Vulnerability Management

What is Vulnerability Management?
We all know that vulnerabilities exist and that we need Vulnerability Management. The hard part is to know which ones YOU have, which ones are the most important to mitigate first, and then have a process to implement that change.
Vulnerability management is a systematic approach to managing security weaknesses, and it stands at the forefront of an effective cybersecurity strategy. We’ve designed this guide to walk you through the critical steps of identifying, assessing, prioritizing, and addressing vulnerabilities in your IT environment.
In 2022, we observed a rise in exploitation vulnerabilities as initial attack vectors, and in 2023, this trend has been magnified.
Download: The Truesec Threat Intelligence Report 2024
Almost 40% of all cyber attacks handled by our Incident Response Team involved the exploitation of a vulnerability in an internet-facing service to gain entry.
From Detection to Mitigation
Cyber vulnerabilities can be likened to the chinks in a suit of armor – tiny, but potentially fatal if discovered and exploited by an adversary. In the digital realm, these vulnerabilities range from software bugs and misconfigurations to insecure user behaviors. The consequences of unaddressed vulnerabilities are severe, potentially leading to data breaches, financial loss, and damaged reputations.
Recognizing the criticality of this issue, this guide aims to equip IT professionals, security analysts, and organizational leaders with the knowledge and tools to establish a robust vulnerability management program. From the initial detection of vulnerabilities to the final steps of mitigation and verification, we cover the essentials of securing your digital assets against known and emerging threats.
Chapter 1: Understanding Vulnerabilities
What Are Vulnerabilities?
In cybersecurity, a vulnerability refers to a weakness in an information system, application, service, appliance, or control that a threat actor could exploit. Vulnerabilities can arise from various sources, including software flaws, outdated systems, misconfigurations, and even human error. Therefore, understanding the nature and variety of vulnerabilities is the first step in defending against them.
The Impact of Vulnerabilities
