
Monitoring by cybersecurity experts

Full potential with data, development, and insights
Detect and manage cyber threats 24/7. We ensure your data and operations stay secure by applying real-time monitoring and rapid action against threats.

Monitoring by cybersecurity experts
By cybersecurity experts.
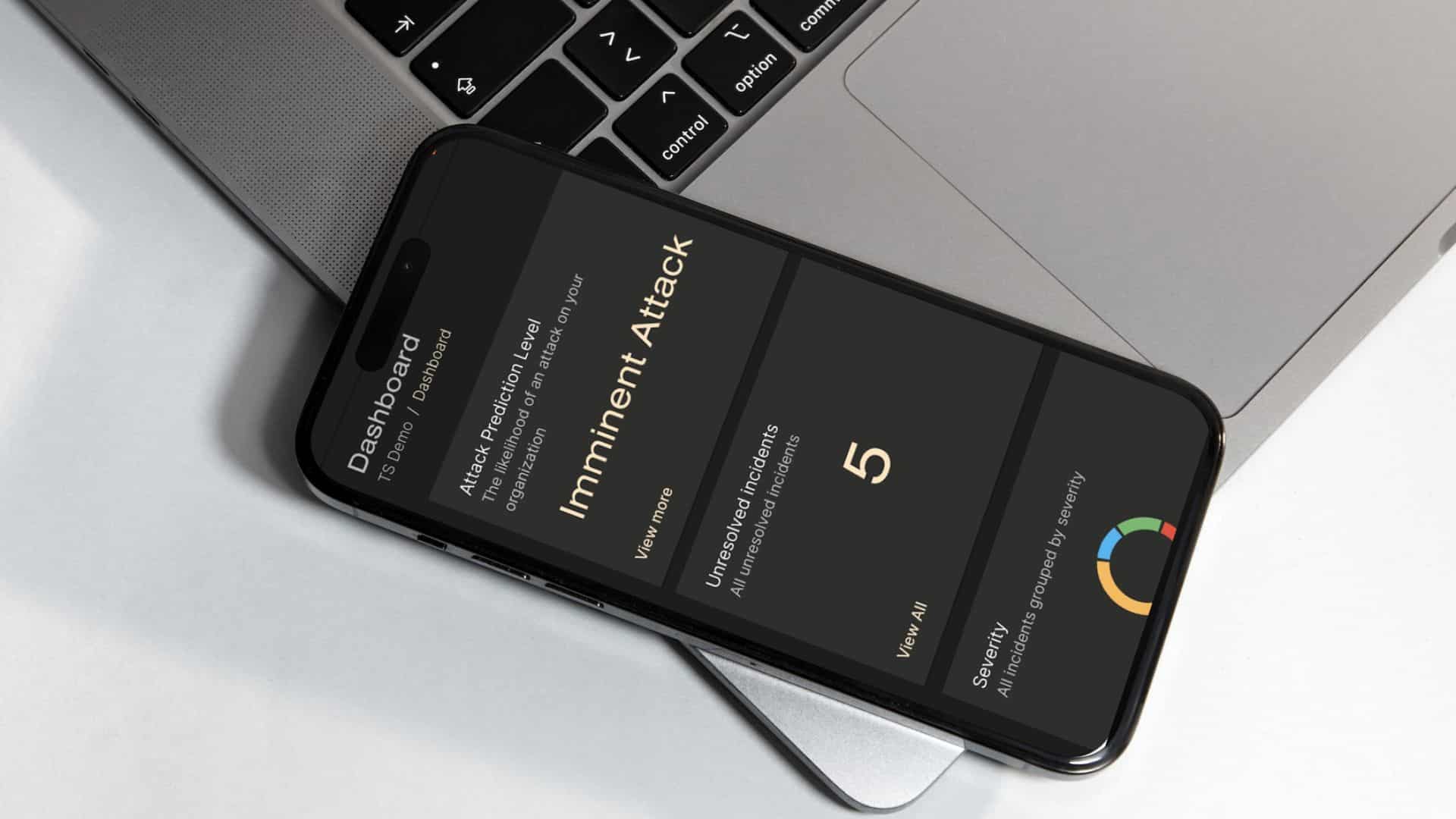
Get easy access to the consolidated view of all the security-enhancing services the Truesec Cybersecurity Platform provides.
We share cyber specialists across customers.
Full potential with data, development, and insights.
Truesec MDR
01
Consult our MDR experts to assess your cybersecurity setup, fill gaps, and create a custom security plan.
02
Review, approve, and seamlessly deploy the MDR platform onto your existing infrastructure.
03
Collaborate with our team to customize and configure the MDR service in alignment with your organizational policies and security requirements, ensuring the service is fine-tuned to provide optimal protection.
04
Join training sessions for our platform and collaboration process. Transition to the go-live phase, where our continuous monitoring and response services kick in to provide real-time cybersecurity defense.
05
Our experienced cyber team will guide you through our governance model, helping strengthen your cyber defenses and navigate your strategic cyber journey. Trust us to be your strategic cyber partner.
Truesec MDR
Truesec MDR
We currently discover maybe 10-20 times more threats than before.
Get answers to your questions
MDR is a comprehensive cybersecurity service that provides continuous monitoring, expert threat detection, and rapid response to secure your organization’s digital infrastructure. It focuses on protecting critical endpoints, servers, and client systems from cyber threats.

Our service is ideal for businesses that require robust cybersecurity but may not have the resources or expertise to manage an in-house Security Operations Center (SOC). MDR is suitable for organizations seeking enterprise-level security solutions that are both effective and cost-efficient.

MDR is not just a preventative tool; it’s a comprehensive solution. It includes 24/7 monitoring, advanced threat detection, proactive threat hunting, and response on true positives, all managed by our team of cybersecurity experts. This approach goes beyond traditional, passive defenses to offer active, continuous protection against cyber threats.

MDR is equipped to handle a wide range of cyber threats, including malware, ransomware, phishing attacks, and advanced persistent threats (APTs). Our service is continuously updated to respond to the latest cyber threats.

Absolutely. MDR assists organizations in meeting various industry-specific regulations related to data protection and privacy. Our service includes compliance-ready reporting and incident response capabilities.

Integration is streamlined and non-disruptive. Implementation is usually done in a few hours.

Pricing for MDR is based on a fixed fee model, calculated on the number of endpoints (client computers + servers) in your organization. This approach makes understanding and managing costs easy without worrying about data log volumes or retention times.

Post-implementation, you will receive continuous support from our team, including the possibility to book a meeting with us to discuss questions or concerns, seek advice, or request additional services. Our support is not limited to reactive measures; we proactively engage with you to ensure that the MDR service continuously aligns with your evolving security needs and business objectives. In addition to direct support, you will have access to the Truesec Cybersecurity Platform. This online platform is a vital resource for managing your cybersecurity services with us.

To begin, contact us at hello@truesec.com for an in-depth consultation. Our team will guide you through the onboarding process, ensuring a smooth and efficient transition to our MDR service.

Reach out to us for an initial consultation to discuss your concerns, objectives, and existing cybersecurity framework. Together, we’ll lay the groundwork for a tailored Cyber Resilience Program implementation suited to your organization’s needs.

In this workflow, we initiate a forensic investigation to secure traces of the threat actor, determine if any company or personal data has been breached or exfiltrated, and determine what the threat actor has done within the environment. This determines in exact detail how the threat actor breached the system. We also conduct threat intelligence on the attackers by analyzing the dark web and locating other relevant leaked information.











