Threat Insight
“HELP! MY ACCOUNT GOT HACKED!“ (Part I)
If any of this sounds familiar, you have likely encountered a threat that has become all too common in today’s digital workplace: “Business Email Compromise”, or in its short version, “BEC”.

What is Business Email Compromise?
Email is a prevalent method of communication that organizations use to conduct their business, to receive or send orders and invoices, and to communicate with their financial institutions, for example for the sake of submitting transactions such as payments.
As many of these communication flows ultimately involve money, cybercriminals have turned their attention to this medium and found ways to perpetrate their deeds:
At heart, BEC are attacks that involve account hijacking and sophisticated social engineering techniques to trick victims into disclosing sensitive information, into forging orders and invoices, and into authorizing fraudulent payments. BEC attacks are almost always highly targeted, with financial fraud as their primary motivation.
Unfortunately, BEC attacks are on the rise and affect organizations across all industries. ENISA, the European Union Agency for Cybersecurity, refers in their “Threat Landscape 2023” report to various cybersecurity vendors that observed a strong acceleration of this type of attacks. The FBI’s Internet Crime Complaint Center (IC3) received over 21,000 complaints about BEC attacks in 2024 with the total reported losses of more than $2.7 billion for the victims.
Let’s look at an exemplary BEC attack story:
“An attacker sent a phishing email towards employees at the finance department of a medium-sized company. Unfortunately, a Senior Accountant did not realize the scam and clicked on a link provided in the email that masqueraded as a login-protected OneDrive document requiring review. Upon clicking the link, a login page was opened resembling a Microsoft login page, and the Senior Accountant entered their credentials. Shortly afterwards, the attacker logged on to the account and read their latest email exchange about outstanding payments from a supplier. The attacker moved the last unread reply from the supplier to a sub-folder in the inbox and answered with an urgent and demanding message to immediately resolve the outstanding debt. Furthermore, the attacker informed them that their banking account had recently been changed and sent the modified invoice along. “
A demanding tone, an urgent request, and details that appear legitimate, all the signs of business correspondence. Except, of course, that this email was not really from the Senior Accountant. It was a trap that the threat actor skillfully crafted for the purpose of deceiving the supplier.
Let’s go over the typical methodology that threat actors use to perform these scams:
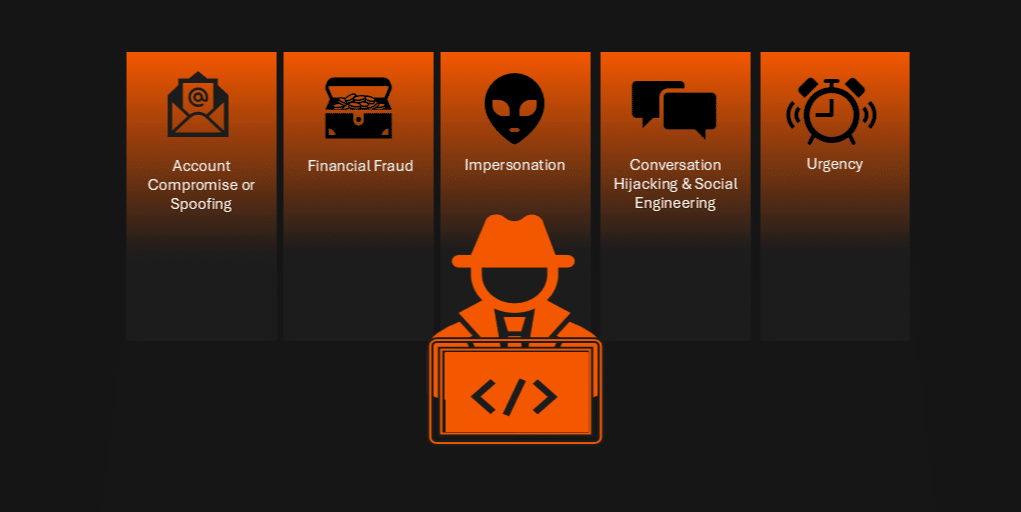
- Account Compromise or Spoofing: by compromising or spoofing a legitimate account, attackers raise their credibility for fraudulent requests.
- Financial Fraud: by sending forged invoices or altered payment details, attackers request money transfers into their own account.
- Impersonation: attackers often impersonate high ranking employees usually holding financial responsibilities, such as the CEO, the CFO, or an attorney, or trusted vendors to make their payment requests more credible and to add a high sense of authority to their demands.
- Conversation hijacking & Social Engineering: hijacking ongoing conversations and referencing confidential company information makes their requests seem like a natural continuation of business and allows them to receive sensitive information, modifying invoices and sending credible payment requests.
- Urgency: most attacks demand immediate actions, attempting to motivate employees to skip internal verification processes.
Who Do BEC Attacks Target?
BEC attacks usually victimize two or more individuals, as visualized in the graphic below.
- User A – The “Innocent Actor”: the attacker attempts to compromise this individual’s account or spoof their email address. Knowingly or unknowingly, individual A appears to be the initiator of the fraudulent communication.
- User B – The “Target”: this individual is tricked into paying the fraudulent invoice or disclosing sensitive information.

The individuals targeted by BEC attacks are often part of the following employee groups:
- New or junior employees: are less familiar with procedures and more likely to follow authoritative instructions without question.
- Executives and decision-makers: can authorize high-value transactions and hold access to sensitive information.
- Employees with financial authority: can authorize and initiate payments as part of their duties, making their requests less likely to be questioned.
- Employees with access to confidential data: hold access to sensitive HR or company data that can be exploited in future attacks.
Mapping BEC in the MITRE ATT&CK Framework
To better categorize these attacks, we can map them to the MITRE ATT&CK Framework, and among others to the following techniques:
- T1586.002 “Compromise Accounts: Email Accounts”,
- T1656 “Impersonation”,
- T1566 “Phishing”,
- T1534 “Internal Spearphishing” and
- T1565 “Data Manipulation”.
BEC vs. Phishing vs. Email Account Compromise: What Is the Difference?
It is easy to confuse the terms as these phrases are very often seen together, and a typical abuse of language in the industry is to extend “phishing” to also cover “email account compromise”, with many using these terms interchangeably. It is, however, important to keep in mind that they cover different aspects. Let’s review each term:
- Phishing describes an attack of sending emails to usually a high number of recipients, casting a wide net to steal credentials or deliver malware. However, even phishing can be used to bait specific recipients (“Spear-Phishing”).
- Email Account Compromise (EAC) refers to any type of account takeover/hijack, regardless of intent. Phishing attacks can lead to an EAC.
- Business Email Compromise (BEC) is a more targeted and strategic attack, that targets fewer individuals with the objective of financial fraud.
Ultimately, a successful phishing attack can lead to an EAC, which can be the initial stage of a Business Email Compromise.
_________________________________________________________________________________
Curious about how these attacks unfold?
In part 2 of our series, we dissect the BEC attack step by step. You can find it here: truesec.com/hub/blog/the-anatomy-of-a-business-email-compromise-attack.
Stay secure – and remember, always verify before you click or pay!
Uncovering BEC Attacks – Blog Series Overview
Part II: The Anatomy of a Business Email Compromise Attack
Part III: Uncovering BEC Threats: How Threat Intelligence uses SOC and IR data
Part IV: Business Email Compromise – Prevention Strategies and Best Practices
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.