The impact of vulnerabilities on an organization can be devastating. They can lead to unauthorized access, data theft, and even the complete shutdown of critical systems. Also, the ripple effect can result in financial losses, erosion of customer trust, and regulatory penalties. It’s not just the direct consequences that matter; the indirect effects, such as increased insurance premiums and the cost of remediation efforts, can also be significant.
Chapter 2: The Vulnerability Management Cycle
Overview of the Vulnerability Management Process
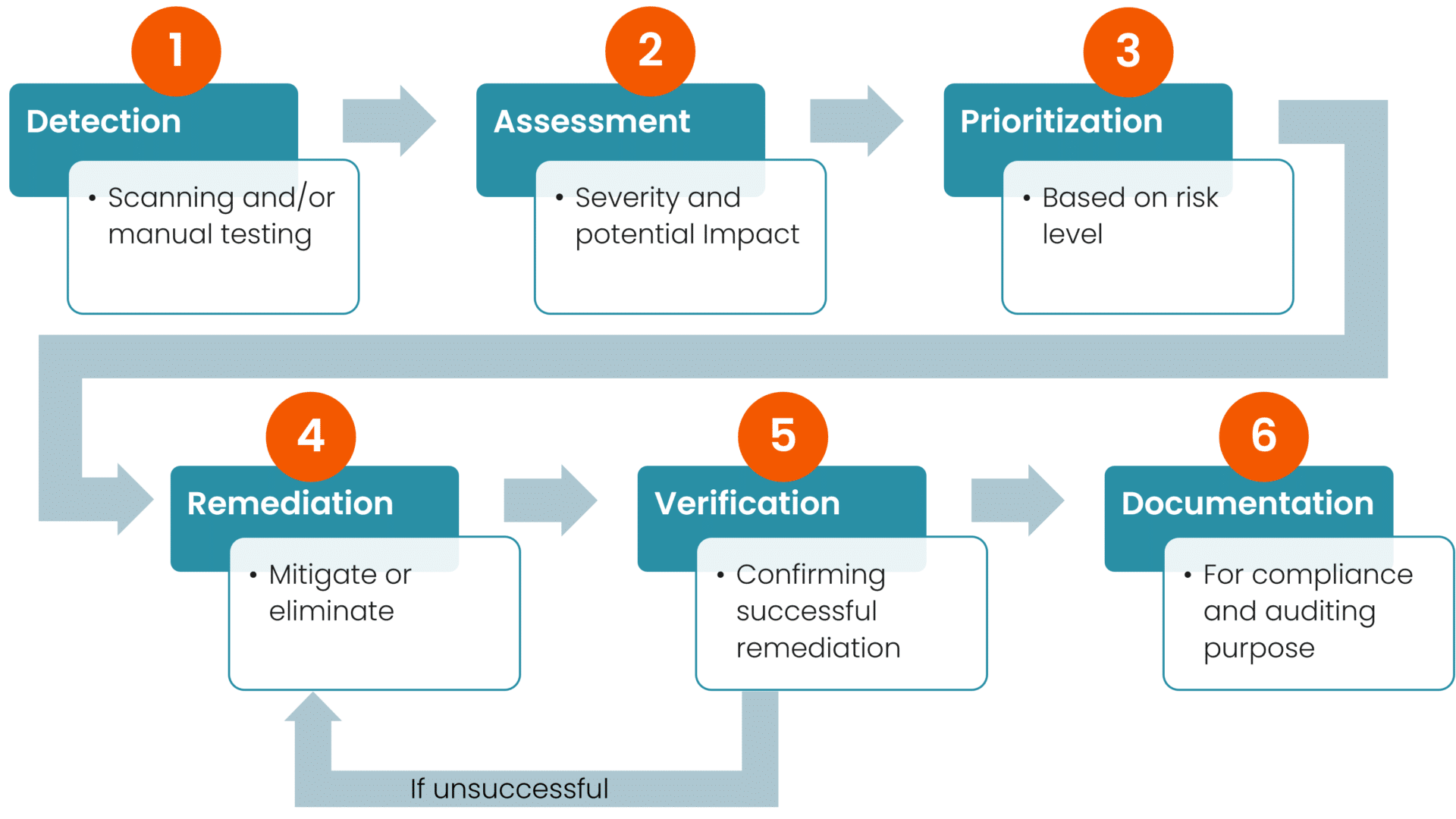
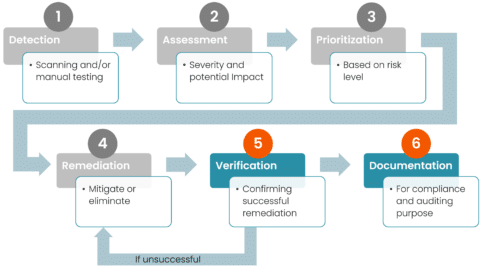
Vulnerability management is a continuous cycle that involves several key stages:
- Detection
Identification of vulnerabilities through automated scanning tools and manual testing. Automated scanning is performed over the network using local agents on the systems, while manual testing is performed by what is typically referred to as penetration testing. - Assessment
The evaluation of the severity and potential impact of detected vulnerabilities (often including one or more vulnerability scoring methods). An assessment must take into account technical defenses, the architecture of the system, and the potential impact on the business. To rephrase it, this stage will require an experienced analyst, with insights into the IT environment, and knowledge of business criticality. - Prioritization
Determining which vulnerabilities to address first, based on their risk level. An overview is made of all known vulnerabilities and their risk levels (severity and impact), and available resources (time, people, money) are prioritized for which vulnerabilities to remediate. - Remediation
Implementation of measures to mitigate or eliminate vulnerabilities. - Verification
Confirmation of the successful mitigation of the vulnerabilities. Typically performed during the next automated scan, this is a crucial step in minimizing a false sense of security. However, for cases that initially involved manual testing, an additional manual test should be conducted. - Documentation
Keeping detailed records of vulnerabilities and remediation actions for compliance and auditing purposes.
Best Practices for Continuous Vulnerability Management
A successful vulnerability management program is proactive, not reactive. It requires ongoing effort and attention to adapt to new threats and vulnerabilities. In general key best practices include:
- Regularly updating and patching systems and software. Systems that are exposed to the internet must be patched on the same day their updates are published.
- Assessing vulnerabilities comprehensively to identify potential weaknesses.
