitor/log-query/log-query-overview#what-is-log-analytics
Summary
Doing these three steps will help you track down anything happening in your environment and assist in recovery should you be a target of ransomware or other malicious attacks. It is important to note even if you complete these steps it will not make you immune!
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.
