Managed Detection and Response
What Is Managed Detection and Response (MDR)?
Managed detection and response (MDR) services combine network, identity, cloud, OT, logs, and endpoint cybersecurity technologies. Organizations can manage these services internally, or they can be managed externally by a third-party provider. Specifically, this could be a “managed service provider (MSP)” or “managed security service provider (MSSP).”
MDR focuses on threat detection and response.
- Threat detection is detecting whether someone or something is doing bad things in the IT or OT environment).
- The response is stopping the threat, investigating what has happened, and ensuring the same thing shouldn’t happen again.
Obtaining this service from an MSP or MSSP helps organizations tackle several challenges. It helps to address the difficulty of hiring skilled in-house cybersecurity personnel. It can also eliminate the costs associated with training and maintaining their skill level with the latest threat information. Furthermore, it minimizes or completely negates the need to integrate advanced analytics and detection and response tools.
For further information, refer to the SANS Report The State of MDR and Bitdefender’s article on the 2023 MDR landscape What the MDR Landscape Will Look Like in 2023.
Understanding Managed Detection and Response
MDR generates alerts using different technical capabilities and human expertise. It investigates whether an alert is a false positive or a true positive that indicates an ongoing breach or an information leak. Additionally, MDR ensures rapid response to contain and remediate threats.
Definition and Core Components of MDR
Managed detection and response (MDR) is an integrated approach to cybersecurity that combines technology and expert analysis to proactively prevent breaches. Its core components include:
- Advanced Detection – Utilizing AI, machine learning, and custom detections to identify threats that traditional tools might miss.
- Response and Mitigation – Rapid response to threats, including containment and remediation strategies.
- Continuous Monitoring and Active Threat Hunting – Ongoing surveillance 24/7/365 of networks and systems to detect any suspicious activities.
- Expert Analysis – Skilled cybersecurity professionals who analyze threats and tailor responses.
- Threat Intelligence – Leveraging global cyber threat information to predict and prevent attacks.
Distinction From Traditional Security Measures
MDR differs significantly from traditional security measures in several ways:
- Proactivity Versus Reactivity – Traditional methods often focus on reacting to breaches after they occur. In contrast, MDR emphasizes proactive threat hunting and prevention.
- Integration of Expertise – Unlike traditional methods that might rely heavily on automated tools, MDR blends technology with human expertise for a more nuanced threat analysis.
- Adaptability – MDR services adapt more quickly to the evolving threat landscape, whereas traditional measures may become outdated against new types of attacks.
- Holistic Approach – MDR provides a more comprehensive view of an organization’s security posture. It goes beyond perimeter defense to include internal network monitoring and response.

Industries and Sectors
Managed detection and response (MDR) services are created to meet the unique cybersecurity needs of various industries:
- In sectors like finance, professional services, and healthcare, MDR provides stringent data protection against breaches, complying with industry-specific regulations.
- For retail and e-commerce, MDR focuses on securing transaction data and customer information.
- In manufacturing and utility sectors, MDR is crucial for protecting infrastructure and operational technology from cyber threats.
- Just to mention a few…
Addressing Cybersecurity Challenges With MDR
MDR addresses key cybersecurity challenges by offering real-time threat detection and response. This is crucial for industries facing sophisticated cyber attacks (see Cybernews about how fast threat actors can encrypt your data). Its proactive stance is essential for sectors handling sensitive data, where breaches can have significant consequences. MDR’s adaptability makes it suitable for various industries. It ensures they can stay ahead of evolving threats and maintain compliance with industry-specific cybersecurity regulations (e.g., EU Cybersecurity Act).

MDR vs. MSSPs
To distinguish a managed detection and response (MDR) service from managed security service providers (MSSPs), you must compare how and whether they focus on proactive threat hunting, detection, and response. MDR offers more in-depth analysis and real-time action against cybersecurity threats, employing advanced technologies and expert human analysis. MSSPs, while providing a broader range of security services, tend to focus more on general security management and compliance, often utilizing more automated approaches. MDR services are tailored to modern cybersecurity challenges. This provides deeper and more immediate protection against sophisticated cyber threats.
It’s important to note that MSSPs can have many different security services in their portfolios, and MDR may be one of them. When looking for an MDR service, you should ensure that it fits YOUR organization’s requirements. It should fit the environment YOUR organization has to defend. Additionally, it must be able to utilize YOUR organization’s licenses and investments.
A general MSSP with numerous security services can be the perfect fit for you, but not all MSSPs are created equal. Some have a background in IT operations and added security, while others come from a threat-centric or consulting mindset and have evolved these into managed services.
“MDR offers more in-depth analysis and real-time action against cybersecurity threats.”
Fundamental Components for Effective MDR
Effective managed detection and response (MDR) relies on a blend of advanced technologies and human expertise to deliver proactive and comprehensive cybersecurity. It encompasses key elements like robust threat detection, rapid response strategies, in-depth analysis of security threats, utilization of cutting-edge technology, and the critical role of skilled cybersecurity professionals. Each component plays a vital role in forming a cohesive MDR strategy – a strategy that effectively combats the evolving landscape of cyber threats.
Threat Detection
Effective managed detection and response (MDR) begins with robust threat detection. This involves continuous monitoring of endpoints, identities, networks, and systems, employing advanced technologies like AI, machine learning, and custom detections. It identifies potential security threats before they escalate, ranging from malware intrusions to unusual activity.
Analysis
Analysis in MDR involves examining detected threats to understand their nature and impact. This continuous process helps in refining detection capabilities and response strategies. MDR analysts assess threat patterns, vulnerabilities, and attack vectors to enhance overall security posture.
Response Strategies
Once a threat is analyzed and detected, rapid and strategic response becomes crucial. MDR employs predefined response protocols to mitigate and contain threats quickly. These strategies include:
- Isolating affected systems
- Locking user accounts
- Requiring reauthentication
- Blocking malicious traffic
- Implementing other necessary measures to prevent further damage
Technology
The technological backbone of MDR includes advanced tools like endpoint detection and response (EDR), security information and event management (SIEM) systems, identity detection and response (IDR), cloud detection and response (CDR), and sophisticated network monitoring solutions (NDR). These technologies facilitate comprehensive surveillance and rapid response capabilities.