- Prioritizing remediation efforts based on the severity and impact of vulnerabilities.
- Educating employees about their role in maintaining cybersecurity.

In the subsequent chapters, we’ll delve deeper into each of these stages, offering insights into effective vulnerability detection techniques, assessment and prioritization criteria, and remediation strategies. Our goal is to provide a roadmap for developing a comprehensive vulnerability management program that safeguards your organization against the cybersecurity threats it faces daily.
Chapter 3: Vulnerability Detection Techniques (Step 1)
Effective vulnerability detection is pivotal to the cybersecurity defense mechanism. With it, you can identify the weak spots in your IT infrastructure before threat actors can exploit them. This chapter explores the tools and techniques essential for uncovering vulnerabilities.
Automated Scanning Tools Used in Vulnerability Management
Automated scanning tools are the linchpins of the detection process; they’re a scalable and efficient method to identify vulnerabilities across vast networks and systems. They typically fall under one of the following categories:
- Network Scanners scan the network for devices and identify vulnerabilities in their configurations and available services. Some of these focus on security weaknesses in web applications, such as SQL injection or cross-site scripting vulnerabilities.
- Agents installed on clients and servers analyze what’s running and installed on the device, then compare it against known vulnerabilities.
- Source Code Analysis, or static application security testing (SAST) tools, look for vulnerabilities in source code and source code repositories.
Selecting the right combination of these tools depends on your specific infrastructure and the types of applications your organization uses. In other words: regular use of these tools, combined with updates and customization to fit your environment, forms the backbone of an effective detection strategy.
Manual Testing and Assessment
While automated tools can identify a wide range of vulnerabilities, they may not catch everything. Therefore manual testing, often performed by skilled penetration testers, plays a crucial role in a comprehensive vulnerability detection program. Techniques include:
- Penetration Testing – Ethical hackers simulate cyber attacks to test the resilience of systems and identify vulnerabilities that automated tools might miss.
- Code Review – For applications, security experts can conduct manual reviews of source code to uncover security flaws that automated tools are not equipped to detect.
- Configuration Review – Manual examination of system configurations and network architecture can reveal misconfigurations or policy violations that could lead to vulnerabilities. Note: This type of testing is moving more and more into automated testing (e.g., in Cloud Security Posture Management).
Combining automated tools with manual testing provides a more complete picture of an organization’s security posture. It enables the detection of both common vulnerabilities and complex security issues that require human intuition and expertise to identify.
Chapter 4: Assessing and Prioritizing Vulnerabilities (Steps 2 and 3)
Following the detection of vulnerabilities, the next essential steps are assessing their severity and prioritizing them for remediation. This ensures that resources are allocated efficiently by focusing on the vulnerabilities that pose the greatest risk to the organization.
Vulnerability Assessment Explained
Vulnerability assessment involves analyzing the detected vulnerabilities to understand their potential impact on the organization’s assets and operations. This analysis considers the nature of the vulnerability, the systems affected, and the potential consequences of an exploit. The goal is to create a clear picture of the risk landscape faced by the organization.
Prioritization Criteria
Given the potentially large number of vulnerabilities that can exist within an organization’s systems at any given time, prioritization is crucial. We commonly prioritize vulnerabilities using the following criteria:
- Severity – The severity of a vulnerability, often measured by scores like the CVSS, provides a standardized way to assess the potential impact. We typically prioritize high-severity vulnerabilities that could lead to significant data breaches or system disruptions.
- Exploitability – Prioritization of vulnerabilities for which exploits are already available or those that require minimal skills to exploit. Specifically, the easier it is for an attacker to exploit a vulnerability, the more urgent it is to remediate it.
- Exposure – Determination of the level of exposure of the vulnerable system. In general, systems directly accessible from the internet or those housing sensitive information warrant higher priority.
- Business Impact – The potential impact on critical business processes or data integrity helps in prioritization. For example, we give precedence to vulnerabilities affecting systems critical to business operations.
It’s a complex puzzle to weigh these different categories. Especially since the impact on an organization can be devastating. To have highly experienced analysts, with top-tier, updated supporting tools is imperative for this to be a success.
