Threat Insight
The Anatomy of a Business Email Compromise Attack (Part II)
In the previous part, we presented a high-level overview of Business Email Compromise (BEC) attacks. This time, we dive a bit deeper into the anatomy of such an attack, the different attack manoeuvres and entry vectors that put your organisation at risk.
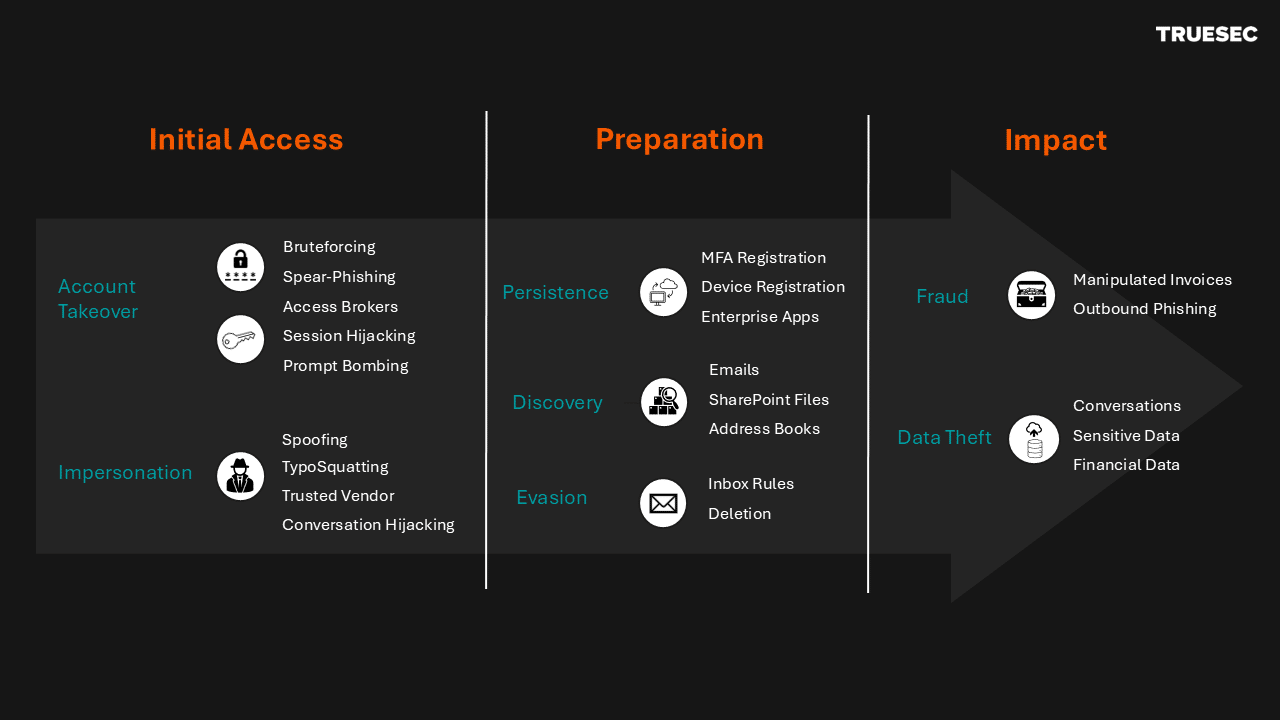
A Breakdown of Entry Vectors
The Internet is built of links – I’m supposed to click them, right?
BEC attacks almost always start with an Email Account Compromise (EAC) – in other words, an attacker gets control of someone’s email inbox.
Step one for attackers is to get their hands on your email address and password. Email addresses are not exactly top-secret: company websites, LinkedIn and event pages are goldmines for attackers.
Identifying your password typically takes a bit more effort: this requires that the threat actor either steals it, guesses it or potentially purchases it from a previous data breach. We could summarize this by saying that if your password is not “Summer24” and if you do not click on every link you see, then you are already less of a target.
