Holistic Cybersecurity Strategy
Holistic Cybersecurity – From Assessment to Strategy

A holistic approach to cybersecurity provides an effective program that is aligned with the business and that adjusts to changing circumstances in the world to help the organization minimize the risk of cyber breaches and their potential impact. This blog will explain the benefits of having Truesec perform a Holistic Cybersecurity Assessment and how this assessment can act as a springboard to a Holistic Cybersecurity Strategy.
What’s in a Word?
The word “holistic” is quite popular these days, in everything from healthcare to philosophy. Truesec’s approach to cybersecurity borrows from both of these disciplines, as well as many others. The word is generally explained as “relating to the whole of something or to the total system instead of just to its parts.” Holistic medicine looks at a person’s whole being rather than just taking care of the symptom and may include looking at that person’s mental and spiritual health as well. A holistic approach to philosophy examines a thought or behavior by looking at its context.
For Truesec, “successful” cybersecurity is when the organization we’re working with is measurably better at preventing cyber breaches and minimizing the impact of a breach over time. We feel the best way to accomplish this is by starting with a high-level look at the organization’s whole.
The Assessment Process
Truesec’s Holistic Cybersecurity Assessment consists of a series of workshops with representatives of an organization’s technical staff and IT leadership. We go through a series of questions about everything from governance and organization to specific technical solutions.
Truesec’s experts then go through and document where the organization is at and come up with recommendations for the next steps in the organization’s cybersecurity journey.
We assign a points value for each control, so if an organization repeats the process in the future, this can become a way of actually measuring progress over time.
Truesec delivers a report and a presentation and goes through this with the participants. At times Truesec presents its findings to the organization’s leadership constellation as well.
A Little About Frameworks (Very Little)
Truesec’s Holistic Cybersecurity Assessment is loosely built around the NIST framework. Currently, we feel this is the framework that has the most technical edge, and it’s one that most people are familiar with. There are also many cross-references from NIST to other frameworks, which makes it quite versatile. Guidelines to NIST Cybersecurity Framework – Truesec
However, we feel like the choice of framework is secondary to the strategic process. All frameworks can be implemented well or poorly, and no compliance or certification is ever a guarantee that you’re secure.
Frameworks are actually only that: A frame. How secure the actual house is depends entirely on how the organization builds it using this frame.
The Truesec Touch
Almost anyone can take a framework of their choice, ask some questions, assign a point value to the answers, and write a report with some standard recommendations based on the information gathered.
Truesec, however, has a wide breadth of cybersecurity experts. Their battle-tested experience and knowledge roll into our report and make it uniquely adjusted to this organization, this infrastructure, this industry, and this time.
- Truesec’s experts in Compliance and Law analyze the organization from a regulatory point of view and make sure the assessment process takes into consideration the legal requirements of the organization.
- Truesec’s Detect and Disarm operation (Secure Operations Center – “SOC”) monitors over 200,000 endpoints and can see trends change and risks emerge even as they happen. This information helps us formulate our recommendations based on actual current threats. https://www.truesec.com/how-we…
- Truesec’s Cybersecurity Incident Response Team (“CSIRT”) has handled over 170 major cybersecurity incidents in the past year. Their expertise in forensics and recovery gives us a very realistic view of how cyber attackers operate today. https://www.truesec.com/how-we…
- Truesec’s experts in Threat Intelligence (“TI”) and Human Threat Intelligence (“HTI”) monitor everything from the geo-political developments at any given time to how insider attacks are performed. They bring a unique view to an organization’s “target value” politically and economically. https://www.truesec.com/how-we… https://www.truesec.com/how-we…
- Truesec’s Secure Development group has expertise in writing secure code and the potential threats to a development environment.
- Truesec’s Secure Infrastructure domain provides expert guidance in on-premise and cloud infrastructure and helps us provide recommendations based on the organization’s specific infrastructure and network design.
- Last but not least, Truesec has experienced Cybersecurity Strategists who can help bring cybersecurity recommendations to life and become tangible measures that are risk-based and cost-effective.
These sources of input make our recommendations well founded both in the threat and risk landscape as it looks right now, but also adjusted to the organization’s unique infrastructure and place in the world.
Ancillary Benefits
Following the assessment, the organization will receive a report and presentation that outlines our recommendations based on the workshops and interviews. This is the tangible deliverable from this assignment.
Many customers also report various indirect benefits from the way Truesec performs this assessment:
- Framework Education – Most IT organizations have read frameworks up and down, but at times there’s a disconnect between the language in the framework and actual activities. Truesec has vast experience in compliance and implementing security measures, and we can explain and give examples of the kinds of mitigating actions that a control may refer to.
- Cybersecurity Coordination – It would be nice if most organizations had regular meetings between all involved parties where cybersecurity is discussed, but this is often not the case. We regularly hear “It’s nice to get to sit down and talk about these things” as feedback from our workshops.
- Annual Internal Cybersecurity Conference – We have customers who perform assessments yearly to promote their progress and ensure they don’t lose momentum. Some of them invite a broader group of participants than is actually necessary and use it to bring the whole organization into sync about their cybersecurity efforts.
- A Fresh Voice – An outside resource like Truesec can provide a refreshed dialog for the organization’s management and its user community.
Time To Lower Risk
In addition to the findings that come out of the assessment process, Truesec sometimes takes into consideration the kinds of activities an organization can undertake to buy themselves a bit of time in the upstart of a new program while the cybersecurity strategy is implemented.