(For more information about Vulnerability Scoring please see this article)
Tools and Techniques for Effective Assessment
Several tools and techniques can be employed to facilitate the assessment and prioritization process:
- Vulnerability Scanners With Prioritization Capabilities – Many advanced vulnerability scanners offer built-in prioritization features, often automatically ranking vulnerabilities based on severity, exploitability, and other factors. Notably, these tools often can’t assess the entire picture, for example, whether other security measures have been implemented. Therefore, a semi-manual approach is often required along with added human knowledge and experience.
- Risk Assessment Frameworks: Frameworks such as the National Institute of Standards and Technology (NIST) Risk Management Framework provide guidelines for assessing risks and prioritizing cybersecurity activities.
- Custom Scoring Systems: Organizations may develop their own scoring system to guide the prioritization of vulnerabilities, which can then be tailored to their specific risk tolerance and operational priorities.
Developing a Remediation Plan in Vulnerability Management
With vulnerabilities assessed and prioritized, the next step is to develop a comprehensive remediation plan. This plan outlines the steps taken to mitigate the highest-priority vulnerabilities, including timelines and responsibilities. However, the remediation plan must be flexible as new vulnerabilities are continually discovered, and the risk landscape continues to evolve.
Chapter 5: Remediation Strategies (Step 4)
Addressing vulnerabilities effectively requires a well-thought-out strategy that goes beyond merely applying patches. This chapter explores various remediation strategies and their application in different scenarios.
Patching and Software Updates
The most straightforward method of remediation is applying patches or updates provided by vendors. However, patch management can be challenging due to the volume of patches, the need (in some cases), to test them to ensure they don’t disrupt business operations, and the risk of patches not being available for certain vulnerabilities (also see virtual patching under the next heading).
Configuration Changes and Isolation
When patches are not available, or immediate patching is not feasible, alternative strategies include making configuration changes to mitigate the vulnerability or isolating vulnerable systems from the network to reduce the risk of exploitation.
There are also vendors (often when agents are present on the server/device) that can provide support for virtual patching. We’ve listed this under “Configuration Changes” because it’s not a patch, it’s more of a configuration in the agent that can intercept malicious calls.
Implementing Workarounds
In some cases, until a permanent solution can be implemented, vendors or security researchers may suggest workarounds or temporary fixes to reduce risk. Such workarounds must be carefully evaluated to ensure new vulnerabilities aren’t introduced.
Regular Review and Adjustment
The remediation plan requires regular review and adjustment based on the evolving threat landscape and the discovery of new vulnerabilities. This results in the organization’s vulnerability management efforts remaining effective over time.
Chapter 6: Verification and Reporting (Step 5 and 6)
After implementing the remediation strategies, it’s essential to verify the vulnerabilities have been effectively mitigated and document the process for compliance and improvement purposes.
Verifying Remediation Efforts
Verification is the process of confirming that applied fixes or mitigation strategies have indeed eliminated or reduced the identified vulnerabilities. Incidentally, there are many different ways of doing this.
Firstly, there’s rescanning which involves running additional vulnerability scans to ensure that previously identified vulnerabilities no longer exist. This helps to minimize misplaced trust in security that hasn’t yet been implemented (sometimes patches fail, or manual configuration is required for the patch to be applied.)
Secondly, there’s penetration testing which is a structured way of conducting targeted penetration tests to simulate attacks on the remediated systems, verifying that the vulnerabilities are not exploitable.
Thirdly, is the code review; here we look for application vulnerabilities. Performing a follow-up code review can confirm that code changes have resolved the issues without introducing new ones.
Notably, this list is not in any way an order of operation. Instead, these three are the most common methods, and you should use the ones that are most applicable to your environment or needs.
Reporting and Documentation in the Vulnerability Management Workflow
Documenting the vulnerability management process is crucial for several reasons, including compliance with regulatory requirements, facilitating future audits, and providing insights for improving the process.