Truesec summarized data gathered from a large number of BEC investigations, which shows that the most common account takeover tricks are:
- Phishing: The oldest trick in the digital scam book. An urgent email about outstanding payments or fake document reviews, click the link and – et voilà! – you are presented with a Microsoft login page. A fake Microsoft login page, as presented in the screenshot below:
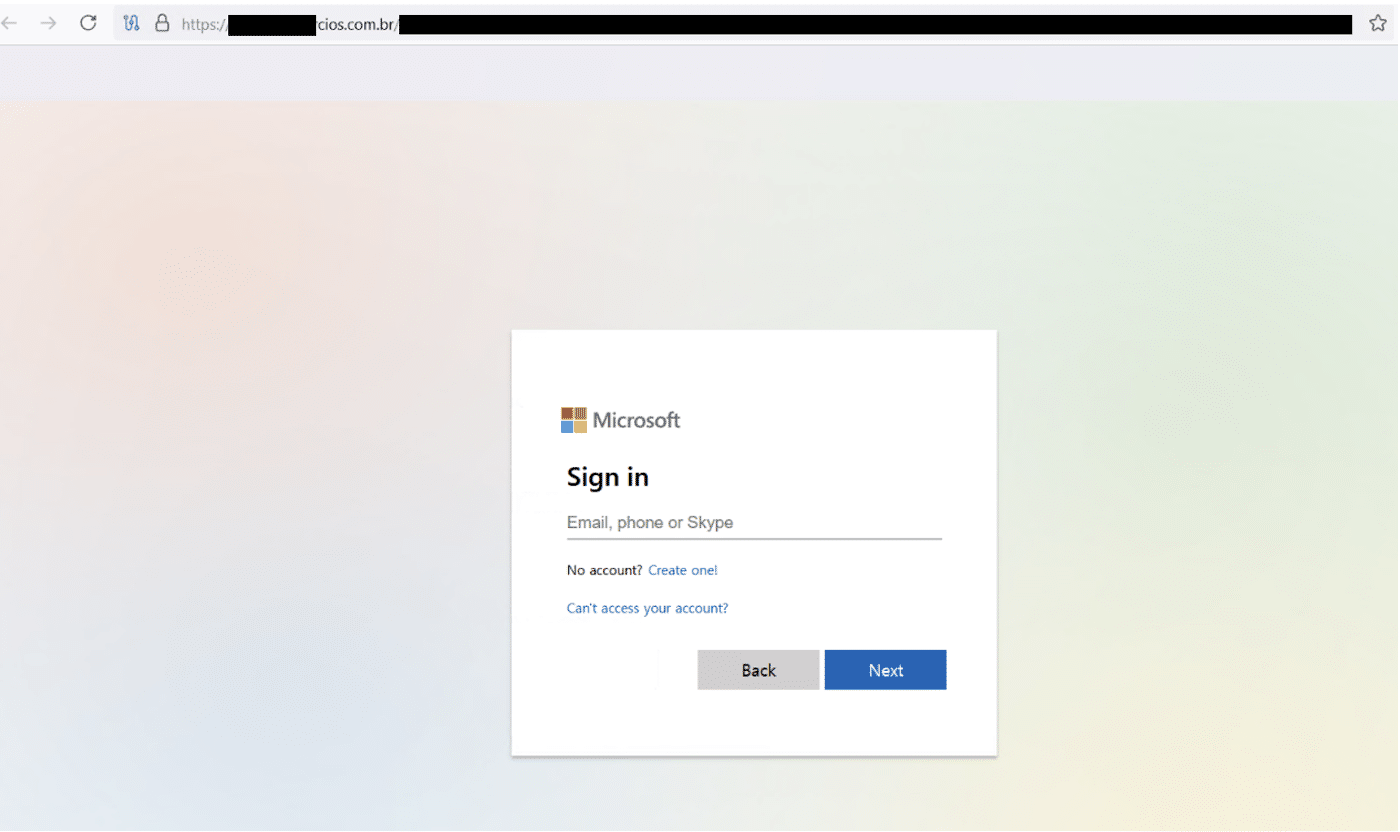
Thanks to AI, most phishing emails nowadays are quite polished and typo-free, and thereby a lot harder to spot than before.