We call this our “Time To Lower Risk” list. The focus is on quick hits, sort of “quick and dirty,” where the 80-20 rule is solidly in effect and “Good Enough” often is good enough.
Depending on where an organization starts out, this may include vulnerability scans, IP scans, a SOC agreement, an incident-readiness assessment, and an analysis of the organization’s elevated access.
What Can a Strategic Cybersecurity Advisor Do for You?
So you have a report, Truesec’s consultants have given a presentation, and Truesec’s salespeople have given you an invoice (albeit a very reasonable one).
Now what?
Some organizations have a ready-to-receive cybersecurity program where the recommendations from the assessment slot right in and get prioritized alongside other initiatives. They have governance and the appropriate resources and processes in place to handle the requirements.
However, most organizations aren’t like that, and we feel these organizations would benefit from entering a strategic cybersecurity partnership with an external specialist. This will provide a new pair of unbiased eyes on the environment and the organization and a new voice to promote cybersecurity initiatives internally, both upwards and outwards.
This kind of partnership can give an organization access to expertise and resources that are very difficult to come by through recruiting, and it’s a slow process even if it’s successful.
A Strategic Cybersecurity Advisor will help the organization lay out a plan that is both operational, tactical, and strategic.
- An operational activity that’s performed now won’t stand on its own because it will fit into the strategic direction for 24 months out.
- A compliance requirement will be easier to mitigate because we’ll have a clear picture of our cybersecurity capabilities.
- We’ll get our money’s worth from digital investments because we’ll ensure tools are configured correctly and operated and managed properly.
- The organization is reassessed annually to provide a consistent measure of progress.
- And the organization will have a cybersecurity strategy as dynamic and flexible as the threat landscape it’s designed to protect us from.
A Strategic Cybersecurity Advisor will also help coordinate the operational and tactical activities of an IT organization so that they, in the long term, contribute to the organization’s strategy.
A Sample Strategy
In its very nature, a strategy is designed to be more fluid than a project plan or similar. It really is “more of a guideline.” We typically break down activities into multiple horizons and divide them between technical and organizational activities. At its highest level, it could look something like this:
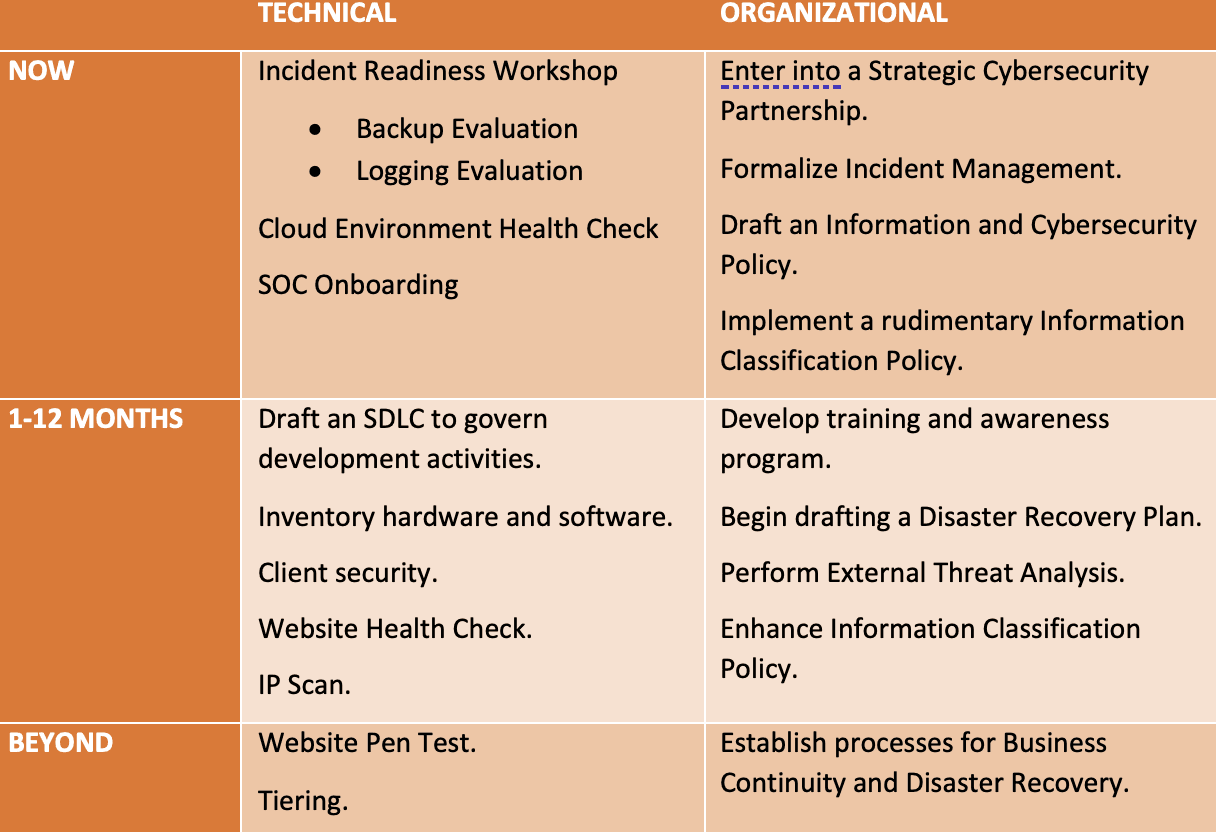
Written by: Stefan Jansson, Senior Strategic Cybersecurity Expert
Contact: stefan.jansson@truesec.com
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.