Human Expertise
The human element in MDR is vital. Skilled cybersecurity professionals analyze complex data, providing insights that automated systems might miss. Their expertise and mindset are crucial in interpreting alerts, managing responses, and evolving strategies to counter new types of cyber threats.
The Right MDR Provider
Selecting the right managed detection and response (MDR) provider is crucial for effective cybersecurity. When choosing an MDR provider, consider factors such as their expertise in the field, the technologies they employ, and their track record handling cybersecurity threats. Truesec stands out in this regard, offering a robust MDR service backed by deep cybersecurity expertise and state-of-the-art technology.
Key considerations when choosing your MDR provider include:
- Expertise and Experience – Look for a provider with a strong background in cybersecurity. Truesec’s team of experts has extensive experience identifying and mitigating complex cyber threats.
- Advanced Technology – Ensure the provider uses the latest technologies, such as AI, machine learning, and comprehensive threat intelligence. Truesec employs cutting-edge tools to offer dynamic threat detection and response.
- Customized Solutions – Choose a provider that offers tailored services to meet your specific needs. Truesec’s approach involves customizing the MDR services to align with your organization’s unique cybersecurity challenges.
- Proven Success – Consider providers with a proven track record of successfully mitigating cyber threats. Truesec’s portfolio includes successful case studies where we have effectively protected clients from sophisticated cyber attacks. For example, in 2023, we sent our customers 13,921 incident reports for threats we had detected and responded to.
- Comprehensive Services – A good MDR provider should offer a range of services, from threat detection to response and recovery. Truesec provides an all-encompassing MDR service, ensuring complete protection against cyber threats.
In summary, the right MDR provider should not only offer advanced technological solutions but also a deep understanding of the cybersecurity landscape tailored to your organization’s needs. Truesec’s MDR service encapsulates these elements, making it a strong contender for organizations seeking robust cybersecurity solutions.
Innovations in MDR – Truesec Platform
AI and Machine Learning – Ensuring They Actually Work
We perform thorough and structured evaluations multiple times annually (read more about parts of this work here). This is to guarantee our platform adopts the most advanced detection and response solutions available, solutions that incorporate AI and machine learning in different ways. These solutions specifically excel in detecting current and emerging cyber threats and threat actors. We use proprietary tools and detection methods alongside a strict selection process. This ensures the Truesec MDR platform stays cutting edge in cybersecurity. It offers unmatched protection against the dynamic landscape of digital threats.
AI and machine learning are fantastic tools for increasing efficiency and decreasing response times. They also speed up investigations, compile facts, and help generate reports. All this enables people to have as much time as possible to do what they are best at – analyzing the tricky and unusual incidents that AI or ML can’t make sense of.
Employee Training
A critical component of an MDR strategy must be comprehensive employee training. Truesec recognizes that human factors are often cybersecurity’s weakest link. Hence, they emphasize staff training to recognize cyber threats. This includes identifying phishing attacks, malware, and other threats. This training empowers employees with the knowledge that they’re often the first line of defense. It also cultivates a culture of cybersecurity awareness in the organization. By combining cutting-edge technology with informed and vigilant staff, Truesec’s MDR service provides a multi-layered defense against cyber threats.
These trainings must be continuous, with many scheduled trainings each week and ad-hoc trainings when new threats or patterns are found. The mindset of “never stop learning,” always watching for new ways of detecting and responding, and sharing this knowledge must be an integrated part of the organization.
Cybersecurity Strategies – MDR and Incident Response Planning
Truesec offers a variety of cybersecurity services that complement the Managed Detection and Response (MDR) service. These include:
- Digital Forensics and Incident Response, which provide efficient response to cyber attacks.
- Incident Preparedness to enhance cybersecurity readiness.
- Threat Intelligence for predicting attacks.
- Penetration Testing for active security testing.
- Governance, Risk, and Compliance services for maintaining industry standards.
- Vulnerability and Posture Management for proactively finding and fixing misconfigurations or vulnerabilities. (read also a general description of Vulnerability Management here)
- Identity and Access Management (IAM) to streamline your identity management and access processes.
- Application Security to secure your development processes.
Each service synergizes with MDR to offer a comprehensive cybersecurity solution.
Legal Aspects in MDR
The legal and regulatory aspects of managed detection and response (MDR) are critical, particularly in compliance with data privacy regulations like GDPR and CCPA.
In the field of MDR, two common approaches are seen regarding data management and platform hosting.
- The first involves using best-of-breed tools within the customer’s own IT environment or tenant. This method emphasizes customer control and ownership of their data.
- The second approach sees the MDR provider hosting the MDR platform in-house, with customer data managed on the provider’s platform.
Each approach has different implications for data sovereignty and operational flexibility regarding service migration and data control.
Post-Incident Analysis and Reporting in MDR
Post-incident analysis and reporting are crucial components of MDR services. After a cybersecurity incident, MDR providers conduct thorough analyses to understand the incident’s cause, scope, and impact. This involves investigating how the breach occurred, identifying the vulnerabilities exploited, and assessing the overall damage. The findings are compiled into detailed reports. These provide actionable insights into the incident and offer recommendations to prevent similar future occurrences. These reports are essential for continuous improvement in cybersecurity strategies and for meeting compliance requirements regarding incident documentation.
