Recommended Advanced Audit Logging
This post will focus on how to accomplish this using GPO. You can, of course, accomplish the same thing using desired state configuration or other tools.

This is only a recommendation on a starting point. The general rule is you can never have to much logs. The challenge is finding a balance between logging enough and getting enough information.
This post will focus on how to accomplish this using GPO. You can of course accomplish the same thin using desired state configuration or other tools.
Creating a GPO
The settings for advanced audit policies can be found under Computer Configuration / Policies / Windows Settings / Security Settings / Advanced Audit Polcies / Audit Policies
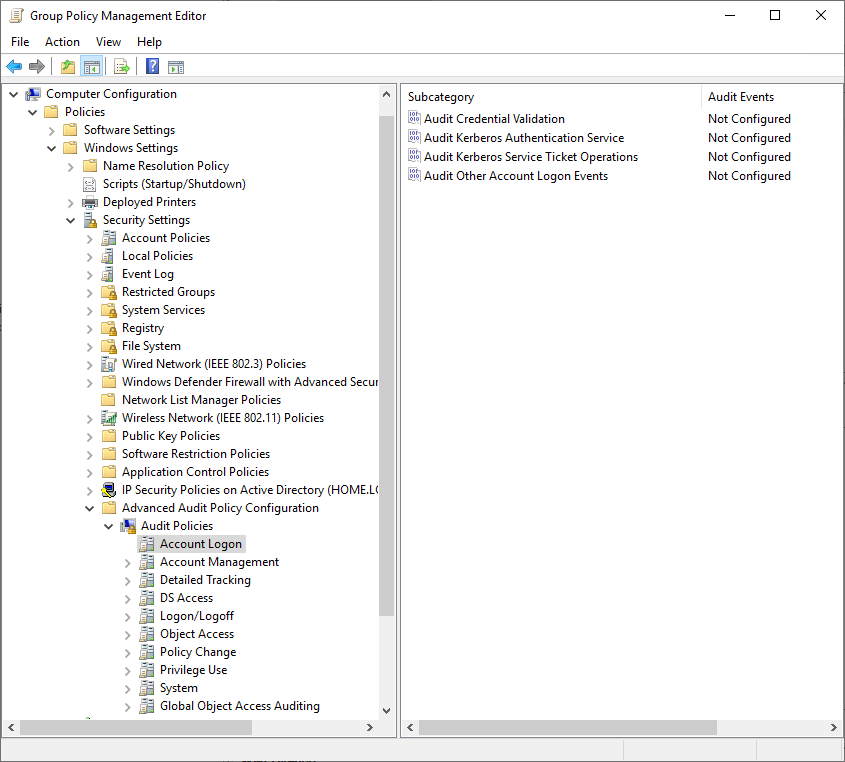
The following settings should be configured
- Account Logon
- Audit Credential Validation – Failure
- Audit Kerberos Authentication Service – Success, Failure
- Audit Kerberos Service Ticket Operations – Failure
- Audit Other Account Logon Events – Success, Failure
- Account Management
- Audit Application Group Management – Success
- Audit Computer Account Management – Success
- Audit Distribution Group Management – Success
- Audit Other Account Management Events – Success
- Audit Security Group Management – Success
- Audit User Account Management – Success, Failure
- Detailed Tracking
- Audit PNP Activity – Success
- Audit Process Creation – Success
- DS Access
- Audit Directory Service Access – Failure
- Audit Directory Service Changes – Success
- Logon/Logoff
- Audit Account Lockout Failure
- Audit Group Membership Success
- Audit Logon Success, Failure
- Audit Other Logon/Logoff Events Success, Failure
- Audit Special Logon Success
- Object Access
- Audit Detailed File Share Failure
- Audit File Share Success, Failure
- Audit Other Object Access Events Success, Failure
- Audit Removable Storage Success, Failure
- Policy Change
- Audit Audit Policy Change – Success
- Audit Authentication Policy Change – Success
- Audit MPSSVC Rule-Level Policy Change – Success, Failure
- Audit Other Policy Change Events – Failure
- Privilege Use
- Audit Sensitive Privilege Use – Success, Failure
- System
- Audit Other System Events – Success, Failure
- Audit Security State Change – Success
- Audit Security System Extension – Success
- Audit System Integrity -Success, Failure
Configuring the above settings will make sure the correct events are logged to allow tracking of most scenarios. This also means by default the event logs will rotate quickly and a long log trail will not be preserved. To make sure is not the case the following settings in Windows Components / Event Log Service should also be configured.
- Application
- Specify the maximum log file size (KB) Enabled
- Maximum Log Size (KB) 512000
- Security
- Specify the maximum log file size (KB) Enabled
- Maximum Log Size (KB) 512000
- Setup
- Specify the maximum log file size (KB) Enabled
- Maximum Log Size (KB) 512000
- System
- Specify the maximum log file size (KB) Enabled
- Maximum Log Size (KB) 512000
Import GPO using PowerShell
If you are like me and you have done this once and then thought, there has to be a better way. Don’t worry, there is – PowerShell to the rescue. Using PowerShell we can automatically read a GPO backup and then create and import the setting into that specific GPO. This all results in you being able to download the script and the GPO available at the end of this post and save yourself a lot of trouble.
To run the script simple run the following command and change the source location to where you have saved the GPO backup copy.
.Import-TSxGPO.ps1 -Source C:GPOBackup
When its done you would have a GPO imported that looks like the image below that can be linked to your domain controller OU.
The complete GPO and PowerShell script can be downloaded below for your convenience.
Read more
If you want to read more about this topic Microsoft has detailed information about what each version of Windows should have enabled for advanced audit logging. https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/audit-policy-recommendations
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.