- Bruteforcing: Your password was not “Summer24” but “Summer23”? Our condolences, someone just took over your email inbox. Bruteforcing is the act of systematically “guessing” passwords, until the correct one is found.
- Previous Credential Theft: Initial access brokers are attackers that focus on stealing and selling credentials on the darknet. If an access broker breached your account, chances are high you did not notice it and never changed your password. Unfortunately, you are now a sitting duck for anyone willing to pay a few bucks on credential dumpsites.
But I Have MFA …
Okay. Now they have my password – but wait – shouldn’t my accounts anyway be protected through multifactor authentication? Yes, they absolutely should. So why do we still see BEC attacks succeed, even with MFA in place?
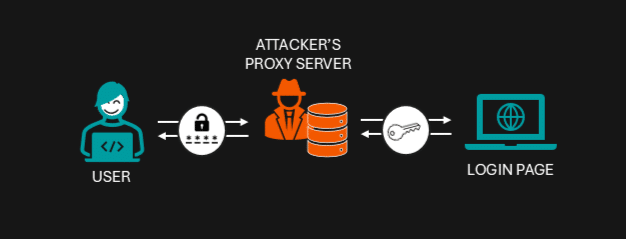
- AiTM Phishing & Session Hijacking: the so-called Adversary-in-the-middle (AiTM) is a type of attack where the attacker creates a proxy server between the user and the legitimate login page (often using “phishing-as-a-service” toolkits).
Upon clicking the link, you are directed to the attacker’s proxy server that is masquerading as the legitimate login page. Once you enter your credentials, the proxy server forwards them to the real Microsoft login page, which triggers an MFA prompt back to the proxy server which, yet again, forwards it to you. You see what seems like a valid and usual authentication process while the attacker intercepts your credentials and MFA codes, essentially stealing your session cookie and/or authentication tokens. This enables them to hijack your session—no need to re-enter credentials or MFA. Suddenly, despite MFA, the attacker is in your email inbox.
- Prompt Bombing and MFA Fatigue: suppose your credentials are stolen or brute-forced, and you have MFA enabled. You are in the middle of a meeting and, suddenly, you receive a flood of MFA prompts. You deny the requests but before long the incessant stream of prompts make you unable to focus on the meeting. Annoyed that denying the requests won’t make it stop, you finally approve one out of frustration, distraction, or exhaustion (= “MFA fatigue”). That is exactly what the attacker is aiming for.
Account compromises despite MFA may, of course, include various other attack techniques such as advanced social engineering attacks that involve calling or texting the user, ServiceDesk impersonations, SIM swaps or endpoint compromises.
I Didn’t Fall for It – Am I Safe?
Even if you’re vigilant, you may still become an indirect victim of a BEC attack, unfortunately. If someone else’s account is compromised, attackers will exploit the human instinct to trust partners and colleagues. Here is how these attacks can still succeed:
- Previous Data Leaks
- Supplier Breaches
- Conversation Hijacks
- Spoofed or Typosquatted Email Addresses
Previous data leaks within your organisation or breaches at a trusted partner organization can give attackers access to email threads, internal communication and inside information. This enables them to hijack conversations and makes it much harder for employees to tell illegitimate from legitimate claims. With access to previous email exchanges, attackers can mimic writing style, tone, grammar and language, blending seamlessly into ongoing conversations, a task that has been made a lot easier with the progress of generative AI.
Spoofed/typosquatted email addressesbear a strong resemblance to a legitimate email address and thus may trick victims into thinking that they are communicating with a trusted partner. For example, a threat actor may use the address support@microsof1[.]com and play on the resemblance of “1” and “t” to trick an unsuspecting user.
They Got In. Now What?
Once attackers have gained access to an email account, their next move is all about maximizing their foothold, learning about the environment, and setting the stage for their attack – all while staying under the radar. This preparation phase can last anywhere from a few minutes to several weeks, until they assess the perfect time and conditions to execute their fraudulent activities. Here is how they typically operate during this stage:
Establishing Persistence
The first concern the threat actor has is that they may lose access at any time, for example because their session expires. Thus, they will plant a type of “backdoor” access. This is crucial for the attacker to make sure they can access the account over an extended period of time. Common persistence techniques include:
- Adding their own MFA: by adding their own MFA device, they can bypass future MFA prompts and reduce the risk of being locked out.