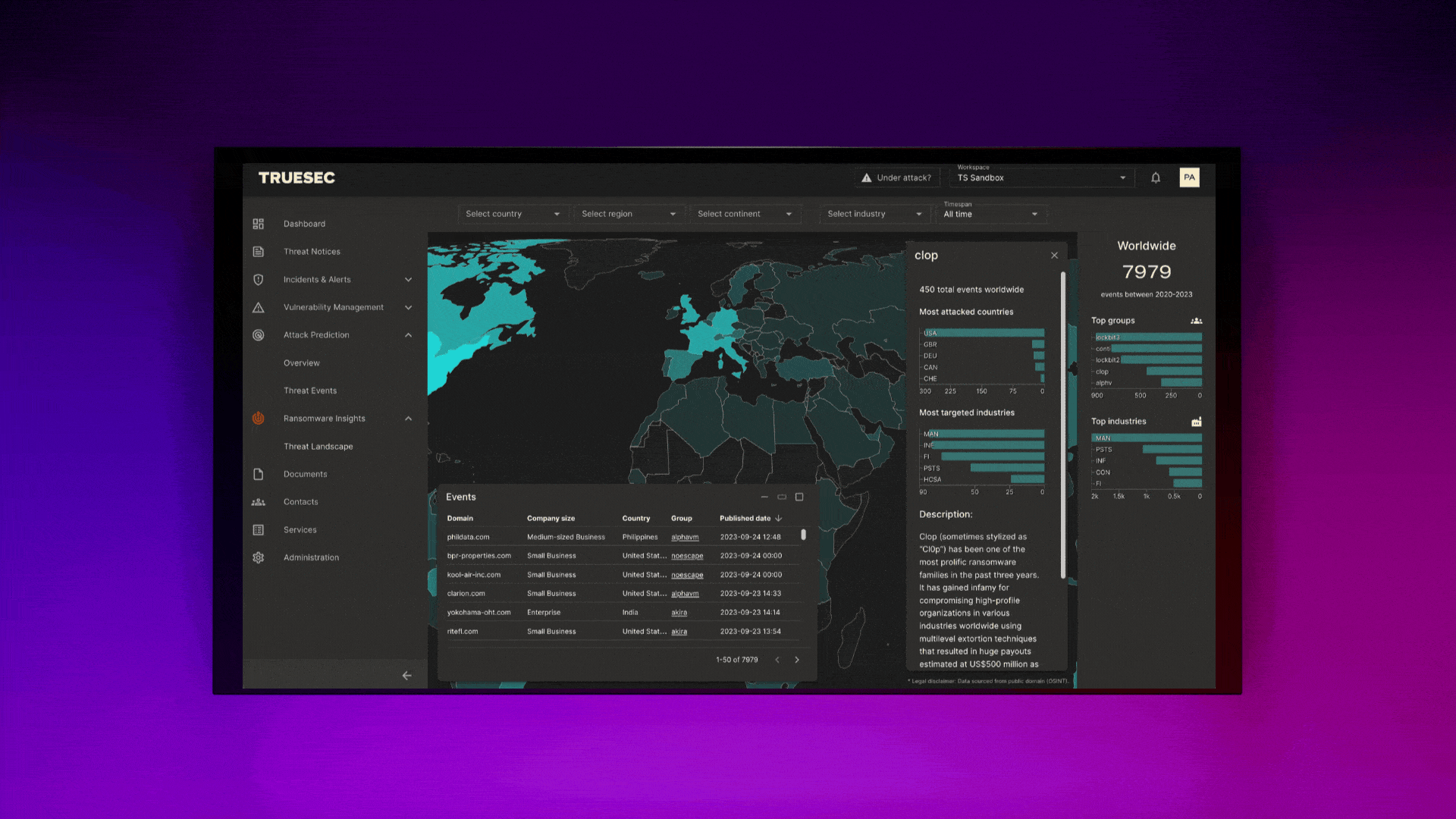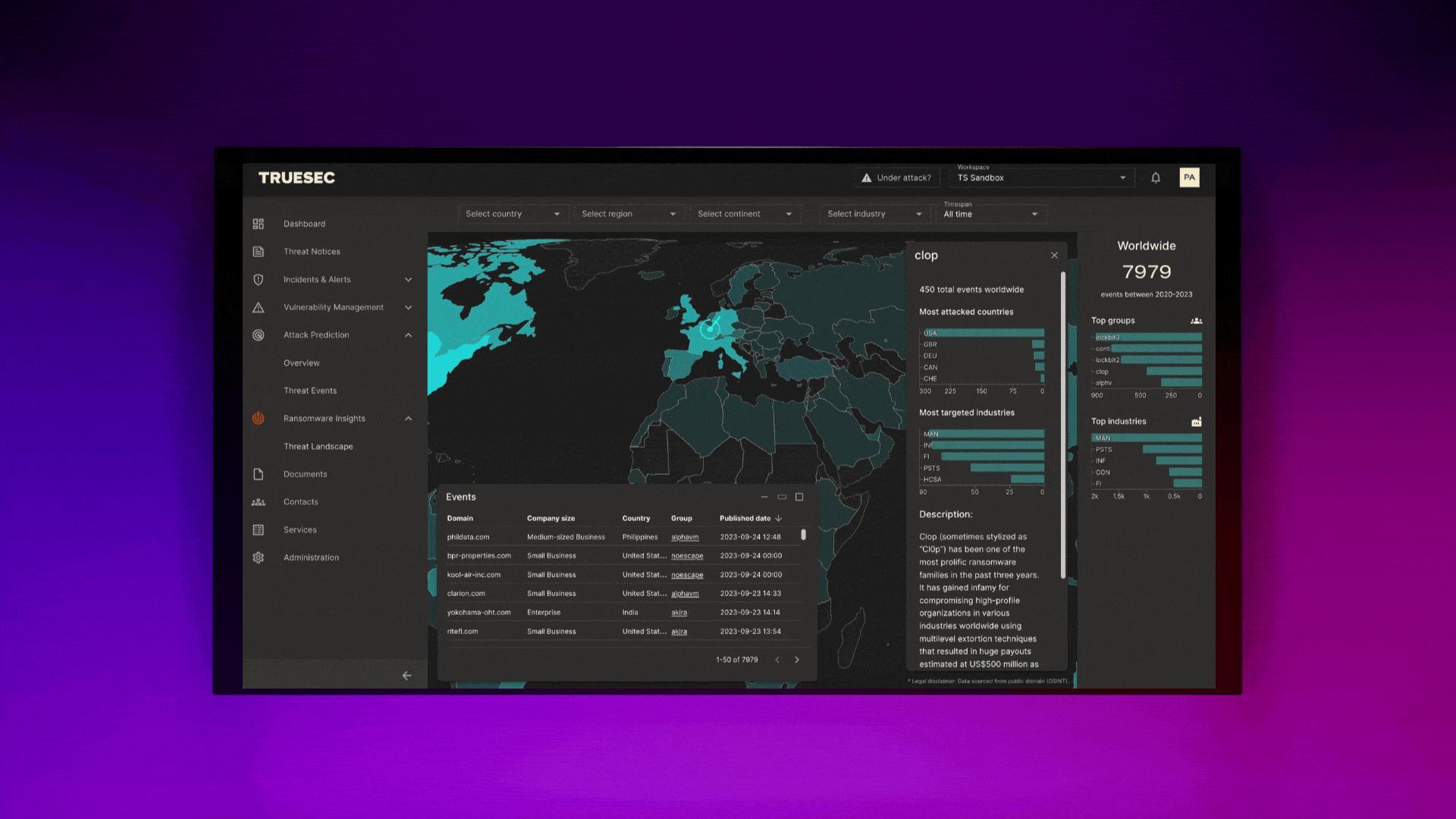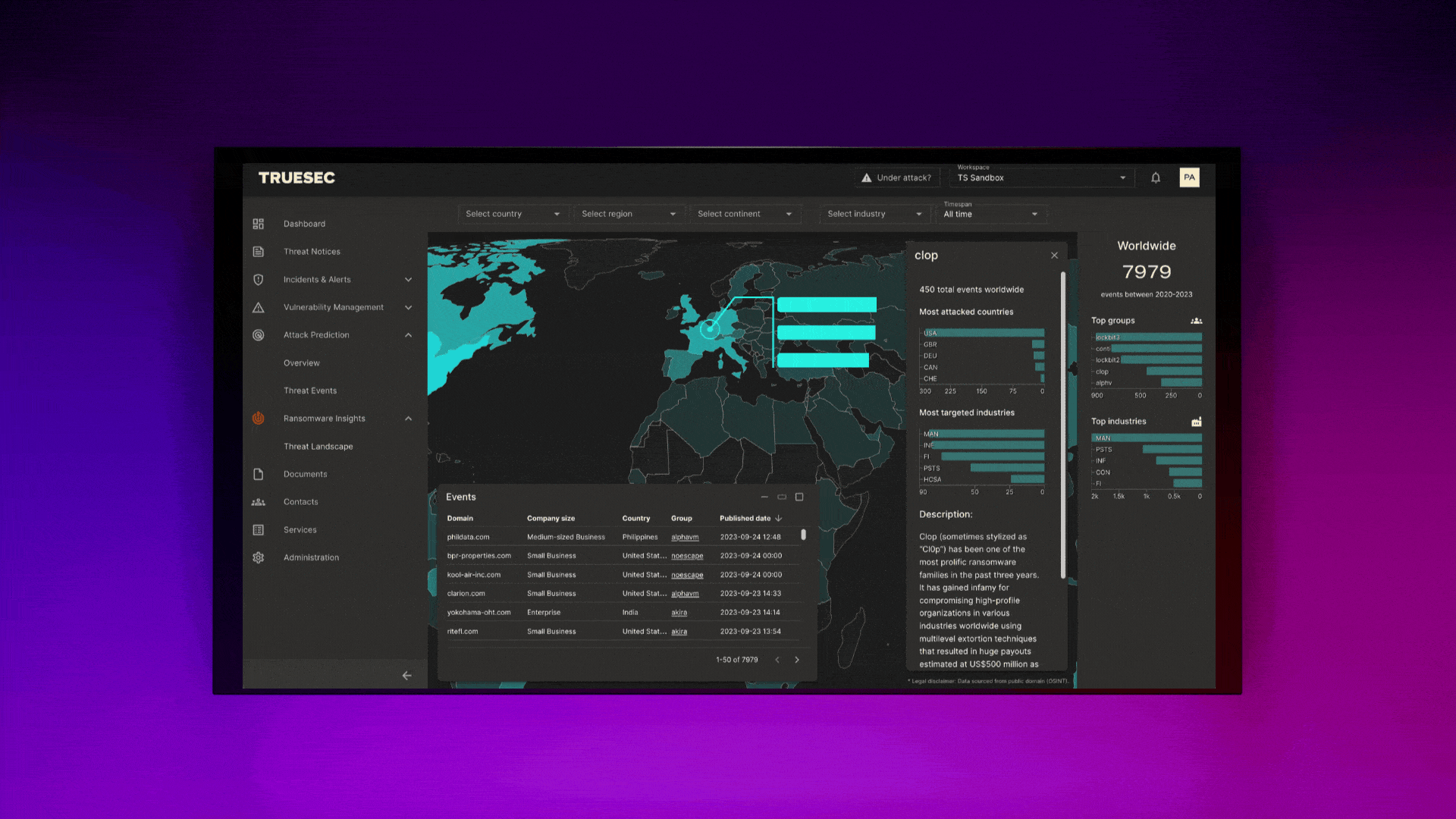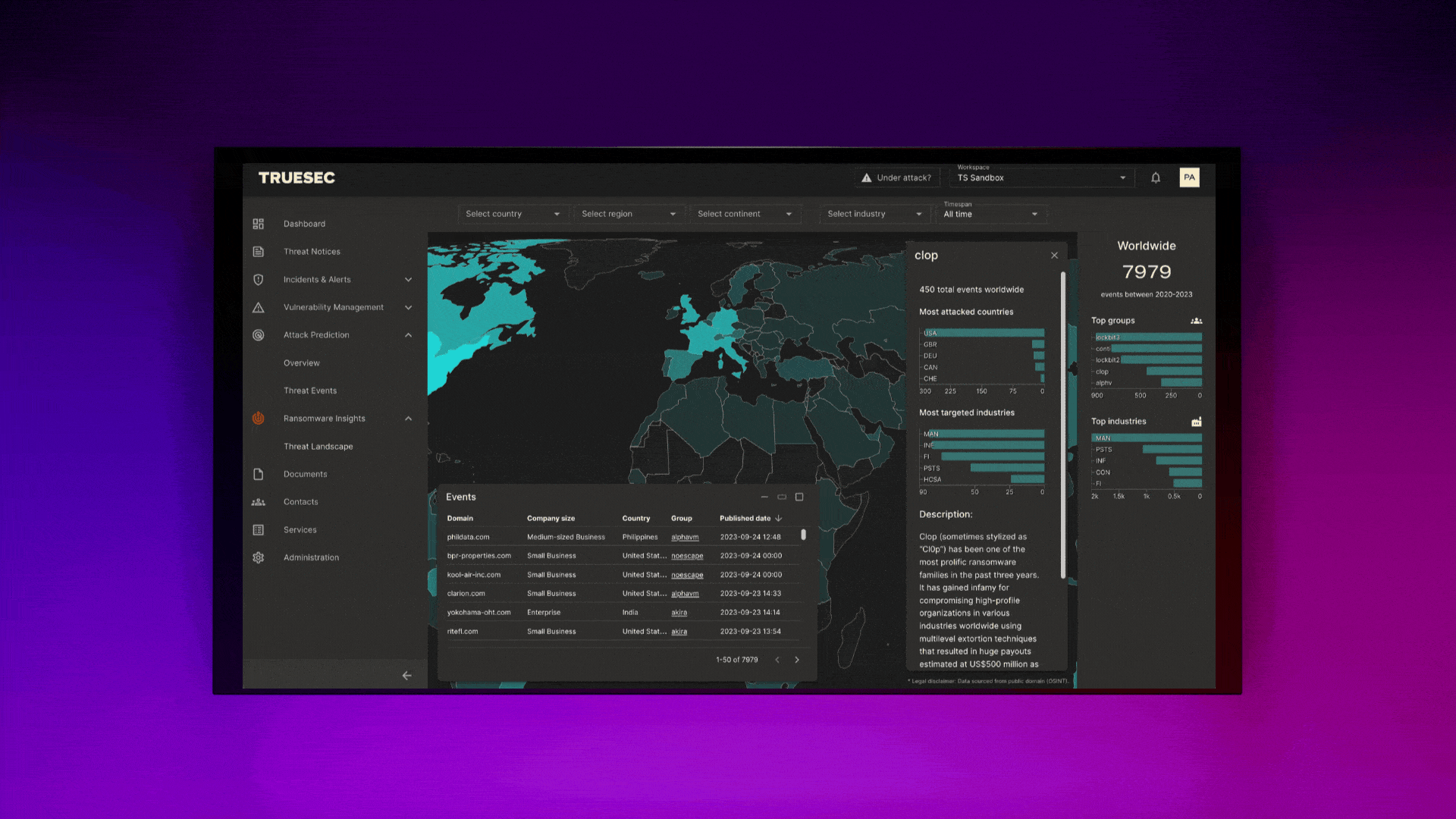
How Reporting Is Done at Truesec
At Truesec, we use the Truesec Cybersecurity Platform and the customer portal that’s included there. It offers a user-friendly interface for monitoring security status, viewing detailed reports, and receiving actionable insights. This portal simplifies the complex process of cybersecurity management, making it accessible and manageable for users.
Future Trends in MDR
Future trends in MDR indicate a significant shift towards more extensive detection capabilities on cloud platforms, including platform as a service (PaaS) and software as a service (SaaS). This evolution reflects the increasing adoption of cloud services and the need for enhanced security measures in these environments. It also highlights the ever-expanding ecosystem of PaaS and SaaS services and how organizations are using them.
