A Truesec Investigation
FIN12/Conti Syndicate Use TeamTNT Tools in Ransomware Attacks
Truesec can now confirm that a ransomware syndicate known as FIN12/Conti TeamTNT is using malware normally used in cryptojacking in their attacks.

We don’t know for sure who the individual behind this leak is. Officially, a Ukrainian researcher with the Twitter handle @ContiLeaks is behind it. Another likely explanation is that a Ukrainian affiliate of FIN12 decided they had enough when Conti openly supported the Russian war in Ukraine. It is known that in the world of cybercriminals, Russian and Ukrainian hackers have cooperated in the past, but FIN12 also has strong ties to Russian security services.
One of the interesting leaks that Truesec can now confirm is that the FIN12 ransomware syndicate is using tools associated with the threat actor TeamTNT, that is normally used for crypotjacking, in ransomware operations.
An Interesting Connection
In the vast dump of data released is a trove of most of the tools used by FIN12. In the file tree, we found the folder “/Conti Toolkit Leak/TeamTNTTools/Chimaera.Ngrok/*”

Figure 1: TeamTNT folder in Conti Leaks dump
In the folder are several malware tied to the Chimaera campaign, a known cryptojacking campaign linked to TeamTNT. This data strongly suggests that the FIN12 syndicate is now using TeamTNT tools, possibly to perform their own cryptojacking campaigns. It is theoretically possible that whoever is behind the Conti leaks also hacked TeamTNT and dumped their tools as well, so further confirmation would help strengthen the link.
From Cryptojacking to Ransomware
Truesec has, in the last six months, been assisting multiple organizations hit by the Conti ransomware. We have revisited a relatively recent case and found some very interesting data regarding the link between FIN12 and the TeamTNT tool set.