- Registering a Device: the attacker registers their own device in order to establish it as trusted/compliant. This can help them reduce the number of authentication prompts and fulfil potential Conditional Access Policies.
- Installing Enterprise Applications: Installing enterprise applications (e.g., eM Client), with delegated permissions allows the attacker to keep access to the environment and receive new session tokens – even if the direct access to the compromised account is reset or revoked.
Discovery: What Can Be Exploited?
Next on the agenda, or even in parallel to the establishment of persistence, is “Discovery”. Often fully automated, attackers gather intelligence about the user, their roles, access rights and communication patterns, as well as identify valuable data which helps them to decide when and how to best exploit their access.
- Syncing Emails and Contacts: Attackers might sync the entire mailbox and address book to their infrastructure to view ongoing conversations and business relationships.
- Keyword Searches: automated scripts often involve searching mailboxes for keywords such as “invoice”, “payment”, “confidential” or relevant names, for example of company executives or financial partners.
- Analysing Communication Patterns: by reviewing email threads, they learn more about who handles financial information, upcoming payment deadlines, or potential personal absences. For the latter, consider that the threat actor may exploit the fact that the CFO is on vacation to impersonate them, using the vacation as a pretext to avoid any phone communications. Sounds familiar?
Evasion: Staying Under the Radar
To avoid detection, threat actors often create inbox rules that will e.g., move any email conversations they have steered or hijacked into a subfolder and mark those emails as read, rendering it basically impossible for the user to notice the suspicious activity in their inbox.
(For an example, check Understanding the Threat: What is Business Email Compromise? – Truesec)
They might furthermore delete the initial phishing email that helped them compromise the account to avoid a delayed detection through the user or the user’s IT department.
Execution and Impact
With persistence established and discovery completed, attackers move to the final stage: Execution with the purpose of financial gain and/or data theft. At this point, attackers are aware that their activities are more likely to be detected, and they usually act fast and decisively.
Financial Fraud
Attackers then send out fraudulent invoices or payment reminders to suppliers, trusted partners, or even within the organization, all based on the most credible scenario, often hijacking ongoing conversations. Due to the inbox rules set up earlier, these conversations usually remain hidden from the legitimate user who is none the wiser, unless someone verifies the request through another channel. In the incidents Truesec responded to, it was common to see multiple back-and-forth emails as the attacker answers follow-up questions, aiming to be as convincing as possible.
At this stage, it is your user awareness and internal verification processes vs. the attacker’s persuasiveness.

Data Theft
Simultaneously, the threat actor may, and usually does, exfiltrate whatever valuable data they find. Email threads that match financial keywords, SharePoint files related to HR and Finance, blueprints and Intellectual Property, whatever is deemed interesting.
Even if that data is not helpful in the current attack, it may fuel future attacks or have value if sold to the right party.
Credential Harvesting
If there is no clear gain opportunity through financial fraud, the attacker might pivot to stealing more credentials. In that case, a common technique for the attacker is to send a phishing email from the compromised account to the external contacts in the user’s address book. Often, the actual phishing link is hosted on the organization’s SharePoint, making the trap harder to spot for recipients.