The focus is on developing advanced detection mechanisms that can effectively identify and respond to threats within these cloud-based platforms, ensuring comprehensive security coverage in the evolving digital landscape.
Summary and Best Practices in MDR Implementation
In summary, best practices in managed detection and response (MDR) implementation involve a comprehensive approach that includes advanced threat detection, rapid response strategies, and continuous monitoring and analysis. Utilizing cutting-edge technology in conjunction with human expertise ensures a robust defense against cyber threats. It’s crucial to tailor MDR services to specific organizational needs and to stay adaptable to the evolving cybersecurity landscape. Effective MDR implementation also requires aligning with legal and regulatory requirements and considering future trends like increased cloud platform detections.
For most organizations, the best way to quickly establish a detection and response capability is to start with monitoring endpoints, identities, and critical data. This approach focuses on protecting the most vital elements of an IT environment, ensuring that the core aspects where threats are most likely to occur are under vigilant surveillance. It’s about securing the main entry points and valuable assets, effectively setting a strong foundation for a comprehensive MDR strategy.
Born-in-the-cloud organizations should start with monitoring identities, cloud platforms, and cloud software. This approach ensures that the key components of their cloud-centric infrastructure are safeguarded, addressing unique vulnerabilities and threats prevalent in cloud environments.
Manufacturing and organizations with operational technologies (OT), such as energy companies and water and facilities organizations, often need to secure both the IT environment and the OT environment. This means that a good approach is to deploy monitoring on endpoints, identities, and critical data and also add monitoring in the OT networks.