The documentation should include details such as identified vulnerabilities, encompassing their severity, the systems affected, and the potential impact they may hold. Documentation also extends to the remediation actions undertaken to address each vulnerability. This includes information about the patches applied, any configuration changes made, and the implementation of workarounds. Furthermore, verification results serve as crucial evidence, confirming the successful mitigation of vulnerabilities. The outcomes of rescans, penetration tests, and code reviews support this process. Additionally, the process yields valuable lessons learned, offering insights that can guide future vulnerability management efforts. These insights spotlight areas for improvement, such as enhancing detection capabilities or refining remediation strategies, thereby informing a more effective approach to cybersecurity.
Maintaining comprehensive reports and documentation not only supports compliance and audit efforts but also enhances the organization’s understanding of its vulnerability management process. This insight is invaluable for refining strategies and improving cybersecurity resilience over time.
Chapter 7: Integrating Vulnerability Management Into Your Security Program
A robust vulnerability management program is not an isolated effort; it should be an integral part of an organization’s overall security strategy. Consequently, vulnerability management must be part of the daily work related to technical debt, risks, and defects in an IT environment. This chapter discusses how to weave vulnerability management seamlessly into the fabric of your security operations.
The Role of Vulnerability Management in a Security Operations Center (SOC)
The Security Operations Center (SOC) is the nerve center of an organization’s cybersecurity efforts, monitoring and analyzing security events around the clock. Therefore, integrating vulnerability management into SOC activities enhances the organization’s ability to respond rapidly and effectively to vulnerabilities and threats.
Incorporating vulnerability data into the SOC’s monitoring tools allows for real-time analysis and prioritization of threats.
With detailed information on existing vulnerabilities, the SOC team can tailor their incident response strategies to address the root causes of security breaches more effectively.
By having insights into the existing vulnerabilities in an IT environment, the knowledge of which vulnerabilities have known exploits, and intelligence on the active threat actors, and their tactics, techniques, and procedures (TTPs), a SOC team can also perform threat-hunting activities to investigate whether a vulnerability has been exploited.
Collaboration Across Departments
Vulnerability management is most effective when it involves collaboration across various departments within an organization. IT, security, compliance, and business units should work together to ensure a cohesive approach to managing vulnerabilities.
Chapter 8: Emerging Trends in Vulnerability Management
As technology evolves, so do the strategies and tools for managing vulnerabilities. This chapter explores emerging trends that are shaping the future of vulnerability management.
The Role of Artificial Intelligence and Machine Learning
Probably no surprise to anyone, AI and machine learning are becoming increasingly important in vulnerability management, offering new ways to predict, detect, and respond to vulnerabilities.
- Predictive Analytics – AI algorithms can analyze patterns in data to predict where vulnerabilities are likely to occur, allowing organizations to proactively address potential weak points.
- Automated Remediation – Machine learning can help automate the remediation of certain types of vulnerabilities, speeding up response times, and reducing the workload on security teams.
One challenge that AI and machine learning have at the moment is the assessment and prioritization of vulnerabilities. As IT environments become more and more standardized, the assessments will be more accurate.
Staying Ahead of Emerging Threats
The threat landscape is constantly changing, with new vulnerabilities and attack techniques continually emerging. Staying ahead requires constant vigilance and adaptability.
- Continuous Learning – Security professionals must continuously update their knowledge and skills to understand and combat new vulnerabilities.
- Collaboration and Information Sharing – Participating in industry forums and information-sharing platforms can provide early warnings about emerging threats and vulnerabilities.
Conclusion
Vulnerability management is a critical component of any organization’s cybersecurity strategy, requiring continuous effort and attention. From detection through to remediation, each step in the vulnerability management process is crucial for protecting against cyber threats. By integrating vulnerability management into broader security operations and staying informed about emerging trends, organizations can enhance their resilience against cyber attacks.
Get Started With Vulnerability Management
- Engage with the Community – Share your experiences and strategies for vulnerability management in professional forums and discussions.
- Continuous Improvement – Regularly review and update your vulnerability management practices to adapt to new challenges and technologies.
- Further Resources – Explore additional resources, training, and certification opportunities to deepen your understanding of vulnerability management and stay ahead of the curve.
Vulnerability management is an ongoing journey, not a destination. By fostering a culture of continuous improvement and collaboration, organizations can strengthen their defenses and protect their most valuable assets in an ever-changing cybersecurity landscape.