The victim organization was initially breached by a threat actor that used the Log4j vulnerability on a VMware horizon machine. The threat actor used this to deploy a cryptojacking malware. The cryptojacker ran for almost two months. Then another threat actor accessed the network, using the same entry point as the initial threat actor. This threat actor appears to have turned off the cryptojacker and then proceeded to recon the network using standard tools to expand their foothold. They then finally gained administrative privileges and deployed the Conti ransomware.
We found artifacts of the cryptojacker that included scripts that matched some of the files found in the Conti dump. For example, we have found a file called “mad.bat” that matches the file “init2.bat” in the Conti leaks dump.
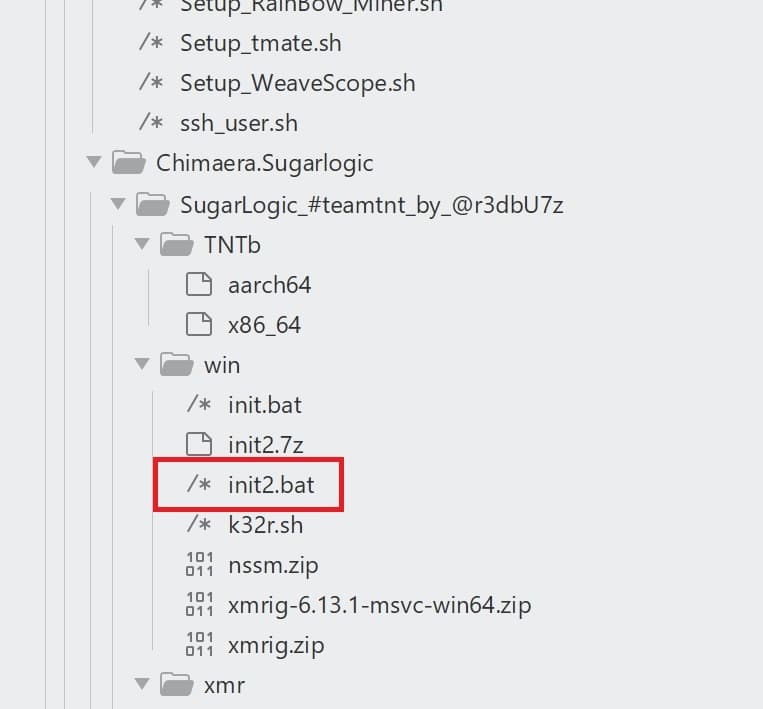
Figure 2: Chimaera cryptojacker script
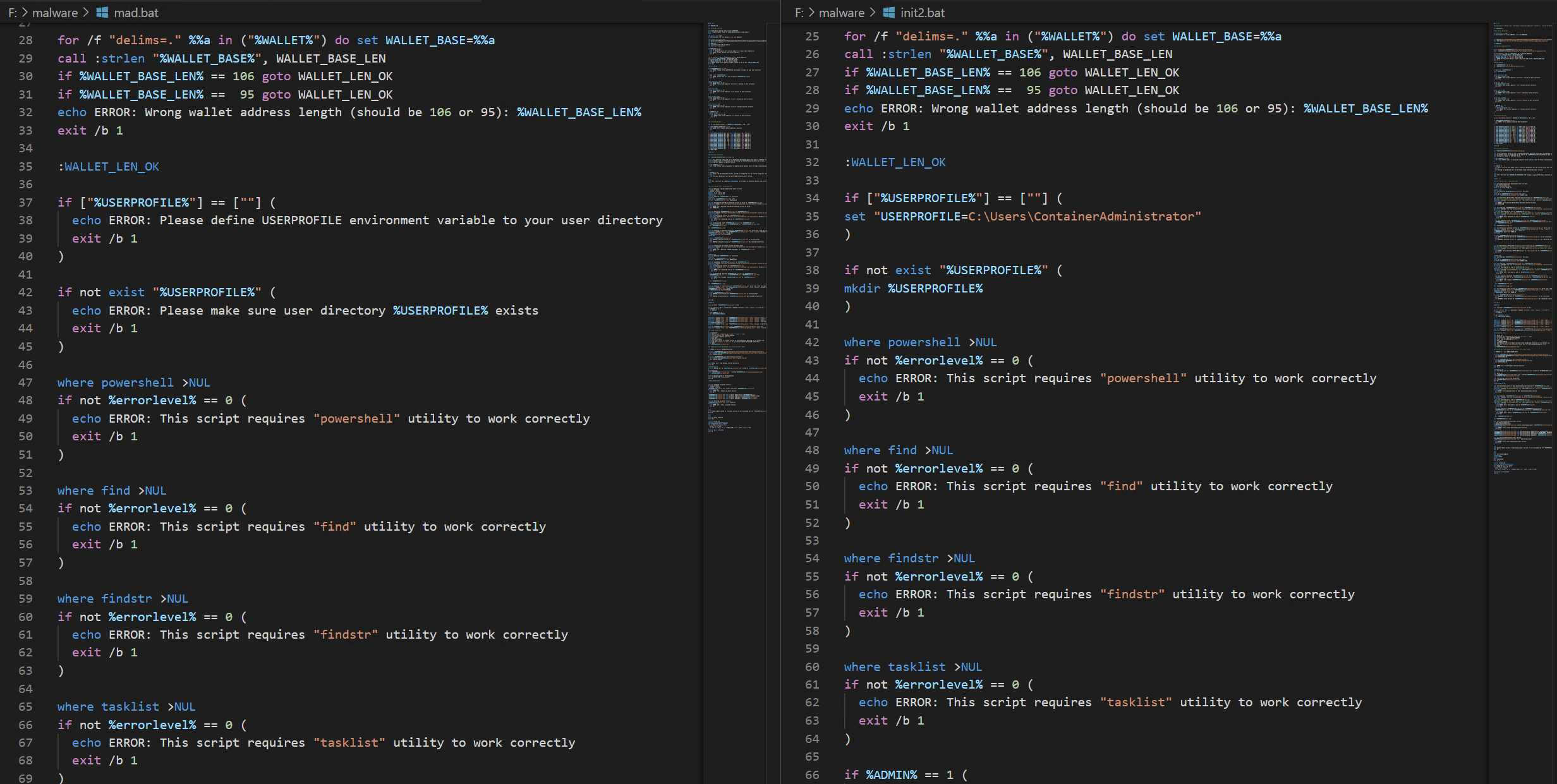
Figure 3: Side by Side comparison mad.bat (left) and init2.bat (right)
They are obviously the same file, just different versions. To further confirm that this is, in fact, TeamTNT and their Chimaera campaign, we compared the same file to published information on this campaign in other open sources. Just as we suspected, the same file was listed in the article about TeamTNT and Chimaera as well, but this time it was named “mad_mickey.bat.”
Conclusion
With this information, we are confident that the threat actor the sprawling FIN12/Conti cybercrime syndicate is using malware used in cryptojacking campaigns on victims they later deploy ransomware on. It is possible that FIN12 has obtained access to so many organizations they don’t have time to conduct ransomware attacks on all of them. Deploying cryptojacking malware, could be a way to monetize this access until they have time to attack them.
IOC
150.129.234.203:82 Download IP for Chimaera cryptojacking malware
51.222.121.180:82 Download IP for Chimaera cryptojacking malware
103.142.218.18:18 Download IP for Chimaera cryptojacking malware
45.32.120.201 C2 IP for persistence on VMware Horizon VM
176.113.115.107 Download IP for Atera Remote access used by Conti
193.27.228.127 Download IP for Atera Remote access used by Conti
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.