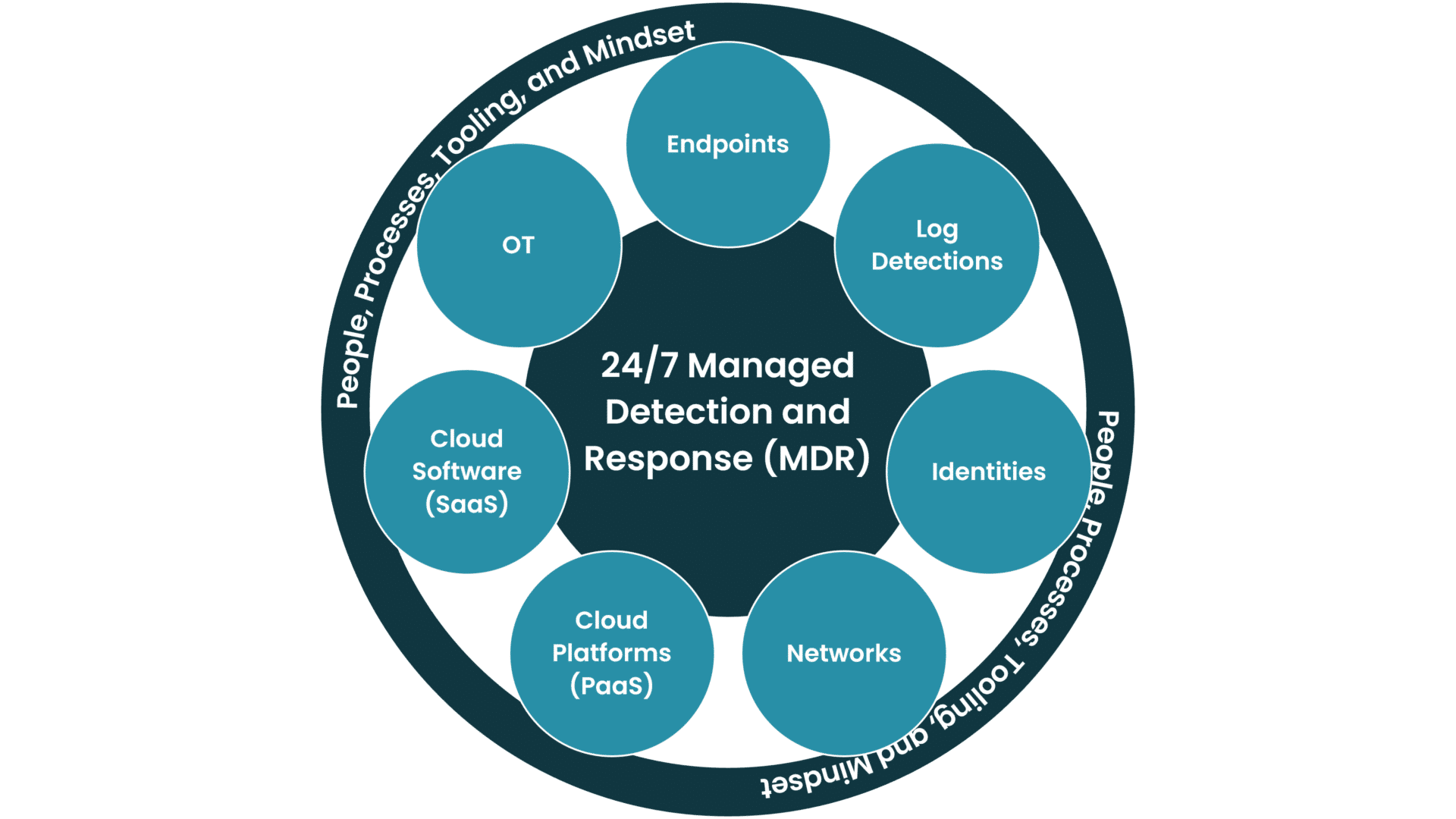
The Modules of Truesec MDR

24/7 Managed Detection and Response + People, Processes, Tooling, and Mindset
The core of our 24/7 SOC services is Truesec Endpoint Detection and Response, managed security monitoring with state-of-the-art capability to detect malicious threat actor activities. The service offers 24/7/365 monitoring, detection, analysis, and real-time response. The service also includes threat intel, threat hunting, a standby incident response SLA, and a dedicated cyber hotline.
MDR on Endpoints (Endpoint Detection and Response – EDR)
For most organizations, endpoint detection and response (EDR) is the central part of the service. EDR is a cybersecurity solution providing continuous monitoring, evaluation, analysis, and timely response to threats aimed at endpoints. Endpoints are managed devices connected to a network and include computers, laptops, servers, and smartphones.

Based on the multitude of incidents Truesec has responded to, nearly every cyber attack interacts with an endpoint at some point before a breach, making this detection approach highly effective. By monitoring and analyzing the activities on endpoints, we can detect and neutralize potential threat actors at an early stage.
In an increasingly digital world, EDR is vital for organizations seeking to enhance their security posture, prevent breaches, and safeguard their digital assets.
MDR With Log Detection (SIEM)
Over the years, the capabilities of SIEM have matured to become more than a log management, security information, and event management (SIEM) solution. Today, SIEM offers advanced user and entity analytics and is enabled to harness the power of AI. Understandably, SIEM has become a quintessential solution for many CISOs worldwide.
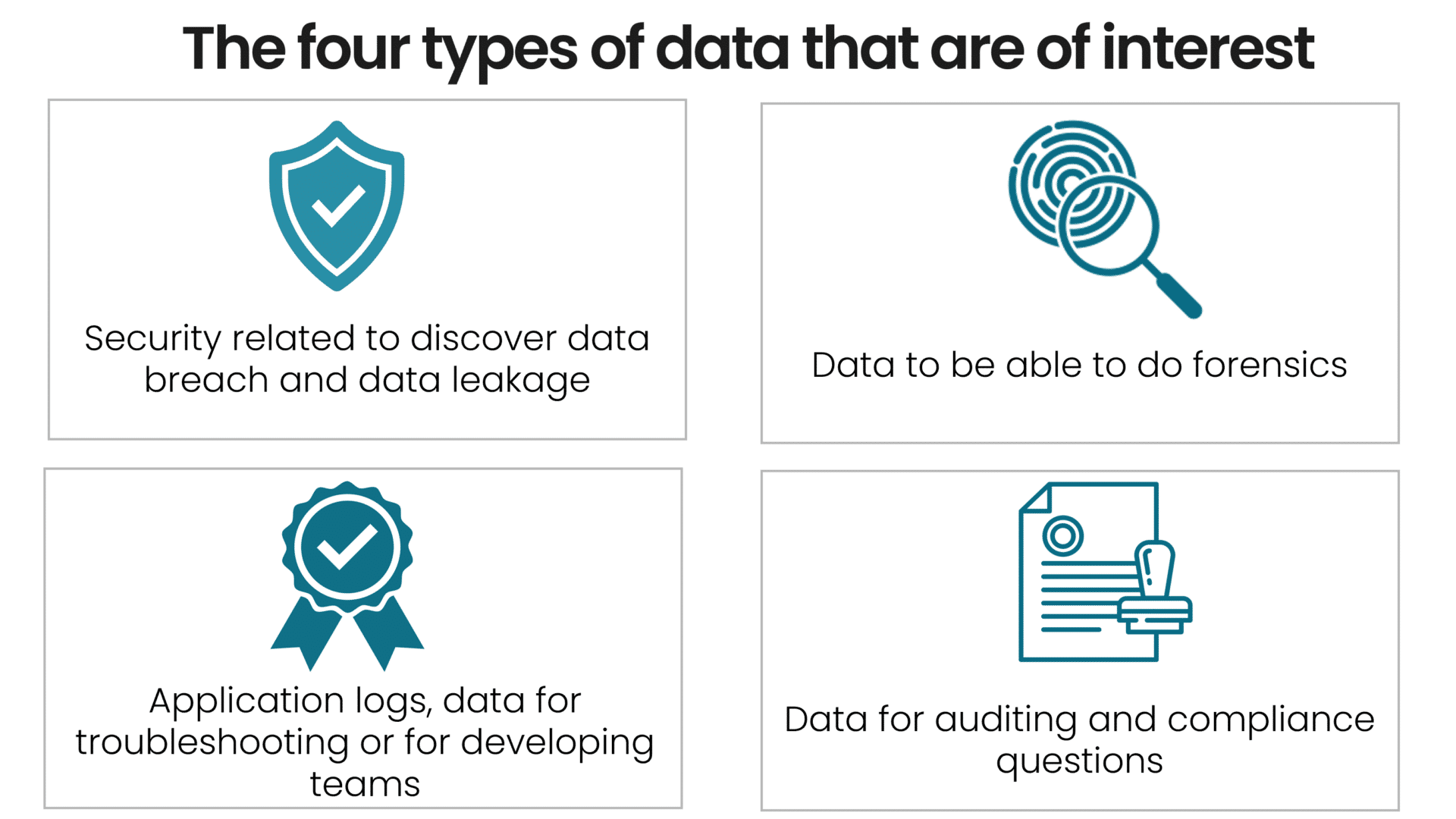
Truesec’s primary focus is to prevent cybercrime, so we concentrate on helping our clients detect and prevent attacks in real time, 24/7, from our SOC. Consequently, our focus for the capabilities in a SIEM solution is geared towards detection, response, and attack prevention. Notably, a SIEM is an excellent tool for incident response (IR), conducting forensic investigations, quality monitoring and troubleshooting, and auditing and compliance requirements.
MDR for Identities (IDR)
Reconnaissance, compromised credentials, lateral movements, domain dominance, and suspicious activities. These are all things that need to be detected and analyzed if they occur in an IT environment to determine if there’s an imminent or ongoing attack on an organization.
Identities are an important protective security layer when using internal services in other providers’ data centers and cloud applications (SaaS). The old way of using a firewall for protection is long gone, especially when using cloud services and when the workforce can work from anywhere at any time.
Truesec provides continuous monitoring, threat detection, and response for your identities, whether on premises or in the cloud.
Few organizations can provide detection for all endpoints and applications, so there will almost always be blind spots. Complete coverage is difficult to achieve; however, identities are always used in some form, so having a detection capability on identities can increase your organization’s security posture.
By consistently and continually tracking and analyzing identity-related activities, we can effectively detect and neutralize potential threat actors.
In today’s digital landscape, leveraging identity detection and response is critical for organizations aiming to fortify their security infrastructure and protect their digital assets against sophisticated cyber threats.