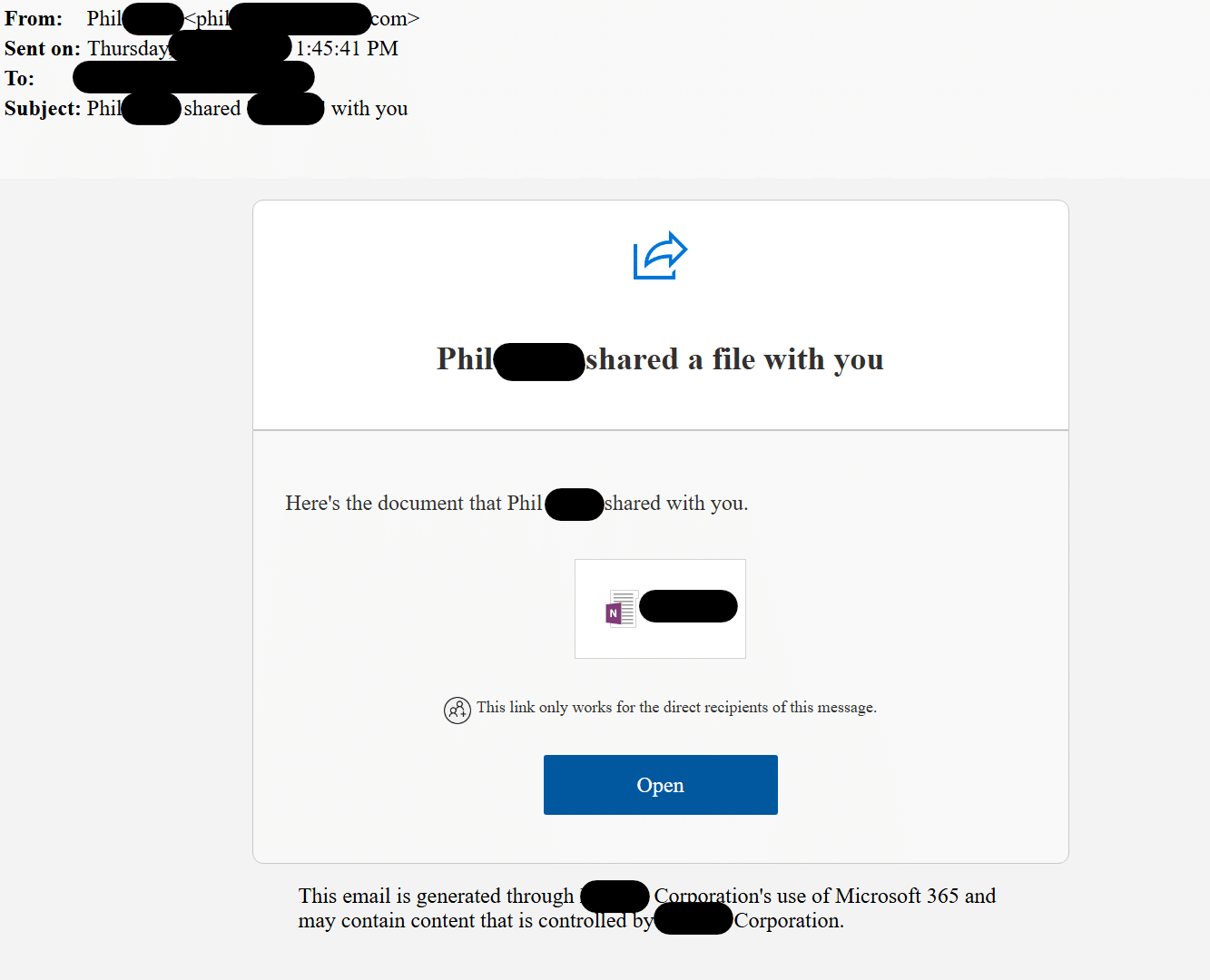
In the screenshot above, you can see the phishing email sent from a trusted account with a link to a OneNote document. Upon clicking “Open”, the victim is redirected to a malicious phishing page masquerading as Microsoft’s login page.
At this point, the impact of the attack depends on how prepared and vigilant your organization is, and how advanced the attacker’s tactics are.
Who Is Orchestrating Such Attacks?
Stay tuned for part 3 of our series, where Truesec’s Threat Intelligence Team reveals more about the threat actors behind BEC attacks, the links between various attacks and the crucial role a SOC plays in stopping them.
Stay secure – and remember, always verify before you click or pay!
Uncovering BEC Attacks – Blog Series Overview
Part I: “HELP! MY ACCOUNT GOT HACKED!“
Part III: Uncovering BEC Threats: How Threat Intelligence uses SOC and IR data
Part IV: Business Email Compromise – Prevention Strategies and Best Practices
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.