MDR for Networks (NDR)
How are you supposed to detect a threat actor in an environment with limited visibility or, in some cases, even complete gaps in detection capability?
In today’s dynamic threat landscape, traditional security measures often fall short of effectively detecting and responding to advanced threats. At Truesec, we also see that most organizations have considerable equipment and devices that don’t permit the installation of monitoring agents (for example, machines, computers connected to medical instruments, etc.)
Segmenting environments is an excellent first step, but we all know that systems and devices are becoming increasingly connected. This effectively opens the previously perfectly segmented environment, thereby giving the attackers holes and attack surfaces to exploit.
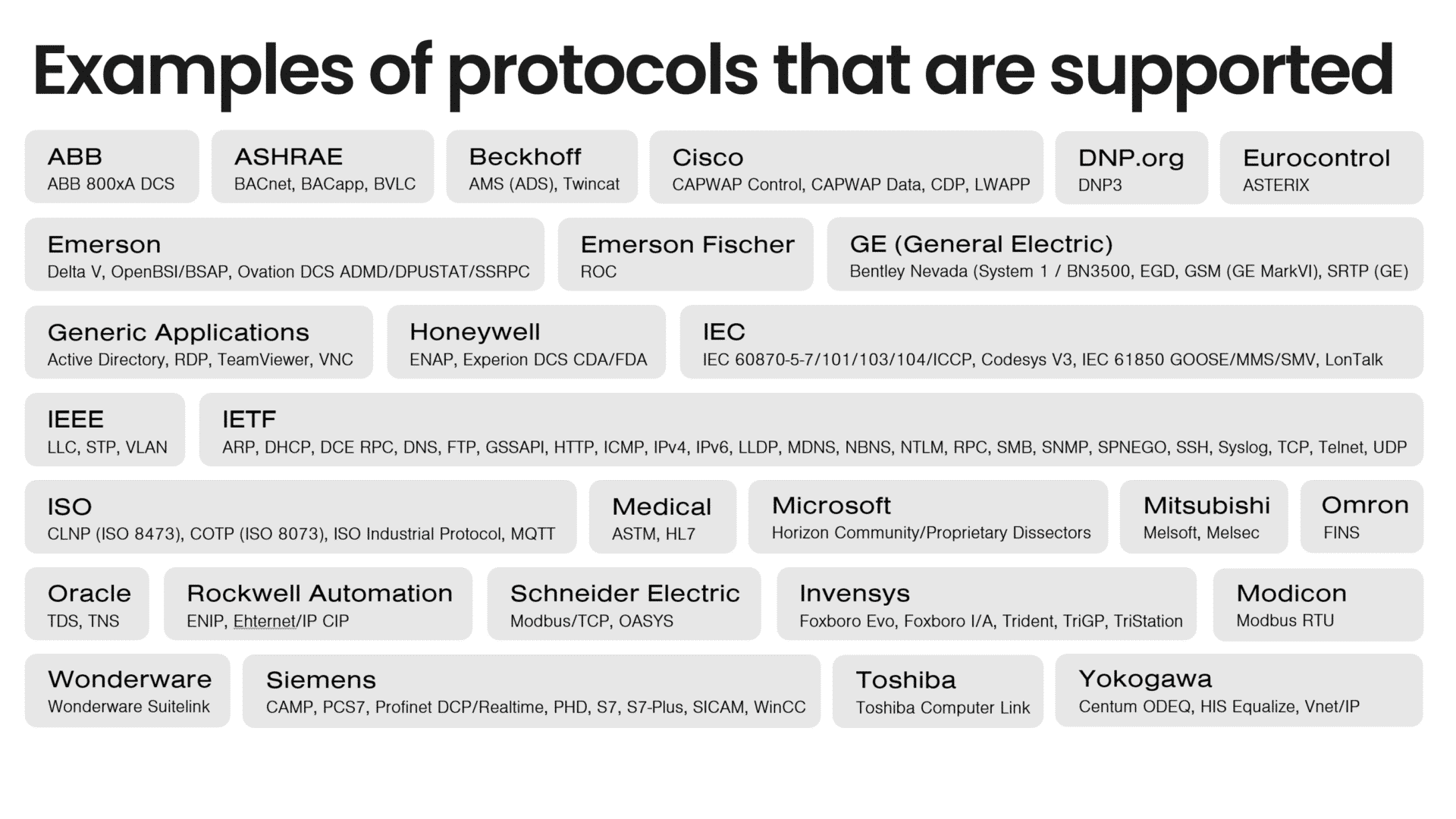
Network detection and response (NDR) provides real-time monitoring and rapid response capabilities. NDR powers Truesec’s Managed Detection and Response (MDR) service and offers advanced threat detection capabilities by leveraging machine learning, behavioral analysis, and anomaly detection techniques. It goes beyond traditional security measures to identify known and unknown threats, indicators of compromise (IoCs), and suspicious behaviors that may bypass standard defenses. This is achieved by understanding the protocols, network communications, and traffic patterns and having a team of cybersecurity specialists with in-depth experience and a mindset geared toward investigating events and incidents from our extensive incident response investigations.
MDR for Cloud Platforms (Paas)
In today’s highly competitive landscape, organizations are racing to innovate, develop, and deploy applications more quickly and efficiently than ever before. A key facilitator of this rapid development is the adoption of platform-as-a-service (PaaS) solutions. These platforms offer agility, cost-efficiency, and scalability; however, they also introduce a host of complex security challenges that traditional security measures often fail to address adequately.
With the accelerated adoption of PaaS solutions, your development teams may be churning out new applications and services at an unprecedented rate. While this velocity is beneficial for business, it opens the door for a myriad of security vulnerabilities that are intricate and continuously evolving. Traditional security systems may not provide the granularity required to secure PaaS environments, and internal IT teams often lack the specialized skills to monitor these services continuously. The result is an increased risk of data breaches, compromised applications, and, ultimately, reputational damage.
Given the unique challenges of securing PaaS environments, a specialized approach is not only preferable but essential. That’s where managed detection and response (MDR) services come in.
By leveraging an MDR service designed explicitly for PaaS, you can securely arm yourself with the tools and expertise necessary to manage your rapidly evolving application landscape. This focused approach to security allows you to keep pace with the demands of modern business, ensuring that innovation remains at the forefront – without leaving your organization vulnerable.
MDR for Cloud Software (SaaS)
In this era of digital transformation, SaaS applications have become a cornerstone for many organizations, driving efficiency and providing innovative solutions.
Yet, this digital immersion introduces a myriad of security challenges. The responsibility of safeguarding these digital assets and ensuring uninterrupted operations is paramount.
Our Managed Detection and Response (MDR) service is tailored for SaaS environments, addressing their unique security challenges. At its core, our service harnesses cutting-edge analytics engines, offering visibility into user activity and sensitive data spanning multiple SaaS platforms. Rapid detection of anomalous behaviors and potential security breaches ensures that experts can respond, mitigating risks and minimizing potential damage.
But our approach is more than just detection and response. We provide a holistic solution that integrates seamlessly with your organization’s existing infrastructure, delivering comprehensive oversight and actionable insights. In an age where cyber threats are constantly evolving, our MDR service ensures that your SaaS ecosystem remains fortified against both present and emerging threats. Trust in our expertise to manage the complexities of security, enabling you to confidently spearhead your organization’s digital journey.
MDR for Operational Technology (OT)
OT environments are increasingly facing business risks from a cyber perspective while presenting constraints that are different from IT.
Critical physical processes must stay up at all times – only a solution that doesn’t interfere with the environment is viable. Having the resources to put the data to use is essential, as OT security expertise is hard to find, and budgets are limited.
Building on best-of-breed network monitoring technology and deep expertise in SOC (Security Operations Center) services from Truesec, the solution uses agentless sensor capabilities to bring full visibility into assets and risks in OT environments and enable real-time threat monitoring. Core functionality includes:
- 24/7/365 coverage by OT SOC experts.
- Agentless zero-impact detection with industrial protocol-aware monitoring (NDR).
- Continuous asset discovery, network mapping, and vulnerability inventory.
FAQ
EDR (endpoint detection and response) is a technology focused on securing endpoints from threats. MDR (managed detection and response) is a service that employs EDR and other tools and adds expert human analysis to manage and respond to threats.
MDR works by continuously monitoring an organization’s network, analyzing threats, and responding to incidents. It combines technology with human expertise for proactive threat detection and response.
Companies need MDR to protect against sophisticated cyber threats, ensure compliance, and provide expert response to incidents, which is often beyond the capacity of in-house IT teams.
MDR enhances cybersecurity by offering proactive, continuous monitoring and expert response to threats, thereby reducing the risk of data breaches and cyber attacks.
Components include threat detection, response strategies, continuous monitoring, advanced technology, and human expertise.
MDR is a service that provides managed threat detection and response, while SOC (Security Operations Center) is a team or facility that houses an organization’s information security team.
Challenges include integrating MDR with existing IT infrastructure, managing false positives, and keeping up with evolving cyber threats.
MDR is needed to effectively address complex and evolving cyber threats, providing organizations with expertise and resources they may lack internally.
Managed detection and response is a comprehensive cybersecurity service that combines technology and human expertise to detect, analyze, and respond to cyber threats.